📡 Cybersecurity Innovation Pulse #31: SSH Terrapin Attack Deep Dive; OpenAI's Preparedness Framework; Scary Fast Vuln. TTE; and More!
Covering Dec. 14th - Dec. 21st
Welcome to Issue 31 of the Cybersecurity Innovation Pulse! I'm Darwin Salazar, Product Manager at Monad and a former detection engineer. Each week, I distill the latest and most exciting developments + trends in cybersecurity innovation into digestible, bite-sized updates. If you’re serious about staying at the forefront of the latest in the cybersecurity industry, make sure to hit the “Subscribe” button below to get my insights delivered straight to your inbox 📩 🚀
Industry🛰️
Assessing and Mitigating the Terrapin Attack on SSH
The recently discovered Terrapin attack (CVE-2023-48795 - Not yet scored) which targets a vulnerability in OpenSSH, manipulates sequence numbers during the handshake process to compromise SSH channel integrity. It exploits vulnerabilities in the SSH transport layer protocol, especially when using encryption modes like ChaCha20-Poly1305 or CBC with Encrypt-then-MAC. This method results in truncated negotiation messages, reducing the security of SSH connections without detection.
To exploit this vuln, the attacker must be sitting between the client and server (Man-in-the-Middle) to intercept the handshake which makes it more feasible on local networks.
“Our scan indicated that at least 77% of SSH servers on the internet supported at least one mode that can be exploited in practice.” - Ruhr-Universität Bochum Researchers
Mitigation strategies include implementing strict key exchange in the SSH protocol and temporarily disabling affected algorithms for both client and server. Additionally, using the Terrapin vulnerability scanner available on GitHub can help identify vulnerabilities in SSH implementations. Given the widespread usage of OpenSSH and the affected encryption modes, this is a fairly realistic threat in my opinion.
Sources:
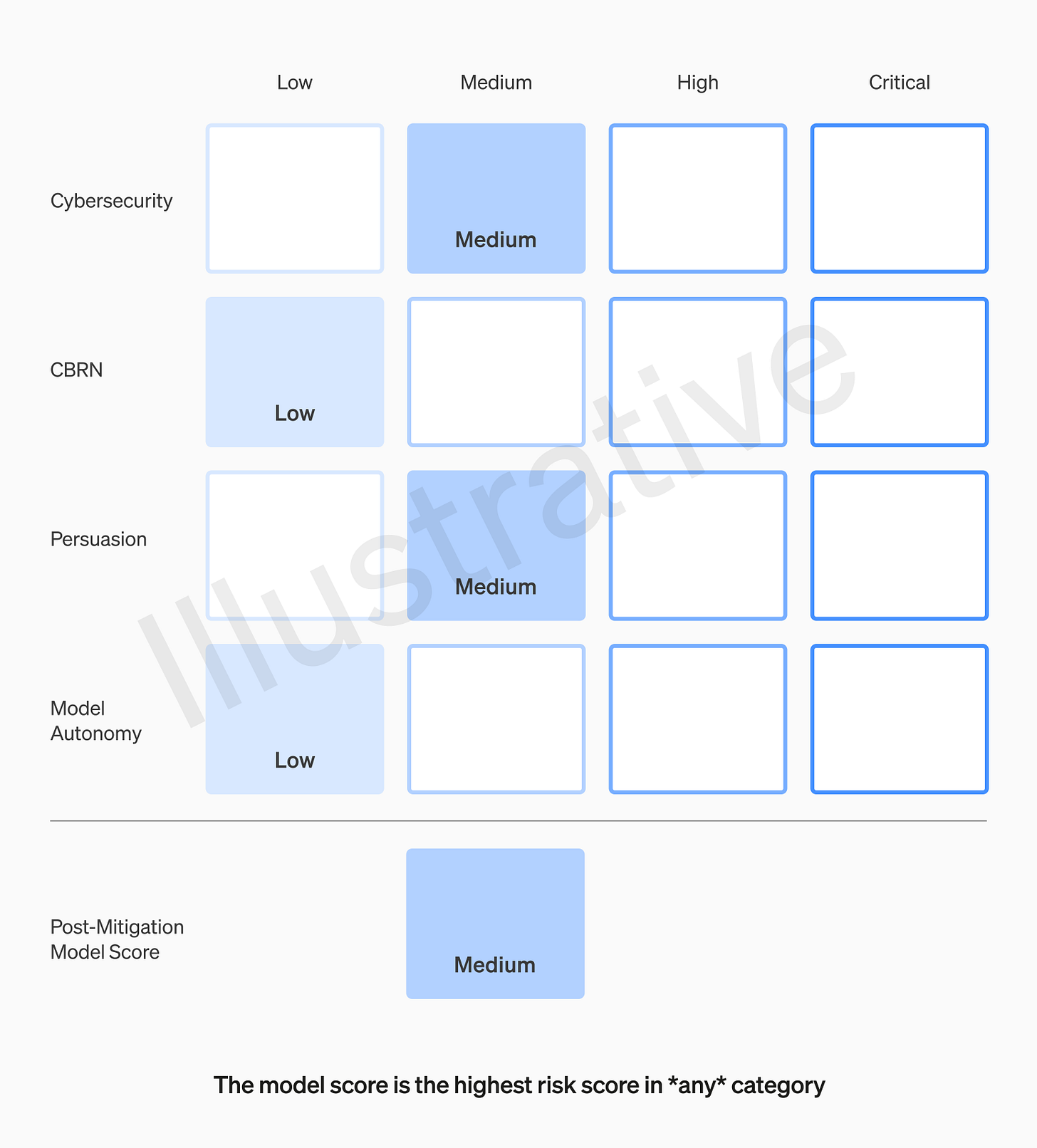
New OpenAI Safety Initiative: A Framework to Mitigate Catastrophic AI Risks
OpenAI has introduced a safety initiative, including a Preparedness Framework, to mitigate risks in AI development. This plan grants the company's board of directors the power to veto high-risk AI projects, surpassing even the CEO's authority. The framework focuses on systematically addressing potential catastrophic risks from advanced AI models, ensuring responsible and safe development.
“…the Preparedness Team will access frontier models, and a “superalignment” team will watch over the development of “superintelligent” models, all of which will report to the board.” - James Farrell, SiliconAngle
The framework evaluates AI models across four risk domains:
Cybersecurity
Persuasion
Model autonomy
Chemical, Biological, Radiological, and Nuclear (CBRN) threats
The Preparedness team will determine the course of development based on continuous risk assessments. One of which you can see down below. Additionally, a new safety advisory group will provide recommendations to OpenAI's leadership, with the board retaining final approval on AI model releases.
Pretty interesting that this initiative is coming out nearly a month after all of the OpenAI Board drama… I wonder if they saw something that spooked them👀
Sources:
Bugcrowd's Vulnerability Ratings for Large Language Models (LLMs)
Bugcrowd has recently updated its Vulnerability Rating Taxonomy (VRT) to include vulnerabilities in LLMs aiming to standardize the reporting of vulnerabilities submitted by researchers. Official release down below!
Sources: Bugcrowd
1 in 4 High-Risk CVEs are Exploited Within 24 Hours of Going Public
A recent Qualys study found that 25% of high-risk vulnerabilities identified in CVEs are exploited within 24 hours of being made public. Talk about a short time window to react lol…
The most impacted areas are network devices and web applications, with attackers frequently using tactics like exploiting remote services and privilege escalation. Other key findings from the report:
Less than 1% of vulnerabilities contributed to the highest risk and were routinely exploited in the wild.
One-third of high-risk vulnerabilities impacted network devices and web applications.
The top three MITRE ATT&CK tactics included the following: exploitation of remote services and public-facing applications; and exploitation for privilege escalation.
Source: SC Media
Product🛸
Okta Acquires Security Firm Spera
Okta, has agreed to acquire Spera for approx. $100-130 million. Spera is an Identity Security Posture Management (ISPM) startup whose coming out of stealth ($10M seed from YL) announcement we covered in TCP #7. Obviously, Okta hasn’t had the best year but this acquisition is a great move to bolster their cloud identity security coverage. Cheers to Dor and the Spera team on a quick and successful exit!
Source: TechCrunch
Halcyon Raises $40M Series B
Halcyon, an Austin-based anti-ransomware company, raised $40 million in a Series B funding round led by Bain Capital Ventures, bringing its total raised in the year to $90 million.
Halcyon leverages AI models and a lightweight agent to provide multi-layered security against ransomware. Their tech includes features like automated encryption key capture and autonomous decryption to restore infected devices.
Halcyon said it leverages the capsule neural network (CapsNet) machine learning system to quickly train, test and deploy protection mechanisms aimed at new techniques leveraged in ransomware attacks. - Eduard Kovacs, SecurityWeek
CapsNet… Will be digging into this one over the holiday break!
Source: SecurityWeek
Cisco Acquires Isovalent
One last acquisition to close out the year for Cisco. Isovalent is known for its contributions to the open-source community, particularly for eBPF, and for leading the development of Cilium, a top cloud-native networking and security solution. Term$ of the deal undisclosed.
Source: Cisco
Tradecraft🤺
Abusing GitHub for Malware Distro
Researchers from ReversingLabs have noticed a spike in attacks leveraging GitHub features including secret Gists and git commit messages. By embedding Base64-encoded commands in these GitHub elements and embedding them in fake Python packages, attackers manage to blend malicious network traffic with legitimate traffic making it much harder to detect this activity.
ReversingLabs said it identified several PyPI packages – namely, httprequesthub, pyhttpproxifier, libsock, libproxy, and libsocks5 – that masqueraded as libraries for handling network proxying, but contained a Base64-encoded URL pointing to a secret gist hosted in a throwaway GitHub account without any public-facing projects. - The Hacker News
Source: The Hacker News
Bye For Now!
That's all for this week! I’ll be back with one more issue to look back on 2023 and wrap up the year. Cheers and hope y’all are enjoying some downtime with your loved ones! 🎄