📡 Cybersecurity Innovation Pulse #33: Open-source Voice Cloning; NIST Adversarial ML Report; Hadoop+Flink Attacks; OWASP AI Exchange; M&A Galore and More!
Covering Jan. 1st - Jan. 11th
Welcome to Issue 33 of the Cybersecurity Innovation Pulse! I'm Darwin Salazar, Product Manager at Monad and a former Detection Engineer. Each week, I distill the latest and most exciting developments + trends in cybersecurity innovation into digestible, bite-sized updates. If you’re serious about staying at the forefront of the latest in the cybersecurity industry, make sure to hit the “Subscribe” button below to get my insights delivered straight to your inbox every week 📩 🚀
Welcome to the first issue of the year! Lots to cover, but first wanted to say thank you for subscribing and joining me on this journey! We recently breached 2,000 subscribers which is a nice bit of fuel to kick off what will be another special year for TCP.
You’ll also notice that I’ve given the site a facelift. More to come! Now without further ado, let’s jump into things.
Industry🛰️
Cyber For Builders is Here!
Over the past few years, nobody has been more successful in cutting through the noise and delivering pinpointed, actionable insights in the security startup and product world than my dear friendRoss Haleliuk from Venture in Security. That said, his much anticipated “Cyber For Builders” book is here and I can’t wait to dig into it this weekend. You can grab yourself a digital or hard copy here. You should probably also subscribe to his Substack. Trust me, you will not be disappointed.
New NIST Report on Adversarial ML💣
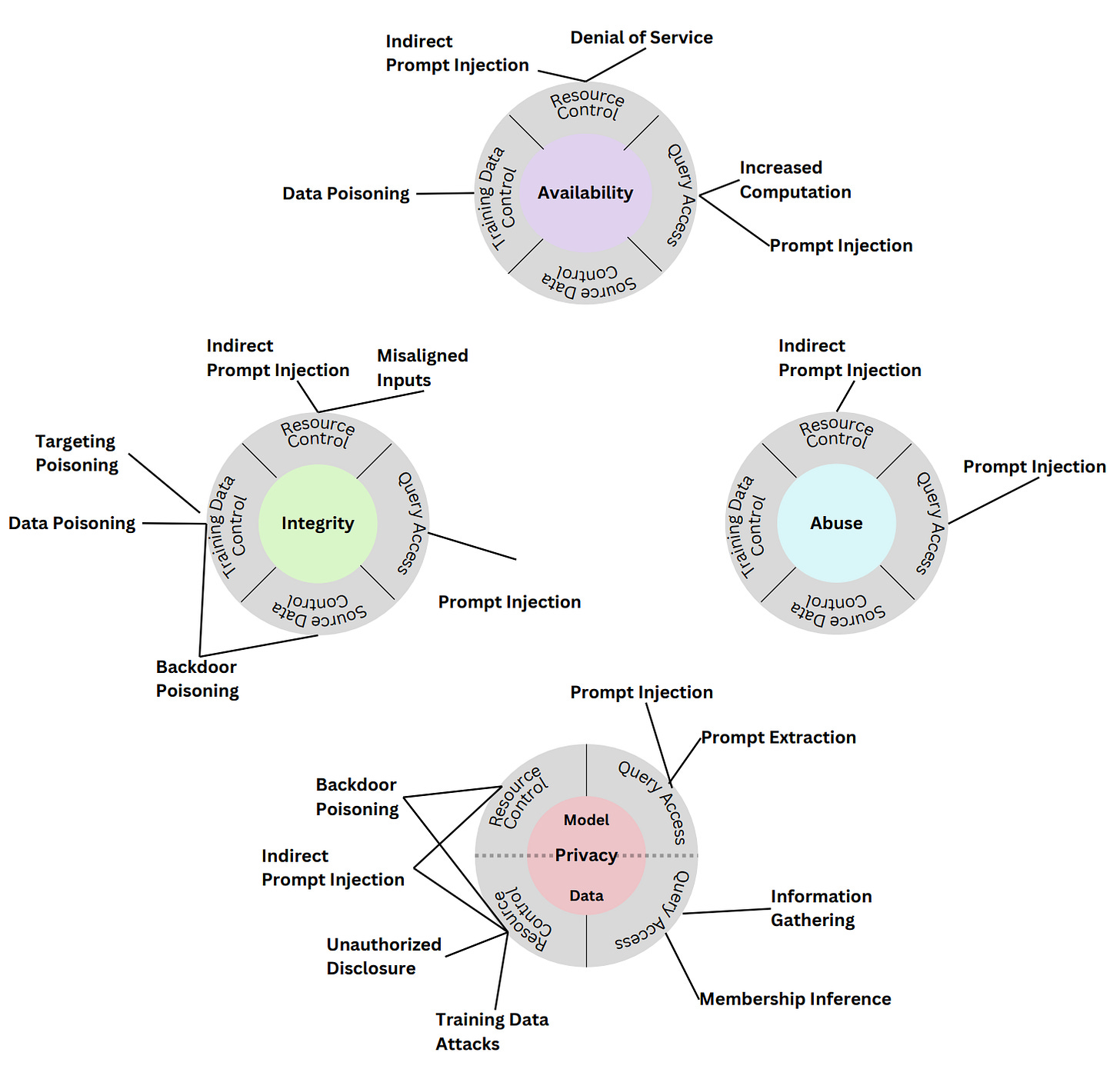
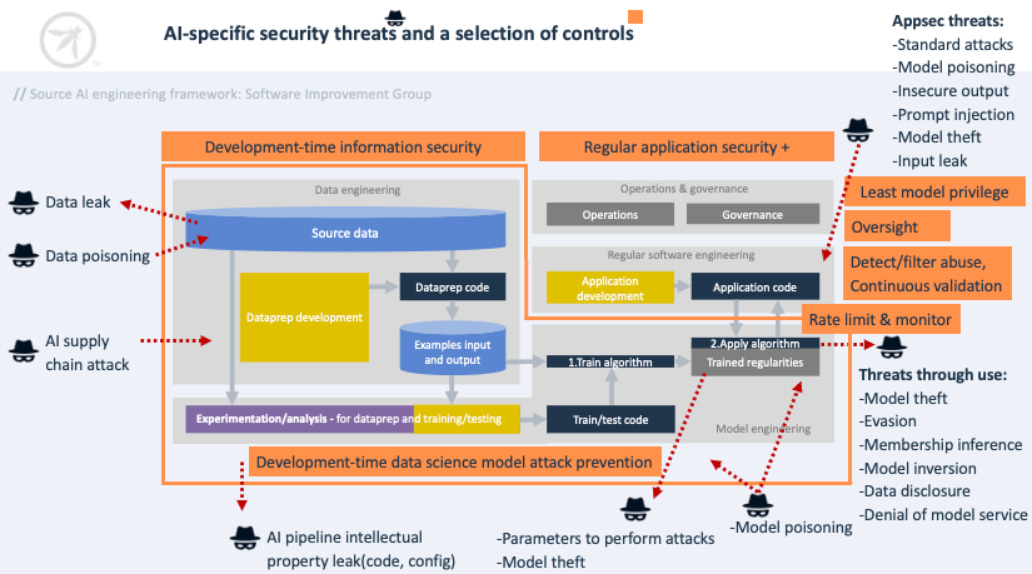
NIST recently released a 106-page report (NIST.AI 100-2) that explores critical security + privacy threats and mitigations to consider during the AI application development lifecycle. In my time writing this newsletter and covering AI security, this is the most robust and practical AI security guidance that I’ve come across. A must-read, imo.
The doc categorizes 4 main types of attacks that can compromise AI systems, including:
Evasion attacks
Poisoning attacks
Privacy attacks
Abuse attacks
The doc also goes in-depth on AI supply chain and direct+indirect prompt injection attacks+mitigations.
Report: NIST
Tl;dr: SecurityWeek
Open-source AI Voice Cloning 🙃
MyShell recently open-sourced their scary good AI voice cloning model, OpenVoice. The model requires only a short audio sample from the target speaker to mimic their unique vocal tone and speech characteristics across multiple languages.
What can possibly go wrong?
Source: VentureBeat
Free+Virtual CSA AI Summit on Jan. 17th
Stacked speaker lineup of folks at the forefront of AI security. Worth attending if you have the time! Register here.
OWASP AI Exchange
OWASP recently opened up their AI Exchange to the world which is an open-source collaborative resource to aid in advancing AI security standards and regulations. This write-up by Chris Hughesfrom Resilient Cyber does a fantastic job of detailing its significance and how it can be used in practice. Check out his interview with Rob van der Veer, one of the leaders of the OWASP AI Exchange on this podcast episode.
Source: Resilient Cyber
Guidance on New SEC Reporting Requirements
“If the registrant experiences a cybersecurity incident that is determined by the registrant to be material, describe the material aspects of the nature, scope, and timing of the incident, and the material impact or reasonably likely material impact on the registrant, including its financial condition and results of operations.” - Neil Carpenter, Orca Security
With the recent SEC incident reporting requirements going into effect, many are still dazed and confused, including me. What does “material impact” even mean in this context? Much legalese, but how can CISO and security teams prepare themselves to comply with this new requirement?
This article by Neil Carpenter from Orca Security provides some great guidance on how companies can ready themselves to meet these reporting guidelines and stay out of the SEC’s crosshairs.
Source: Orca Security
Cybersecurity Workforce Trends in 2024
Tl;dr: We need more defenders and we’re not producing capable defenders at a high enough rate. This article dives into the trends+complexities of this challenge and how our industry can work to close the gap.
Source: Security Intelligence
Product🛸
Slow start to the year on the product announcement front, but we have seen a few key acquisitions that’ll help incumbents bolster their offerings:
SentinelOne To Acquire PingSafe
SentinelOne to acquire for over >$100M. PingSafe is a pure-play CNAPP product. You can dig into PingSafe’s features here.
Great pickup at a good price by S1. Hopefully they integrate it well :)
Source: SentinelOne
Mimecast To Acquire Elevate Security
Mimecast, to acquire Elevate Security. Elevate is a startup specializing in human risk management. Timely and synergistic pickup by Mimecast given their market position in the email security landscape.
Source: Cybersecurity Dive
SonicWall to Acquire Banyan Security
Two companies that I’m admittedly not very familiar with but a strong signal of continued consolidation in the security space. You can learn more about the deal here.
Source: Cybersecurity Dive
Choosing an AI-SPM Tool
Add another one to the “SPM” column! I guess AI-SPM is a thing now and the SPM product naming trend will never go away.
All jokes aside, this Wiz post does a great job of highlighting AI-SPM solution capabilities and highlighting critical questions security teams should be asking themselves such as:
Does my organization know what AI services and technologies are running in my environment?
Do I know the AI risks in my environment?
Can I prioritize the critical AI risks?
Can I detect a misuse in my AI Pipelines?
Source: Wiz
Terraform fork OpenTofu Goes GA!
It’s been dope watching the software+infra+security communities rally to build OpenTofu. The GA release, v1.6, contains new features and tons of enhancements not present in Terraform.
Source: SiliconAngle
Tradecraft🤺
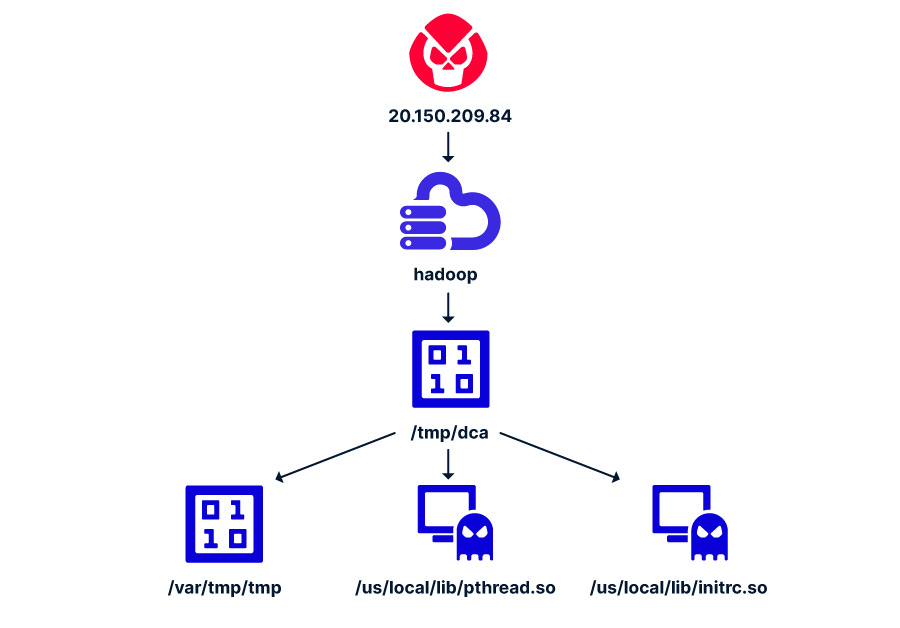
Apache Hadoop+Flink Being Targeted
The great research team at Aqua Security has observed pretty stealthy and advanced hackers dipping their hands in Apache Hadoop and Apache Flink which are popular big data processing frameworks. You can learn more about the attacker techniques, mitigations, and detection opportunities in Aqua’s report here.
Source: Aqua Security
Free Decryptor for Black Basta and Babuk's Tortilla Ransomware
Cisco Talos has released a free decryptor for Black Basta + the Tortilla🌮 variant of the Babuk ransomware.
Source: The Hacker News
Chat Services as a Vehicle for Malicious Purposes
The great Andy Giron from Datadog Security Labs has done some great work in understanding how malicious actors are leveraging chat platforms like Discord and Telegram for their communications and payload delivery. In this report, he details exactly how attackers are doing this and different indicators of compromise to look out for.
Source: Datadog Security Labs
Rare Data Transfer Tactic Observed in the Wild
Uptyc’s research team has observed that the folks behind the RemcosRAT (UNC-0050) tool are using an EDR-evading data transfer tactic using the “anonymous pipes” feature in Windows.
Source: Uptycs
Extras
AI is Changing Security - Palo Alto Networks