📡 TCP #61: Fal.Con; Agentic AI v. SOAR; And More
Security Product News | Sept. 18th - Oct. 1st, 2024
Welcome to Issue 61 of The Cybersecurity Pulse! I'm Darwin Salazar, Founding PM at Monad and former Detection Engineer. Every week, I cover the latest in security product innovation and news impacting the industry. If you’re serious about staying at the forefront on these topics, make sure to hit the button below to get my insights delivered straight to your inbox every week! 📩
Interested in sponsoring The Cybersecurity Pulse and connecting with over 4,000 security professionals across 100+ countries? Learn more below! 🌎
Welcome to a jam-packed edition of TCP! October is here which means Winter Arc. IYKYK. In any case, we’ve got a lot to cover this week including a deep dive on all the product announcements made at Crowdstrike’s annual Fal.Con conference. Aside from that, we cover 15+ product announcements, take a look at how data breaches impact the stock of publicly traded companies, and so much more.
Alright, let’s get to it!
Picks of the Week🎯
NIST Drops Password Complexity, Mandatory Reset Rules
NIST has updated their password recommendation guidelines in SP 800-63-4. Among the updates, they’ve recommended that credential service providers (CSPs) stop the following:
Mandating periodic changes
Requiring use of special character types
Use of knowledge-based authentication (i.e., security questions)
While I’m no password cracking expert, I’m split on this one. I feel that periodic changes and special character types make it much harder for credential-based attacks to succeed.
Congress Advances Bill to Add AI to National Vulnerability Database (NVD)
A bill that would enable NIST to create an official vulnerability reporting process for AI systems has been advanced to the U.S. House of Congress. The bill would mean that vulns found in AI systems would make it into NIST’s National Vulnerability Database (NVD).
Agentic AI in SOCs: A Solution to SOAR's Unfulfilled Promises
This was an interesting sponsored post by Radiant Security which takes a look at the 3 generations of SOAR and why SOAR hasn’t succeeded… yet. They make the case that SOAR is great at performing “doing” task but not “thinking” tasks. It lacks reasoning capabilities. This where agentic AI will save the SOC in their opinion.
While I think they’re onto something, I also think we’ve got a long way to go before we can trust autonomous agents to perform security tasks in an enterprise environment.
UnitedHealth Group CISO: We had to ‘start over’ after Change Healthcare attack
“The only thing that we kept from the old environment into the new environment was the cables. New routers, new switches, new compute infrastructure, deployed everything from a safe environment, truly started over. - Steven Martin, CISO at United Healthcare Group
Even 7 months later, the ransomware attack on Change Healthcare is still having an impact on UHGs operations. While the paid ransom was $22M, UHG predicts that the financial loss for this fiscal year will be north of $1B. The magnitude of this attack is on the same scale as the 2017 Equifax breach and should be studied by our industry, especially those in SecOps and IR roles.
All that said, this CyberScoop report gives us a glimpse of what the UHG CISO shared at the mWISE conference several weeks back. It’s a great peak behind the curtain of such an attack + it was good to see that he and his team leads prioritized mental health during the initial recovery phases… IR is .. hard.
The Relation Between Breaches and Stock Price Drops
Ever wondered about the correlation of what happens to the stock of publicly traded companies in the days, weeks, and months after a breach? Well, this report analyzed 118 companies and their stock price post-breach and found that stock prices bottomed out at -1.4% on an average of 41 days after a breach.
The biggest stock price drop post-breach was Equifax which dipped 60% at its lowest before recovering most of that nearly a year later. This is a very interesting report as it looks back as far as 2007 and across many industries. Worth checking out, imo!
Product News 📰
Product news. My favorite kind of news. It’s always good to see what some of the brightest minds in security are shipping to help their customers adapt in today’s threat landscape. Especially considering the billions that pour into R&D + Product every year.
That said, CrowdStrike just had their annual conference, Fal.Con, where they had some fairly major announcements.
Fal.Con ‘24 Product Recap 🐦
Unified Security Posture Management (USPM)
CrowdStrike has now combined DSPM, CNAPP, ASPM, and AI-SPM to create a USPM.
Project Kestrel
Unified data layer and product experience across the CrowdStrike Falcon platform.
SIEM
200+ new 3rd party actions for their Fusion SOAR
AI-generated parsers. Analyze log samples using LLMs to classify structure and build parsers.
AI-powered stuff
Attach Path Analysis added to their exposure management offering. This is pretty tablestakes for any exposure management tool today.
CrowdStrike Signal - An “AI-powered engine” added to Falcon Insight XDR.
Detection triaging capabilities added to Charlotte AI which helps investigate and triage alerts. Sounds very similar to what AI for SecOps vendors are doing. Should become tablestakes for any alert-based product.
Identity
Enhanced coverage for Microsoft Entra ID
Updates to Falcon Privileged Access
Interestingly enough, their recap blog post had a disclaimer on “Forward Looking Statements” which had legal jargon that probably helps limit liability on certain things. Worth a look if you’re into these types of things!
Full Fal.Con product recap can be found here.
Application security
Myrror Contextual Remediation Engine
Myrror Security has released their ‘Contextual Remediation’ feature which helps engineers answer critical questions about Myrror’s AppSec (SAST + SCA ++) findings. The feature helps provide context about the finding, remediation effort estimation, and forecast/illustrate the impact that implementing a remediation may have.
This is one of those features that truly help make user’s lives easier by removing guess work and limiting the risk of things breaking due to remediations.
Rest of AppSec product news ⬇️
Cloudflare moves to end free, endless AI scraping with one-click blocking
ArmorCode unveils two modules to help reduce software-based risks
Cloud security
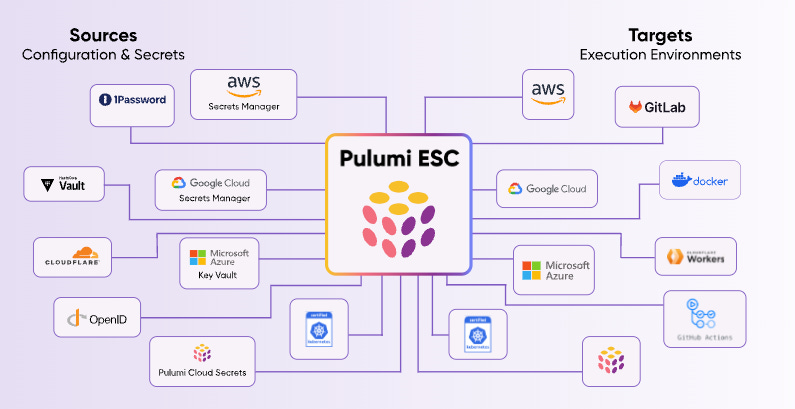
Pulumi unveils first two security products
Pulumi which initially started out as an infrastructure-as-code (IaC) provider has begun their foray into security with two new products:
Pulumi Environments, Secrets, and Configuration (ESC) - Unified secrets management across cloud services ++
Pulumi Insights - Asset relationship graph that surfaces dependencies and security/compliance issues. The product also has automated remediation capabilities and can bring unmanaged/un-IaC assets under IaC management.
I like this move by Pulumi and think they’re uniquely positioned to take the IaC market into the next level and to bring security to the hands of Infra and SW engineers.
Edera raises $5 million to improve Kubernetes security
K8s security is hard. Many vendors focusing on this problem. Edera recently raised $5M to tackle it with an innovative approach leveraging Rust and a type 1 hypervisor to provide isolation at the container level.
While I’m no expert in K8s security, it’s refreshing to see new products coming on the market with different approaches to difficult problems. What’s more refreshing to see is great marketing in security. Edera has nailed it as shown below.
Edera’s founding team is also pretty stacked and includes the former COO of Anchore and Chainguard, Emily Long.
Rest of CloudSec product news ⬇️
Dashboards-as-Code and More With Orca’s Enhanced Terraform Provider
Tamnoon raises $12 million to reduce critical cloud exposures
Identity Security
Permiso launches Universal Identity Graph
Permiso, an ITDR startup, has launched their Universal Identity Graph feature which integrates with many identity solutions including identity providers like Entra ID and cloud services like AWS to provide a holistic view at identity activity and posture.
When done right, more context = better prioritization = less noise/FPs for end users = more secure environments.
Kudos to the Permiso team on this launch!
Rest of Identity Security product news ⬇️
Offensive Security
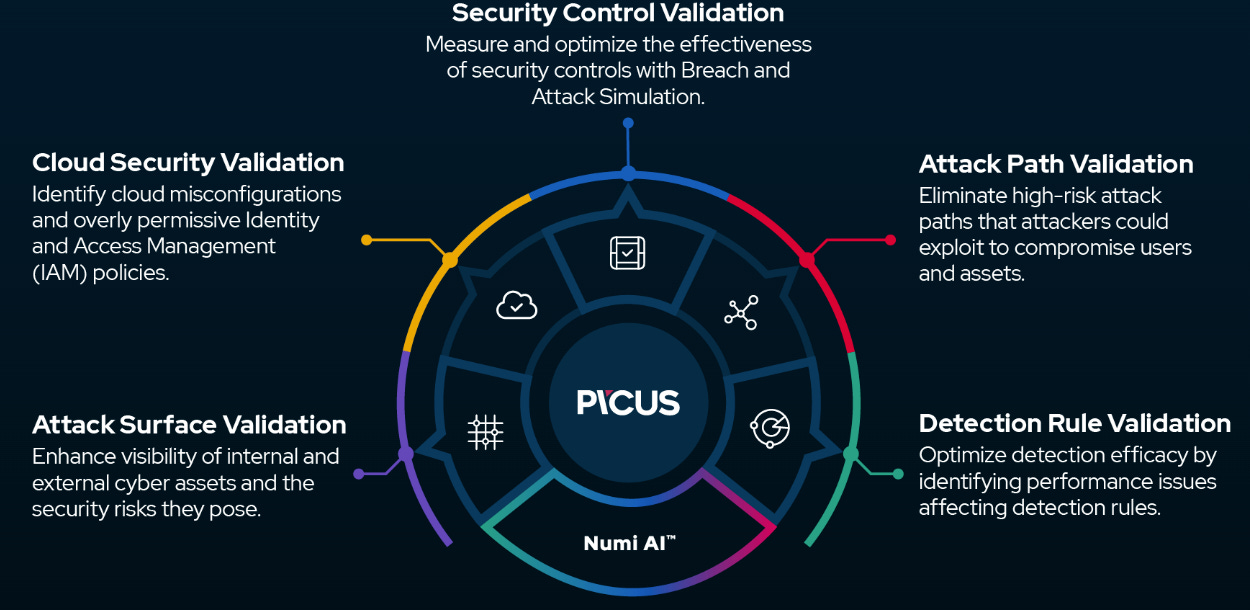
Picus Security Raises $45 Million
Picus Security recently closed on $45M Series C round. The way that they’ve come to market and differentiated themselves is through “security validation”. Simply put, they take an offensive security approach to validate their customer’s security posture across several domains.
Rest of OffSec product news ⬇️
Security Operations
Safe Security launches mobile app for CISOs
While risk intelligence products are not new, I think the approach that Safe Security is taking in offering their solution via mobile app is a breath of fresh air. How does it work in practice? How effective is it? etc. I don’t have the answers to these questions but I do think there is a lot of value for CISOs in being able to pull security and risk insights at their finger tips (given proper security guardrails, ofc).
Rest of SecOps product news ⬇️
The power of behavioral AI: Inside SentinelOne and Mandiant’s dynamic collaboration
Security automation platform provider Torq raises $70M to boost expansion and AI integration
Veeam Recon Scanner identifies adversary tactics, techniques, and procedures
Bye For Now!
That’s all for this week… ¡Nos vemos la próxima semana! 👋🏽