Intel Hub 🧠
Introduction
The Intel Hub is a centralized repository for cybersecurity-related research reports. Carefully curated from a diverse range of over 90 sources, including security vendors, cloud providers, venture capital firms, and non-profits, the hub streamlines access to crucial information on market and product trends, enterprise security developments, and the latest threats and threat actors. The hub is designed to support a wide range of stakeholders, from founders and c-suite executives to marketers, venture capitalists, and anyone interested in the cybersecurity field. These research reports are priceless because they provide an inside look into what trends and activities security vendors are seeing in the “trenches”. A perspective we wouldn’t have otherwise. This helps us all make better-informed decisions.
Most importantly, researchers, data scientists, and other experts work tirelessly to compile this invaluable research so it’s only right to continue highlighting their work. Before getting onto the reports, click the “Subscribe” button down below to become a member of The Cybersecurity Pulse community and receive my weekly newsletter!
Table of Contents 📚
Introduction
Reports
Conclusion
Reports
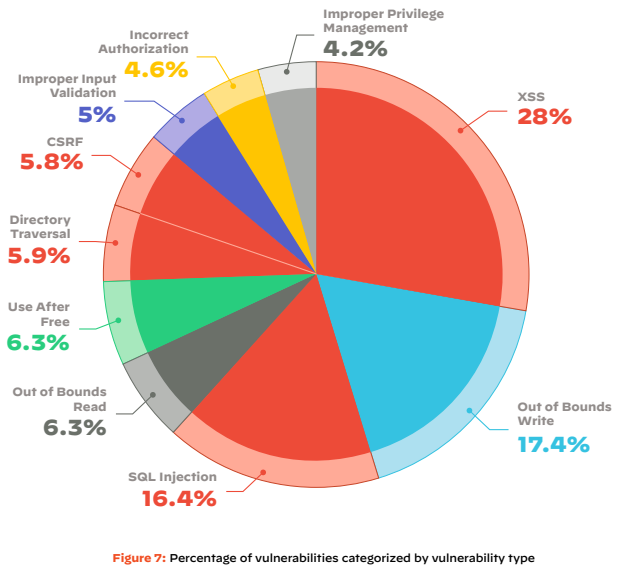
Cloud Security

Key Findings
35% of companies assessed have workloads across two cloud providers with 22% leveraging three cloud providers. - Wiz, State of the Cloud 2023
The average security team is responsible for 165,633 cyber assets, including 28,872 cloud hosts, 12,407 network interfaces, 55 applications per human employee, 59,971 data assets (including 3,027 secrets), and 35,018 user assets. - JupiterOne, State of Cyber Assets Report 2022
91.3% of code running in the enterprise is developed by a third party, meaning that modern organizations are incredibly vulnerable to supply chain attacks. - JupiterOne
Orphaned Assets are a Myth: While previously believed to be heavily isolated, users, networks, and devices are hardly ever on an island considering their rampant first-degree relationships to mission-critical data. - JupiterOne
87% of Container Images Have High-Risk Vulnerabilities - SysDig, Cloud-Native Security and Usage Report 2023
90% of granted permissions are not used. - SysDig
We [Aqua Security] detected thousands of exposed registries and artifact repositories containing over 250 million artifacts and over 65 thousand container images. - Aqua Security, Fortune 500 at Risk
In most organizations' cloud environments, 80% of the alerts are triggered by just 5% of security rules. - Palo Alto Networks, Unit 42 Cloud Threat Report, Volume 7: Navigating the Expanding Attack Surface
75% of organizations don’t enforce trail logs for Amazon Web Services (AWS) CloudTrail. 74% don’t enforce Microsoft Azure key vault audit logging. 81% don’t enforce Google Cloud Platform (GCP) Storage bucket logging. - Palo Alto Networks, Unit 42 Cloud Threat Report, Volume 7: Navigating the Expanding Attack Surface
Reports
Palo Alto Networks: State of Cloud-Native Security 2023
Google Cloud’s Cybersecurity Action Team (CAT): State of Cloud Threat Detection and Response Report 2023
JupiterOne: State of Cyber Assets Report 2022
Contrary Research: Taking the Fight to the Cloud
(ISC)2: Cloud Security Report 2022
Google Cloud’s CAT: Threat Horizons Report Jan. 2023
Fidelis: AWS Cloud Security Report 2022
ZScaler - Cloud (In)Security Report 2022
Aqua Security - Fortune 500 at Risk 2023 [New]
Palo Alto Networks, Unit 42: Cloud Threat Report, Volume 7: Navigating the Expanding Attack Surface [New]
Software Supply Chain Security
Key Findings
5.5 commits out of every 1,000 exposed at least one secret. (+50% YoY) - GitGuardian, State of Secrets Sprawl 2023
1.35M GitHub Authors accidentally exposed a secret in 2022. - GitGuardian, State of Secrets Sprawl 2023
Malicious NPM packages jumped by more than 40% in 2022. - ReversingLabs, The State of Software Supply Chain Security 2023
Over 70% of DevOps teams release code as frequently as once a day. - GitLab, Global DevSecOps Survey 2022
40% of respondents still don’t use key supply chain security technologies like SCA or SAST - Snyk, State of Open Source Security Report 2023
83% of the organizations have hardcoded credentials in their source control management systems. - Palo Alto Networks, Unit 42 Cloud Threat Report, Volume 7: Navigating the Expanding Attack Surface
Reports
GitGuardian: State of Secrets Sprawl 2023
GitLab: Global DevSecOps Survey 2022
SonaType: State of the Software Supply Chain 2023
VMWare Tanzu: The State of the Software Supply Chain: Open Source Edition 2022
ReversingLabs: The State of Software Supply Chain Security 2023
Snyk: State of Open Source Security Report 2023 [New]
Application Security
Key Findings
Holiday shopping sees a ~550% increase in API attacks. - Cequence, API Protection Report 2023
Only 3% of critical vulnerabilities are worth prioritizing. - Datadog, 2023 State of Application Security
Over 74% of applications have at least one security flaw found in the last scan over the last 12 months. - Veracode, State of Application Security 2023
30% of HTTP traffic is automated. Equivalent to about 13 million HTTP requests/second on the Cloudflare network. Down 8% during the same timespan in 2022. - Cloudflare, State of Application Security in 2023
Reports
Cloudflare: State of Application Security in 2023
Veracode: State of Application Security 2023
Datadog: State of Application Security 2023 [New]
Cequence: API Protection Report 2023 [New]
Identity and Access Management
Key Findings
Only 1% of permissions granted are actually used. - Microsoft, State of Cloud Permissions Risks 2023
73% of Organizations Don’t Enforce Multifactor Authentication for Console Users. - Palo Alto Networks, Unit 42 Cloud Threat Report, Volume 7: Navigating the Expanding Attack Surface
68% of non-human identities have access to sensitive data. - CyberArk, Identity Security Threat Landscape Report 2022
Dormant accounts represent 24.15% of the average company’s total accounts - Oort, State of Identity Security Report 2023
Machine identities outweigh human identities by a factor of over 45. - CyberArk, Identity Security Threat Landscape Report 2022
The average company has 40.26% of accounts with either no MFA or weak MFA -- Oort, State of Identity Security Report 2023
Reports
Microsoft - State of Cloud Permissions Risks 2023
Threat Landscape
Key Findings
There were 4,135 critical vulnerabilities (CVEs) reported in 2022, up 59% year over year. - Deepwatch, Annual Threat Report 2023
79% of security pros say they make decisions without threat intelligence. - Mandiant, Global Perspectives on Threat Intelligence 2023
62% of system intrusion incidents came through an organization’s partner - Verizon, Data Breach Investigations Report (DBIR) 2022
82% of breaches involved the Human Element, including Social Attacks, Errors, and Misuse. - Verizon, Data Breach Investigations Report (DBIR) 2022
Cloud exploitation grew by 95% in 2022 and "cloud-conscious" threat actors observed grew by 288%. - CrowdStrike, Global Threat Report 2023
The volume of password attacks has risen to an estimated 921 attacks every second – a 74% increase in just one year." - Microsoft, Digital Defense Report 2022
Reports
Microsoft: Digital Defense Report 2022
Accenture: Cyber Threat Intelligence Report 2022
CrowdStrike: Global Threat Report 2023
Sophos: Threat Report 2023
Tenable: Threat Landscape Report 2022
CheckPoint: Cybersecurity Report 2023
Splunk: State of Security 2022
SecureWorks: State of the Threat Report 2022
Red Canary: Threat Detection Report 2023
LATAM CISO x Duke University - LATAM CISO Report 2023 [New]
ZScaler ThreatLabz - The State of Encrypted Attacks 2022 [New]
SecurityIntelligence - Industry Threat Recap: Finance and Insurance 2022 [New]
Deepwatch: Annual Threat Report 2023 [New]
BlackBerry: Global Threat Intelligence Report - Aug. 2023 [New]
Mandiant: Global Perspectives on Threat Intelligence 2023 [New]
DevOps and Platform Engineering

Key Findings
65% of developers said that they are using AI/ML in testing efforts or will be in the next three years. - GitLab, Global DevSecOps Report: Security Without Sacrifices 2023
62% of developers using AI/ML use it to check code, up from 51% in 2022. - GitLab, Global DevSecOps Report: Security Without Sacrifices 2023
Over 50% of organizations operating in each cloud have adopted serverless - DataDog, State of Serverless Report 2022
Over 60% of large organizations have deployed Lambda functions in at least three languages - DataDog
Reports
DataDog: State of Serverless Report 2022
Google: State of DevOps 2022 Report
Contrary Research: The Evolution of DevOps
GitLab: Global DevSecOps Report: Security Without Sacrifices [New]
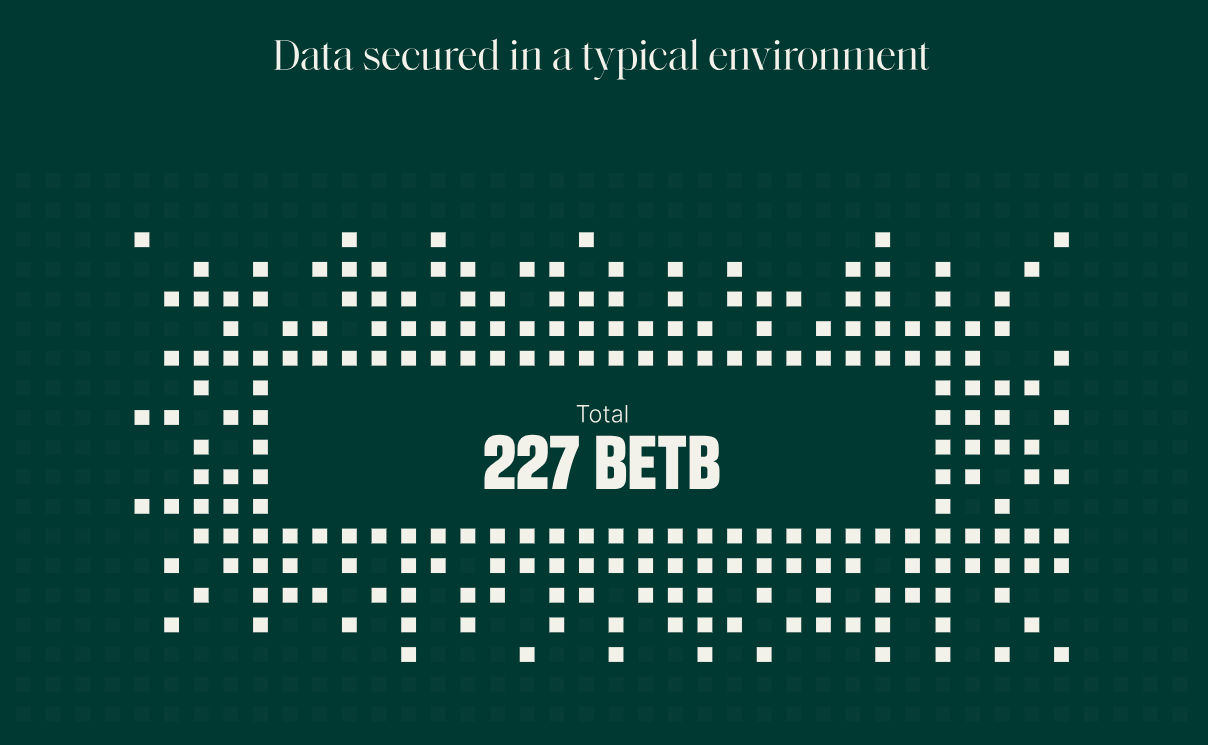
Data Security
Key Findings
In 2023, the average time taken to identify and contain a breach is 277 days—about 9 months. - IBM, Cost of a Data Breach Report 2023
A typical organization needs to secure over 227 backend terabytes, traditionally spread across a mix of on-premises, cloud, and SaaS. For perspective, this equates to approximately 330 billion Microsoft Word files. - Rubrik Zero Labs, The State of Data Security 2023
58% of organizations fail to acknowledge data breach disclosures. - CompariTech
Reports
IBM: Cost of a Data Breach Report 2023 [New]
Cyera: Top 35 Data Security Statistics to Know in 2023 [New]
Rubrik Zero Labs: The State of Data Security 2023 [New]
SaaS Security
Key Findings
A typical company with 10,000 employees has over 350 SaaS applications in its stack. - Adaptiv Shield, Uncovering the Risks & Realities of Third-Party Connected Apps 2023
Reports
AdaptivShield: Uncovering the Risks & Realities of Third-Party Connected Apps 2023
Wing Security: State of SaaS Report 2023
Endpoint Security

Key Findings
There was a 51.5% increase in posted ransomware victims between beginning of January and end of February 2023.- Guidepoint Security, GRIT Ransomeware Report for February 2023
LockBit accounted for about 33% of all Ransomare-as-a-service attacks. - MalwareBytes, State of Malware Report 2023
Reports
MalwareBytes: State of Malware Report 2023
Sophos: The State of Ransomware 2022
Zscaler ThreatLabz: The State of Ransomware Report 2022
Guidepoint Security: GRIT Ransomeware Report for February 2023
Contrary Research: The Era of Endpoints
ExpertInsights: 50 Endpoint Security Stats You Should Know in 2023
Security Operations
Key Findings
36% of enterprises are spending more with MSPs in 2022 than they did in 2020. - LogicMonitor, The Next-Gen Managed Service Provider Research Report 2022
88% of MSPs have experienced a brownout or outage in the past year – averaging one per month. - LogicMonitor
Reports
LogicMonitor: The Next-Gen Managed Service Provider Research Report 2022
MicroFocus: State of Security Operations 2021
Offensive Security
Key Findings
92% of organizations report a rise in their IT security budgets, and 85% report a raise in their pentesting budget specifically. - Pentera, The State of Pentesting 2023
Cyber Insurance as the primary reason to conduct pen tests grew from 2%in 2020 to 36% in 2022. - Pentera
57% of EU organizations surveyed reported a breach in 2022 - Pentera
Reports
Pentera: The State of Pentesting 2023
Randori: State of Offensive Security 2022
Email Security
Key Findings
Email Cyberattacks Spiked 464% in the First Half of 2023. - Acronis, Mid-Year Cyberthreats Report 2023*
Direct financial loss from successful phishing increased by 76% in 2022. - ProofPoint, State of the Phish 2023
72% of companies expect to be harmed in 2023 by a collaboration-tool-based attack. - Mimecast, State of Email Security 2023
Reports
Mimecast: State of Email Security 2023
ProofPoint: State of the Phish 2023
Acronis: Mid-Year Cyberthreats Report 2023 [New]
IoT Security
Key Findings
In 2022, the number of automotive API attacks grew by 380%. - Tripwire, 2023 Global Automotive Cybersecurity Report
Half (50%) of pneumatic tube systems were found to have an unsafe software update mechanism. - Armis, Top 10 device types with the highest number of attack attempts 2023
Reports
TrendMicro: ICS/OT Cybersecurity TXOne Annual Report Insights, 2022
Armis: Top 10 device types with the highest number of attack attempts [New]
Culture
Key Findings
As a region, North America is more favorable than the rest of the world when it comes to security culture. - KnowBe4, Security Culture Report 2022
Nearly two-thirds (57%) of respondents say their workplace provides them with resources and support for their mental health and well-being. Yet only 54% say their workplace prioritizes mental health. - Tines, State of Mental Health in Cybersecurity 2022
58% of respondents are currently taking medication for their mental health. 49% are currently seeing a therapist. 50% say they’re in excellent physical shape. 42% are getting 8 or more hours of sleep per night. - Tines
Reports
KnowBe4: Security Culture Report 2022
Aspen Institute: Diversity, Equity, and Inclusion in Cybersecurity, 2021
Fortinet: Cybersecurity Skills Gap, 2023
Crunchbase: Study of Gender Diversity on Private Company Boards, 2022
SANS: Security Awareness Report: Managing Human Risk 2023 [New]
VC and Start-up Ecosystem

Key Findings
Start-ups raised $18B across more than a thousand deals in 2022. In comparison, 2021 saw over $30B in VC funding. - Momentum Cyber, Cybersecurity Almanac 2023
IAM Security space led the pack in funding captured with a total of $3.1B secured funding in 2022. Risk and Compliance came in at second place with $2.9B. - Momentum Cyber
Reports
Momentum Cyber: Cybersecurity Almanac 2023
Quantum Computing Security
Key Findings
2.5 quintillion bytes of new data are being created every day. - IBM, Security in the quantum computing era
Reports
Organizational Security Approach Trends
Reports
Lightspin: The Complete Guide to SecDataOps and Vulnerability Management on AWS by Jonathan Rau
Cloud Spend Trends
Key Findings
The average cost of a breach for organizations with high levels of compliance failures was $5.57M in 2022. - IBM, Cost of a Data Breach in 2022
Managing cloud costs ranks as the top challenge for organizations of all sizes. Higher than security. - Flexera, State of the Cloud Report 2023
73% of respondents expect their enterprise tech budgets to stay flat or increase in 2023. - Battery Ventures, Cloud Software Spending Report 2022
Reports
Battery Ventures: Cloud Software Spending Report 2022
Flexera: State of the Cloud Report 2023
Conclusion
That’s all for now! Hopefully, you get some value out of this repo. I know I’ll be circling back to this a ton for my own insights. I’ll try to update this monthly. If there are any reports I missed that you think should be up here, please reach out to me on LinkedIn (Darwin Salazar) or Twitter @Darwnsm. If you aren’t yet a subscriber, click the button below to become a part of The Cybersecurity Pulse community!