Welcome to The Cybersecurity Pulse (TCP)! I'm Darwin Salazar, Head of Growth and Marketing at Monad and former Detection Engineer in big tech. Each week, I dig through all the major headlines to bring you the latest security product innovation and industry news. Subscribe below for weekly updates! 📧
Splunk’s user conference, .conf, took place in Boston last week and I had a front row seat to it all. I spent the week at the con sitting through keynotes, workshops, and catching up with friends + Splunk customers. This post will highlight what matters most to security teams and those building in the SecOps space.
TL;DR 📰
Splunk bringing a lot more capabilities into their SIEM offering including domain-specific AI agents, AI x SOAR and a detection studio. They’ve also added federated search support for Snowflake and announced their upcoming launch of their Time Series Foundation Model on Hugging Face.
Security teams deserve better than building integrations, parsers and pipelines
Stop spending hours wrangling APIs, building custom parsers and data pipelines. Monad is the easy button for security data integration, with 150+ pre-built connectors that just work. Our flexible platform seamlessly routes data from any source to any destination—whether you're using Splunk, Snowflake, S3, or all of the above. Transform, filter, and enrich your data with the utmost flexibility.
Let your security engineers focus on catching threats, not building plumbing. Monad handles the data complexity while saving you over 70% on your SIEM bill so your team can focus on what matters most: securing the org.
Standout Announcements from .conf 🚀
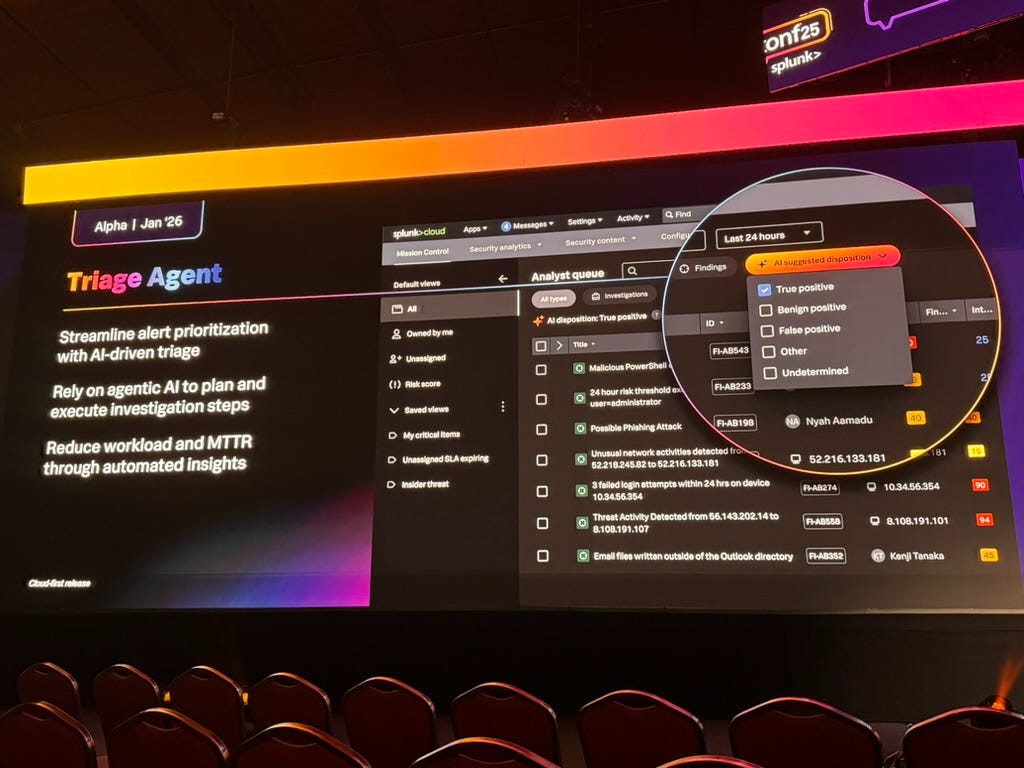
Triage Agent
The Triage Agent streamlines alert prioritization with AI-driven analysis, automatically executing investigation steps and reducing MTTR through automated insights. It evaluates, prioritizes, and explains alerts. This is expected in Alpha in January 2026 so long way till it’s in the hands of all Splunk users.
This is their “AI for SOC” answer. Lots of funding has been poured into AI for SOC startups in recent years. It’ll be interesting to see Splunk’s roll-out and the industry’s reception to this.
Malware Reversing Agent
Splunk's malware reversing agent unpacks malicious scripts step-by-step for clear analysis. It extracts IOCs, maps threats to MITRE ATT&CK, and eliminates bottlenecks from limited coding expertise. The demo showed it analyzing PowerShell commands in real-time, constructing temporary file paths, instantiating WebClient objects, downloading MSI files from remote servers, and invoking malware installation. The agent explains each line of code, flags evasion techniques, and groups recurring behaviors.
Most SOC analysts aren't malware reverse engineers so this is pretty significant.
AI SOAR Playbook Authoring
This feature converts natural language commands into SOAR playbooks. The interface shows a simple prompt like "Build a playbook to isolate a host if X alert triggers" and generates the complete workflow with custom code blocks and action blocks.
Lots of the qualms w/ SOAR is the technical complexity required to actually roll-out sophisticated playbooks. Hopefully this helps ease that thrash and reduce the need for hiring 3rd parties to build your playbooks.
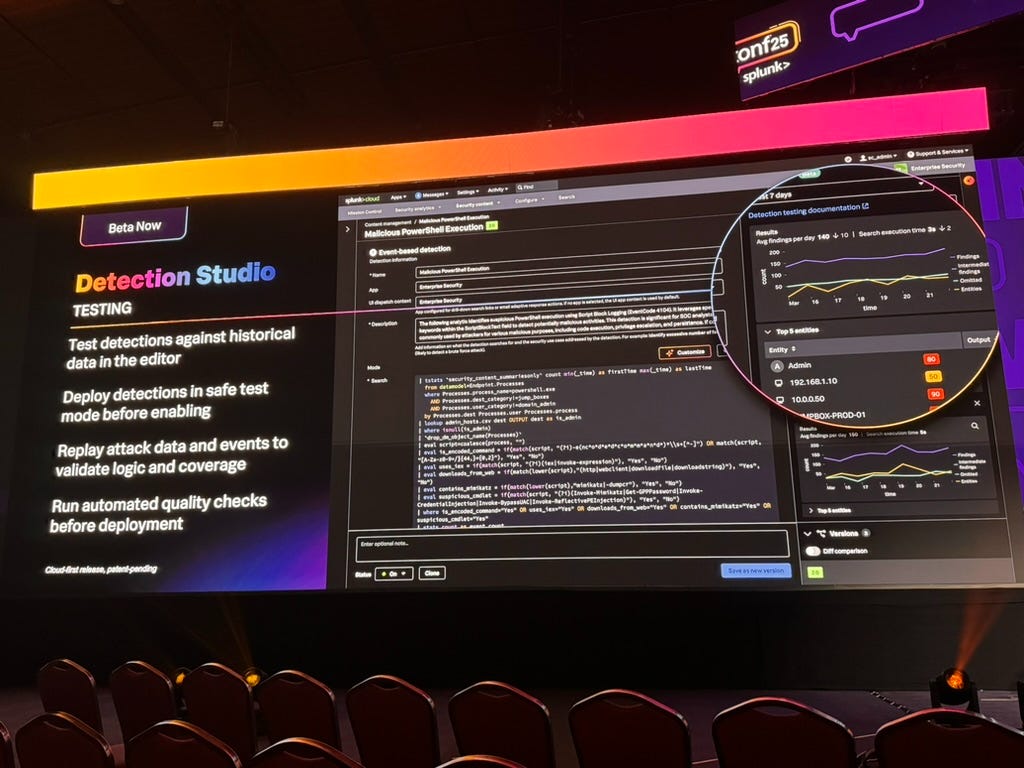
Detection Studio with AI Enhancement
Detection Studio now includes AI-powered features that help with many steps across the detection lifecycle including ideation, testing, fine-tuning, and monitoring. The interface shows real-time detection coverage metrics, validates data source availability, and includes a Personalized Detection SPL Generator that customizes detections for unique SOC environments. You can test detections against historical data (using data replays), deploy in safe test mode, and run automated quality checks before production deployment.
The Detection studio is in Alpha stage so still may be a while till it’s generally available.
Read the full press release here.
The Cisco Data Fabric + Time Series Foundation Model
The “data fabric” term is not new and probably dates back a decade+ at this point. However, I think Splunk is perfectly positioned to scale this out given the amount and variety (SecOps, NetOps, ITOps etc.) of telemetry they ingest + analyze. The Cisco Data Fabric will enable customers to build custom AI models with their proprietary data, unify distributed data sources for real-time insights, and power agentic workflows.
As part of this effort, they also launched a Time Series Foundation Model specifically for anomaly detection that'll hit Hugging Face in November.
There aren’t many foundation models that exist for security and I haven't come across one that is specifically trained for SecOps use cases so this is truly a game changer. This will enable anyone to build applications and use cases on top of that model and will be helpful for correlation (events, identities, etc), anomaly detection, predictive stuff and more. Excited for this to ship!
Read the full press release here.
Federated Search Support for Snowflake
Snowflake integration will be in Alpha in February 2026. This will allow security teams to query Snowflake directly from Splunk. Jeetu Patel, CPO @ Cisco is calling distributed data stores "data ponds" and "data puddles". More water x data metaphors..
Federated search is great for conducting retroactive data/log analysis (i.e., threat hunting, investigations). It allows you to store data in cost-effective stores while still being able to query it from Splunk. Some security teams have adopted Snowflake for security data storage and many enterprises use it to store other business data so having access to that context directly from Splunk will be pretty dope.
Read the full press release here.
The Quiet Part Said Out Loud💰
The elephant in the room: cost. Let’s face it. Splunk is cost-prohibitive for SMBs and even larger enterprises with small security budgets. If you’ve been in the SecOps space, you’ve probably heard this more than a few times. Even Splunk presenters themselves brought up pricing concerns on multiple occasions. That's how you know it's bad.
Kudos to Splunk for addressing it head on though. Not highlighted much on the mainstage but more so in the breakout rooms is that they’re building to make Splunk less cost-prohibitive including edge processors, ingest filtering, federated search, S3 replay, and even free Cisco firewall log ingestion (is there any fine print here?).
The Bottom Line 🤷🏽♂️
Should you care? If you're already a Splunk customer, absolutely. If you’re a Splunk SIEM or SOAR competitor? Certainly. What about if you’re a startup building in AI for SOC, federated search or the ETL space? Maybe… You should certainly be paying attention.
The reality is that Splunk remains the enterprise default because it’s been proven at the largest of scales for decades. The world’s largest and most important enterprises rely on Splunk as their SOCs command center. While the paradigm has shifted, these latest innovations show they’re not getting complacent and are building for the long-haul.
Splunk is going deep on SecOps workflows with features like Detection Studio, recommended data onboarding plans, S3 data replay, and enhanced federated search. That paired with their AI announcements brought into one unified experience will be a game changer for customers once it’s all in place.
Will Splunk still dominate enterprise SIEM in three years? 🤷🏽♂️ I don’t have a crystal ball and as always, it’s all about execution.
However, I do know that the announcements made at this year’s Splunk .conf positions them well as we move into the AI era in security.
Interested in sponsoring TCP?
Sponsoring TCP not only helps me continue to bring you the latest in security innovation, but it also connects you to a dedicated audience of ~7,300 CISOs, practitioners, founders, and investors across 125+ countries 🌎



AI agents, anomaly models, natural-language detections… Splunk sells hope on stage.
But if the data is rotten, AI just multiplies the noise. If the costs stay high, defenders keep drowning.
The truth: conferences announce progress. Real SOCs bleed in silence.