TCP #58: Playa Mode 🏜️
Security Product News | Aug. 20th - Aug. 28th, 2024
Welcome to Issue 58 of The Cybersecurity Pulse! I'm Darwin Salazar, Product Manager at Monad and a former Detection Engineer. Each week, I distill the latest and most exciting developments in cybersecurity innovation into digestible, bite-sized updates. If you’re serious about staying at the forefront of the latest in security products and industry news make sure to hit the “Subscribe” button below to get my insights delivered straight to your inbox every week 📩 🚀
Howdy! Welcome to another issue of TCP! We had a fairly eventful week on the M&A + fundraising side of the house yet not so much on the product side. That said, AI security is at the forefront of this week’s newsletter with Clint Gibler and Francis Odum both releasing stellar pieces for practitioners, investors and everyone in between.
Just a heads up before we dive in: No TCP issue next week as I’ll be on vacation 🌴 I’ll be back with the next issue of TCP on the week of Sept. 9th! This should also serve as reminder for you to touch grass and use your PTO.
Anyhow, let’s get into things! ⚒️
Picks of the Week🎯
TL;DR: Every AI Talk from BSidesLV, Black Hat, and DEF CON 2024
AI security was a HOT topic this hacker summer camp. Clint Gibler from tl;dr sec spent hours digging through the latest research and presentations to provide a easily digestible roundup of the 60+ talks that took place in Vegas earlier this month.
No matter where you are in your AI security journey, his post is a great place to get brought up to speed on the latest AI research.
Deep Dive Into The Security for AI Ecosystem
Over the past two years, we’ve seen dozens of AI security startups emerge and raise hundreds of millions in funding. I think that by now, we know that AI is not all fluff. AI is being rolled out across most industries and having real-world impact. That said, what does the past, present, and future of AI security look like?
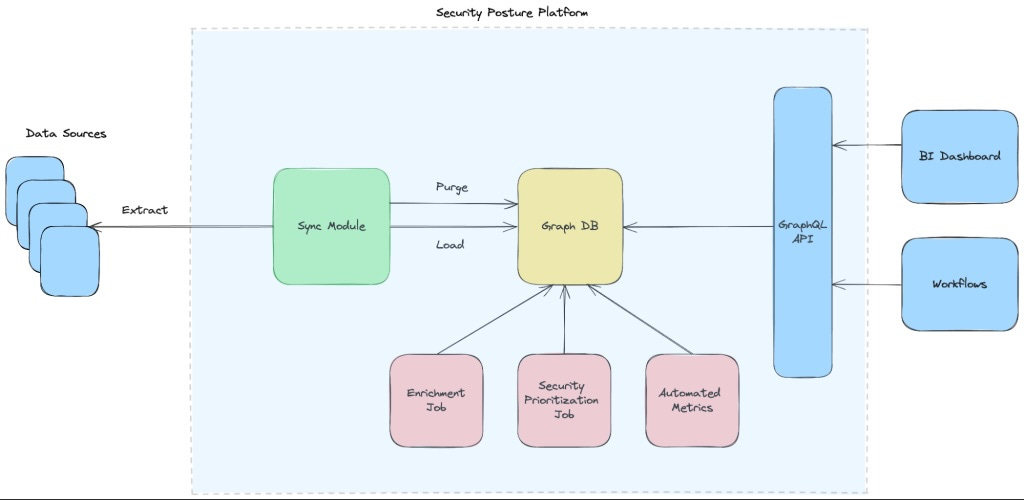
In this post, Francis Odum and Zain Rizavi take a very comprehensive look at the market for AI security and where it is headed. Worth the 20-30 minute sit down read!!How Prisma Cloud built Infinity Graph using Amazon Neptune and Amazon OpenSearch Service
A look at how Palo Alto Networks built its Infinity Graph which helps map cloud asset attack paths, blast radius and few other cool things. It’s pretty cool to get a behind-the-scenes look at how they built a feature that now services thousands of enterprises. Worth checking out if you build security products! 🔥
Why LinkedIn Developed Its Own AI-Powered Security Platform
It’s always great getting an inside look at what world-class security teams are up to. Netflix, Chime, Rippling, Coinbase, Robinhood, Canva and the likes often publish open-source tools and articles that detail about how they’re approaching different security challenges.
In this post, we get an inside look at LinkedIn AI-powered AI Security Graph. Of course, following a similar approach is something that only the top 1% of security teams can afford and pull off but its still pretty cool to see!NSA Issues Tips for Better Logging, Threat Detection in LotL Incidents
Cisco snaps up AI model and data security startup Robust Intelligence
Robust Intelligence is the first pure play AI security startup to be acquired. Much more consolidation to come, imo and as highlighted by Francis and Zain in story #2.
Check Point to Acquire External Cyber Risk Management Firm Cyberint
More consolidation in the external attack surface management space (EASM). Just this year, NetSPI, Rapid7, (and a few others that I can’t remember at the moment) have all acquired EASM vendors.
The key trend this highlights is that context is king for prioritization. EASM vendors help shine a light on how reachable and exploitable vulnerable systems may be. If a critical vulnerability is surface on a VM that is not publicly accessible, then is it really a critical vuln? EASM helps provide comprehensive context in such scenarios.
Data management startup Cribl nabs $319M at $3.5B valuation
Cribl recently announced a Series E round of $319M. Over the past couple of years, they’ve doubled down on their new product lines, Cribl Search and Cribl Lake. I imagine a good chunk of this funding will go toward R&D + GTM efforts for those while continuing to innovate on their Stream and Edge products. Either way, I’m a fan of what Cribl has done and where they are headed. Kudos to the great team there!
Side note: Here’s a pretty great pod with Cribl founder and CEO, Clint Sharp on the Grit podcast hosted by Kleiner Perkins.
Product News 📰
AI Security
HITRUST unveils new tool for AI risk management
If I had to bet, healthcare is one of the biggest early adopters of AI. Up until recent years, it must’ve been the wild west in securing the use of AI in the sector. Things are definitely changing with the HITRUST consortia taking aim at AI security with their new AI Risk Assessment tool. More vendors and services companies are also doubling down on AI security.
Data Security
How Fabric plans to make advanced cryptography ubiquitous
Startup using novel approaches to cryptography including zero-knowledge proof and fully homomorphic encryption. Timely topic with more quantum computing and cryptography momentum building up.
Updated Fortanix Data Security Platform Adds File System Encryption
Email Security
Offensive Security
Bye For Now!
That’s all for this week… and next! Vacation starts now 🦦