TCP #108: F5 BIG-IP + AWS Woes; Scaling 1 Million K8s Nodes; and Product News
What's hot in security🌶️ | Oct. 15th - Oct. 22nd. 2025
Welcome to The Cybersecurity Pulse (TCP)! I'm Darwin Salazar, Head of Growth at Monad and former detection engineer in big tech. Each week, I bring you the latest security product innovation and industry news. Subscribe to receive weekly updates!
AI Agents That Triage Vulnerabilities 24/7
Have you wasted countless hours chasing vulnerabilities that will never be exploited?
Maze takes a better approach. In a recent review of CVE-2025-27363, Maze’s AI Agents investigated like human experts, testing real exploit scenarios against the actual environment.
Non-exploitable risks were ignored. Exploitable were investigated further to evaluate their impact and likelihood.
Fewer false positives, faster fixes, and stronger security, built by engineers from Meta, Elastic, Amazon, and GitHub.
Howdy! 🤠
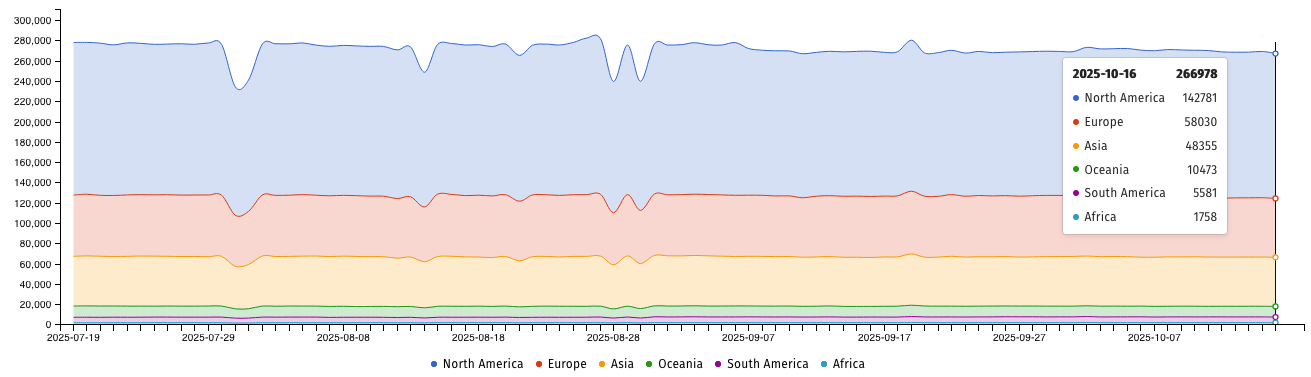
Hope you’re having a great week! Lots sp00ky things happening. F5 BIG-IP source code + eng config files stolen by ‘nation-state’ actors. AWS us-east-1 region causes outages for 1K+ companies.
Not great by any measure, but a good gut check for our industry on resiliency and DR+ IR plans
Here’s my favorite meme of the week:
Anyways, let’s dive in!
TL;DR 📰
🚬 F5 BIG-IP source code exfil – Nation-state attackers gained persistent access to F5, stealing BIG-IP source code + eng docs. CISA warns of “imminent threat” to federal networks.
🌩️ AWS us-east-1 outage takes down half the internet – It was DNS.. So they say.
🧩 Scaling Kubernetes to 1 Million Nodes – Ex-OpenAI engineer Ben Chess pushes K8s to extreme limits. Great read on where orchestration, observability, and security break down at hyperscale.
🕵️ Europol takes down SIM farm network – 40K SIMs, 49M fake accounts dismantled across 4 countries; 7 arrested..
💎 $102M Louvre heist exposes physical security flaws – ‘Heisters’ used ladders + chainsaws to breach the Apollo Gallery. Many metaphors for cybersecurity here.
🪪 Keycard raises $38M for AI agent security – Introduces task-level permissions for AI agents; backers include a16z and Acrew.
🐶 Datadog ‘BewAIre’ PR Reviewer – LLM-powered code-review engine now folded into their SAST suite; scans 10K+ Datadog PRs/week for risky changes.
💾 Veeam to acquire Securiti AI for $1.7B – Adds DSPM and data-privacy coverage to Veeam’s backup portfolio.
🧬 Defakto raises $30M Series B – NHI
📊 Anton Chuvakin on SIEM MQ 2025 – SIEM + SOAR now merged, AI SOCs emerging as SOAR 3.0. UEBA absorbed; EDR vendors evolving into SIEMs.
💰 Dataminr acquires ThreatConnect ($290M) – Adds threat intel automation + TIP capabilities.
🧠 Google launches agentic threat intel – Brings conversational AI to threat analysis
⚒️ Picks of the Week ⚒️
💎F5 BIG-IP at Risk After Attackers Gained Persistent Access to Crown Jewels💎
Last week, F5 disclosed that a “highly sophisticated nation-state threat actor” had gained persistent access and exfiltrated files from “certain F5 systems”. These systems included their BIG-IP product development environment + their “engineering knowledge management platforms”. Yes, this does include SOURCE CODE.
BIG-IP is an app delivery controller that handles load balancing, proxying and acts as a security gateway. It essentially handles how users reach web apps, APIs, or microservices by sitting between clients and backend servers.
So what Darwin? Why should I care? BIG-IP is relied upon by many Fortune 500s and government agencies across the world. The US CISA called this an “imminent threat” for federal networks. While many of us fear SolarWinds-like implications, F5 says they have not found any active exploitation.
The issue with this is that since the hackers stole source code + build info on the BIG-IP appliances, they could find and chain together 0-days and then deploy those on high value targets like US Govt. agencies. If the attackers got access to F5 customer configs, then they can craft more sophisticatedly tailored attacks.
The possibilities here are endless.
More details here:
🟢 Your Application Security Agents 🟢
Put a custom DryRun Security agent on every PR to flag logic flaws, policy violations, and complex vulnerabilities with clear steps to remediation. Define secure coding policies in plain English and enforce them on every PR. Developers get guidance, security gets coverage.
The root cause of Monday’s AWS us-east-1 outage is being pinned on a DNS resolution issue with the DynamoDB endpoint for the region which caused cascading effects for other critical AWS services. The outage impacted 1K+ customers including Delta Air Lines, Office 365, Lyft, Zoom, Asana, and even the McDonalds app.
This goes without saying, but having multi-region (and maybe multi-cloud) failover should be a top CTO+CISO priority. Depending on the business, downtime can lose tens or hundreds of millions of $ or worse, loss of life.
Scaling a Kubernetes Cluster to 1 Million Nodes
Ever dreamed of scaling a Kubernetes (K8s) cluster to a gazillion nodes? Then this post is probably great weekend reading for you. Even if you’re early on your k8s journey, this post is still for you. Ben Chess who worked at OpenAI for 5+ years ran an experiment on what it would take to run 1 million nodes within a single K8s cluster. The post is a technical masterclass and shows what limitations you hit when scaling k8s. After a certain threshold, security + observability suffers incrementally.
Europol Dismantles SIM Farm Network w/ 49 Million Fake Accounts Worldwide
Okay, now some good news! Europol recently took down a crime ring’s SIM farm of over 40K SIM cards operating over 49 million fake accounts. 26searches conducted across Austria, Estonia, Finland, and Latvia. 7 arrested. The ring helped carry out phishing, smishing, fraud and other criminal things.
Here’s a pretty badass video of the sting the Latvian police conducted on the SIM farm:
Louvre Museum Security ‘Outdated and Inadequate’ at Time of Heist
This is more physical security than cybersecurity, but it’s still security-related and something out of a movie so I’ll cover it. Heisters.. Is that a word? Anyways, heisters stole $102M worth of jewels from the Apollo Gallery at the Louvre. They got in through a window exposed to the street, a ladder and mini-chainsaws.
One would think that a place with so much worth would be more heavily guarded by drones, better built-in reinforcement, or even humans. But nope… I’m sure there are many metaphors one can draw from this heist and apply it to the cybersecurity space but I will leave that for another time.
🔮 The Future of Security 🔮
AI Security
AI agent security startup Keycard reels in $38M
Keycard Labs launched with $38 million ($8M seed led by Andreessen Horowitz and boldstart, $30M Series A led by Acrew Capital). Think task-level permissions for AI agents.
More AI Security news ⬇️
Application Security
Behind the Scenes of Datadog’s AI-powered PR Reviewer 🔥
One of my favorite things when I worked at Datadog was the dogfooding and upstart culture. Their recent work with ‘BewAIre’ is a great example of that. It’s an LLM-powered PR reviewer that looks across author behavior, code diffs, file metadata and more to detect risky pull requests. The post is great because it dives into how they use it to scan 10K+ PRs a week, working around model degradation and context windows for larger PRs and more. BewAIre has also been rolled into their SAST solution.
Stellar work by the Datadog SDLC team.
More AppSec news ⬇️
Data Security
Veeam to Acquire Data Security Firm Securiti AI for $1.7 Billion
Veeam announced plans to acquire data security posture management company Securiti AI for $1.725 billion in cash and stock, expected to close in early December. Veeam is a data backup + recovery co. This acquisition gives them DSPM capabilities and positioning Veeam well against competitors like Rubrik. And yes, since data security is a huge part of security, this also positions Veeam well for the AI era.
More Data Security news ⬇️
MIND Expands Endpoint DLP to Help Enterprises, MSSPs Secure GenAI Use at the Edge
Matters.AI Raises $6.25 Million to Safeguard Enterprise Data
Identity and Access Management
Defakto Raises $30 Million Series B for Non-Human IAM Platform
Defakto (formerly SPIRL) raised $30.75 million Series B led by XYZ Venture Capital with participation from The General Partnership, Bloomberg Beta, and WndrCo. Non-human identity (NHI) player.
Security Operations
SIEM, Startups, and the Myth (Reality?) of IT Inertia: A Reformed Analyst Reflects on SIEM MQ 2025
When Anton Chuvakin speaks on the state of security, SecOps, or SIEM, you should probably listen. 20+ yrs in security and 8 at Gartner. In this post, he provides his takeaways from this year’s Gartner SIEM Magic Quadrant. Among them:
AI does not drive SIEM purchasing decisions.
Gartner is not pay to play. MQ placement has nothing to do w/ how much a vendor pays.
SIEM and SOAR are fully merge. AI SOCs are pretty much SOAR 3.0.
UEBA has also been absorbed into the SIEM.
EDR vendors have graduated to full blown SIEMs.
If you’re in the SecOps space, follow Anton and check out his musings on the space.
More SecOps news ⬇️
Dataminr to acquire cybersecurity firm ThreatConnect for $290 million
Google introduces agentic threat intelligence for faster, conversational threat analysis
Interested in sponsoring TCP?
Sponsoring TCP not only helps me continue to bring you the latest in security innovation, but it also connects you to a dedicated audience of ~7,500 CISOs, practitioners, founders, and investors across 125+ countries 🌎
Bye for now 👋🏽
That’s all for this week… ¡Nos vemos la próxima semana!
Disclaimer
The insights, opinions, and analyses shared in The Cybersecurity Pulse are my own and do not represent the views or positions of my employer or any affiliated organizations. This newsletter is for informational purposes only and should not be construed as financial, legal, security, or investment advice.





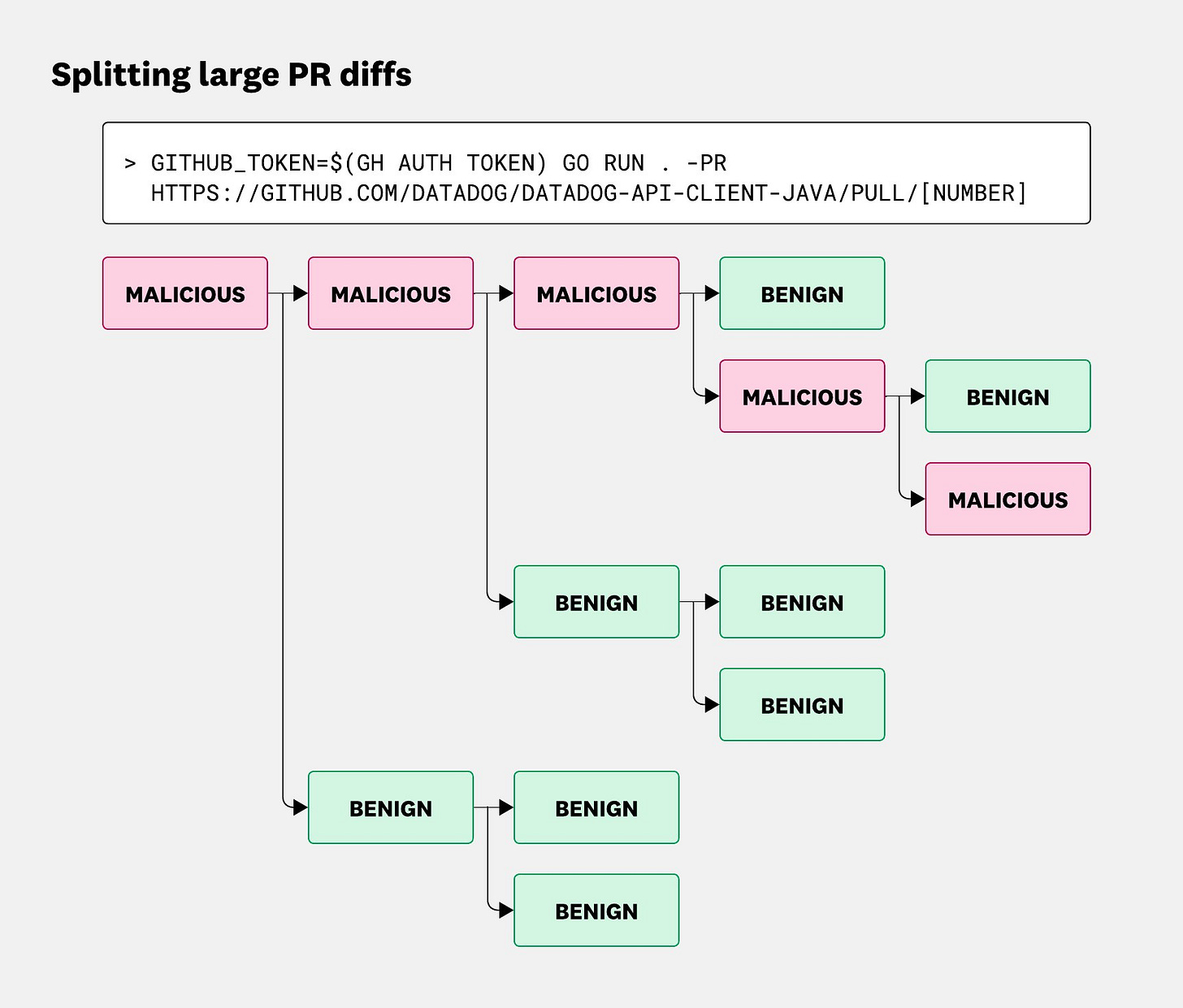
Great roundup Darwin! The BewAIre section really stood out - it's fascinating that you worked at Datadog and saw that dogfooding culture firsthand. The techncial breakdown of how they handle large PRs by splitting them into chunks and rolling up individual verdicts is brilliant. What I find most impressive is that they're achieving production-grade reliability (processing 10K+ PRs/week) while dealing with LLM context windows and model degradation. Rolling this into their SAST offering is a smart move since they already have the distribution channel to enterprises. Thanks for the insider perspective!