TCP #98: AIxCC; GPT-5 Security Woes; and Hacker Summer Camp News
What's hot in security🌶️ | July 30th - August 13th, 2025
Welcome to The Cybersecurity Pulse (TCP)! I'm Darwin Salazar, GTM lead at Monad and former detection engineer in big tech. Each week, I bring you the latest security product innovation and industry news. Subscribe to receive weekly updates!
🧘🏽♂️ AI-Powered Investigations, Zero Analyst Burnout 🧘🏽♂️
Drowning in noisy alerts and slow triage? Your analysts deserve better. Prophet Security’s Agentic AI SOC Analyst automates full-context alert investigations with machine speed and precision—cutting through the noise so your team focuses on real threats.
Free your analysts from alert fatigue. Speed up response. Catch what matters.
👉 Want to sponsor the TCP newsletter? Learn more here.
Howdy! I hope you’re doing well wherever you’re tuning in from. If you missed my post on my key takeaways from this year’s hacker summer camp, you can check it out here.
That said, we have a lot of ground to cover since it’s been two weeks since our last TCP weekly so let’s get to it! 🔨
TL;DR📚
🏆 DARPA AI Cyber Challenge winners announced with Team Atlanta taking 1st place and $4M grand prize
😔GPT-5 flops on many things including security with NeuralTrust jailbreaking it in 24 hours and SPLX finding GPT-4o nearly 2x more secure
🏆 Prime Security wins Black Hat Startup Spotlight beating FireTail, KeepAware, and Twine Security with their design-stage product security tool
🚨 Fortinet FortiSIEM vulnerability (CVE-2025-25256) scores 9.8/10 with exploit code in the wild allowing remote code execution
💰 Noma raises $100M Series B led by Evolution Equity Partners
🤝 SentinelOne acquires Prompt Security for $250M just 2 years after its founding
🤖 Anthropic launches /security-review for Claude Code enabling instant vulnerability scanning in terminal
🔐 Descope launches Agentic Identity Control Plane w/ policy-based governance
🎯 Wiz launches Exposure Management with UVM across cloud, hybrid and on-prem environments
Let’s cyber 🕺🏽
⚒️ Picks of the Week ⚒️
🏆 AI Cyber Challenge Winners Revealed in DARPA’s $30M+ Competition
The DARPA AI Cyber Challenge was a 2-year competition designed to gamify and streamline the development of AI security tools tailored toward securing US critical infrastructure and better vulnerability management. The teams built their own cyber-reasoning systems which have been open-sourced here. $30M+ in total prize pool.
Key stats about the challenge below:
The code bases in scope were 54 million lines total and had 70 vulns spread out
Detection rate (54 of 70 synthetic vulnerabilities found - 77% success rate)
Only 37% of vulns were detected in last year's semifinals
Patching capability (43 of 54 found vulnerabilities were successfully patched)
Patching is hard. This is a great sight.
Unknown unknowns (18 previously unknown zero-days discovered, 11 patched)
12 in Java code bases and 6 in C.
Speed and cost efficiency (45-minute average patch time at $152 per fix)
The winners, Team Atlanta, took home $4M. Trail of Bits crew took home $3M in 2nd place.
Other things to note:
Team Atlanta didn't go full AI. They leveraged traditional vuln discovery approaches like dynamic analysis, fuzzing, and static analysis paired w/ OpenAI LLMs (o4-mini, GPT-4o and o3).
This competition further validates that AI for security has massive upside.
We need more of this.
Dig deeper here:
DLP. Who knew 3 letters could be so daunting.
Dope.security eliminates the anxiety with an AI-Powered CASB DLP. Powered by LLMs dope.security identifies and classifies sensitive files in a single click. No DLP rule configuration required.
Monitor and remediate your org’s external file permissions all in one place
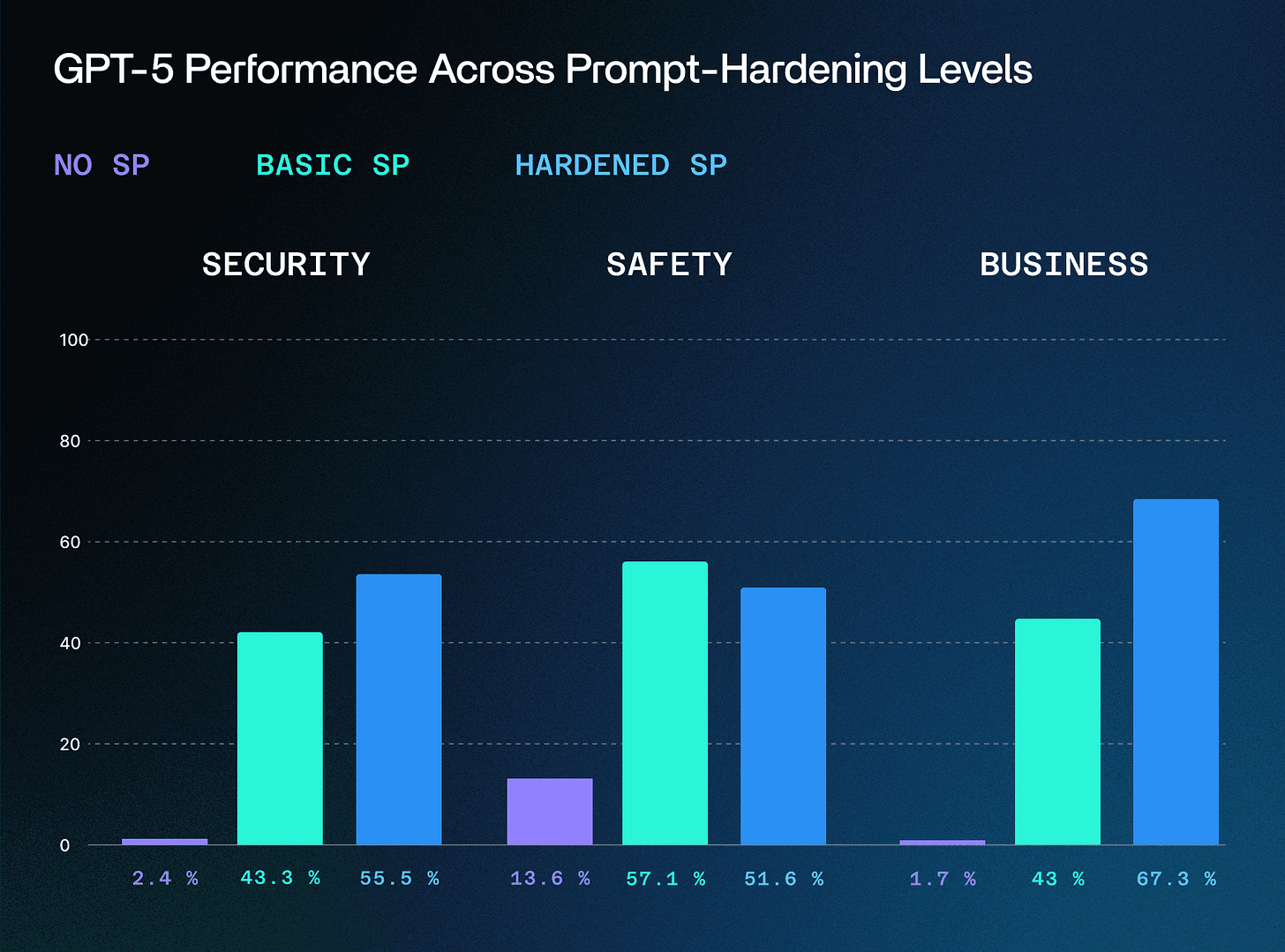
GPT-5 was released last week and it's not looking good. Not only are people reporting that it hallucinates more, has less creativity, and it ignores context, but it also flopped on the security front:
NeuralTrust jailbreaks GPT-5-chat using Echo Chamber + Storytelling
SPLX research finds that GPT-4o security + safety scoring is nearly 2x better than GPT-5.
I have many questions here. Does this indicate that this wave of AI plateauing? How do you control which models enterprise users can use? Are any security tools using GPT-5 today and if so, can users switch back to legacy models? Do vendors using AI models perform their own benchmarking to identify drift + performance issues across models or do they rely on others?
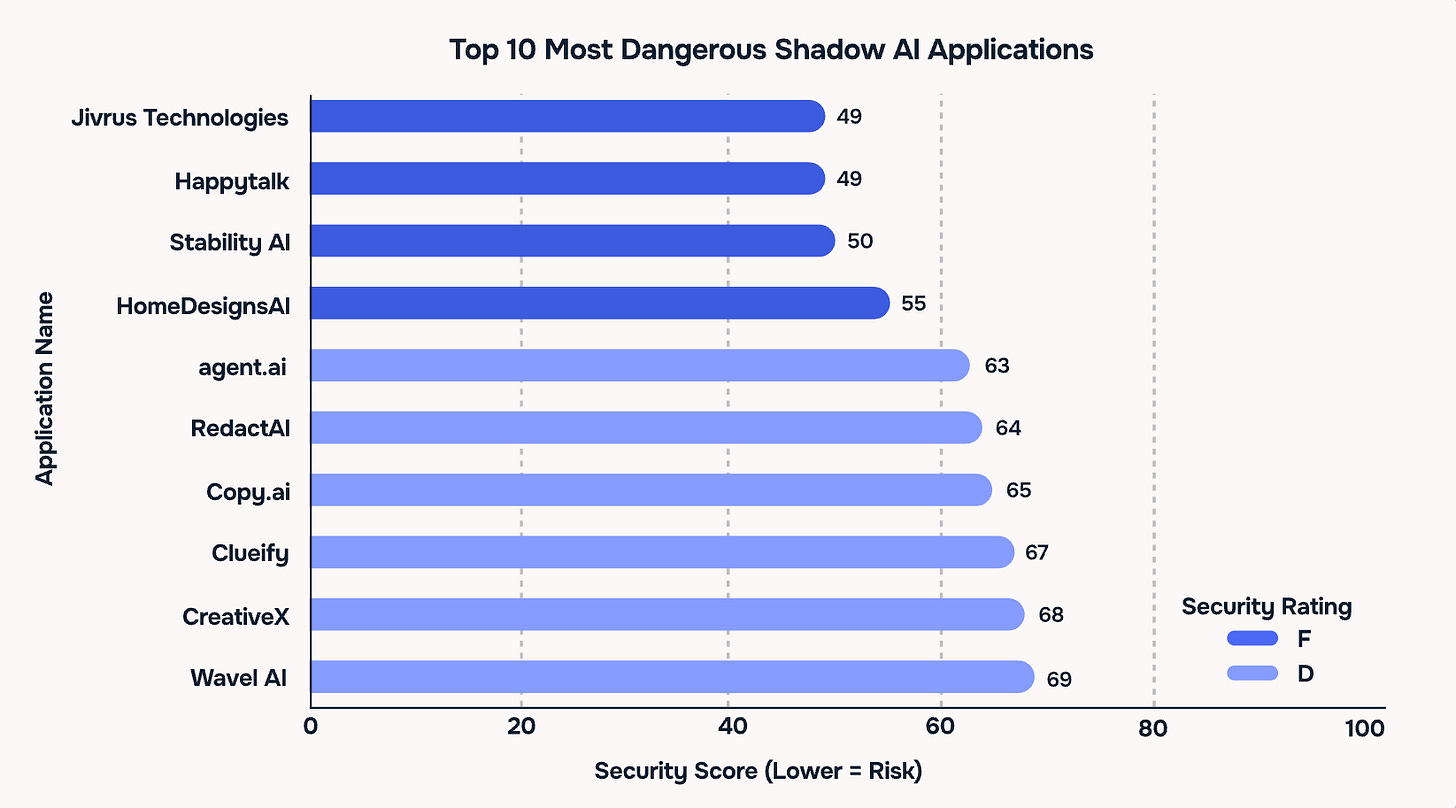
👤 Reco's 2025 State of Shadow AI Report
I recently partnered with Reco to deep dive into the big Shadow AI problem everyone keeps talking about and honestly, it's pretty bad. AI has revolutionized the way we work and there are thousands of tools out there. Some are 'vibe-coded', others built in adversarial nations, while others wouldn't pass your sniff test if you saw it in use. The problem is that most orgs don't have Shadow AI discovery and governance tools in place meaning that these AI tools present new attack surface and opportunity for sensitive data leaks. IBM's recent Cost of a Data Breach report even found that breaches involving Shadow AI add an additional $670K in damages.
Here are some key findings from Reco's report:
Jivrus Technologies, Happytalk, and Stability AI had the lowest security scores (F-grade) of all assessed apps
Small businesses face the highest shadow AI risk, with 27% of employees in companies with 11-50 workers using unsanctioned tools
OpenAI apps accounted for 53% of all detected Shadow AI use
Download the report here and check out Reco if you have Shadow AI or SaaS security needs. They have 200+ integrations and one of the best, if not the best, solutions on the market for this stuff.
🏆Prime Security Wins Black Hat's Startup Spotlight Competition
Prime Security is the Startup Spotlight winner at this year's Black Hat US. They beat out FireTail, KeepAware, and Twine Security. Prime is a product security tool that places a heavy emphasis on the design stage by hooking into CI/CD and other dev tools. Pretty neat.
Fortinet Warns About FortiSIEM Vulnerability (CVE-2025-25256) With In-the-Wild Exploit Code
Fortinet has advised FortiSIEM customers to update versions after discovering a vuln w. CVSS score of 9.8/10. The vuln allows for remote code execution via OS command injection and affects all versions except their latest. They say exploit code is in the wild which means it's most likely being exploited.
What could possibly go wrong you may be asking? SIEMs are goldmines for recon and a major choke point if taken over by attackers. There's a lot that could go wrong here.
🔮 The Future of Security 🔮
Note: Given the influx of news this week, I didn’t have the chance to parse through and synthesize everything. Thus, I’m leaning on AI to do some of the heavy lifting.
AI Security
Noma raises $100M Series B in a round led by Evolution Equity Partners, with continued participation from Ballistic Ventures and Glilot Capital. Noma is one of the hottest names in the AI security space and they're expanding aggressively. The interview above provides a look at how their Founder + CEO is thinking about the future of AI Security.
SentinelOne acquires Prompt Security for $250M
Prompt had raised $23M through Series A. Their solution covers GenAI and agentic AI security. Great exit for a 2-yr old company and great pick up by SentinelOne. Other major players are shopping for AI security capabilities including CheckPoint, Zscaler, and F5.
This comes on the heels of Palo Alto Networks acquiring ProtectAI and Tenable acquiring Apex. AI security space is ripe for more M&A.
More AI Security news ⬇️
Cisco’s Foundation AI Advances AI Supply Chain Security With Hugging Face
Startup SPLX Expands AI Security Platform with Runtime Protection Tool
Foundation-sec-8B-Instruct: An Out-of-the-Box Security Copilot
Application Security
Anthropic automates software security reviews with Claude Code
Anthropic launched automated security reviews for Claude Code. All you have to do is type "/security-review" in terminal to instantly scan for vulns like SQL injection, XSS, and authentication flaws before committing code. Neat. I think foundational model shops are uniquely positioned to take on security and that they have a moral responsibility to do so.
Palo Alto Networks announces Cortex Cloud Application Security Posture Management
Their ASPM will be GA in October. To no surprise, they're placing a heavy focus on context and are building out their AppSec integration ecosystem with 3rd parties like Snyk and Veracode. The ASPM is seen as an extension of Cortex Cloud which pairs CNAPP and CDR.
Cloud Security
Sysdig Introduces Agentic AI for Cloud Security Prioritization
Sysdig Sage is an agentic solution for streamlining cloud security discovery and remediation. Good use case.
Data Security
Cribl has launched capabilities to mask, block, or properly route sensitive data (i.e., credentials or PII) from their telemetry pipelines. This is great.
More Data Security news ⬇️
Rubrik Agent Rewind enables organizations to undo mistakes made by agentic AI
BigID Launches WatchTower for AI & Data to Deliver Always-On Risk Visibility Across the Enterprise
Varonis unveils Next-Gen Database Activity Monitoring for agentless database security and compliance
Identity Security
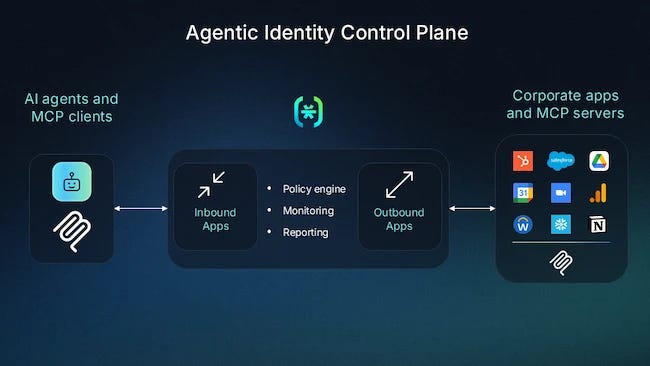
Descope launches Agentic Identity Control Plan for AI identity security
Agentic identity security is a top concern due to the unprecedented speed and access these things have. Descope is uniquely positioned to solve for this and they recently launches their Agentic Identity Control Plane which provides policy-based governance for AI agents. #cool
More Identity Security news ⬇️
1Kosmos raises $57M to advance passwordless authentication and global identity security expansion
BloodHound 8.0 debuts with major upgrades in attack path management
Delinea introduces Iris AI to enhance identity security with real-time access control
Security Operations
CrowdStrike Tailors Adversary Intelligence to Customer Environments
CrowdStrike's Adversary Intelligence now takes a more personalized approach by assessing threat intel from an organization’s industry, infrastructure, and exposure lens.
AttackIQ debuts Watchtower to automate cyberthreat intelligence analysis
The new capabilities leverage AI to provide tailored threat intel and IoC analysis specific to the customer's environment. It also auto-generates adversary emulation scenarios to test the defenses of customers.
More SecOps news ⬇️
DXC and 7AI Unveil Agentic SOC to Redefine Managed Security with Autonomous AI Agents
Microsoft unveils Project Ire: AI that autonomously detects malware
Vulnerability Management
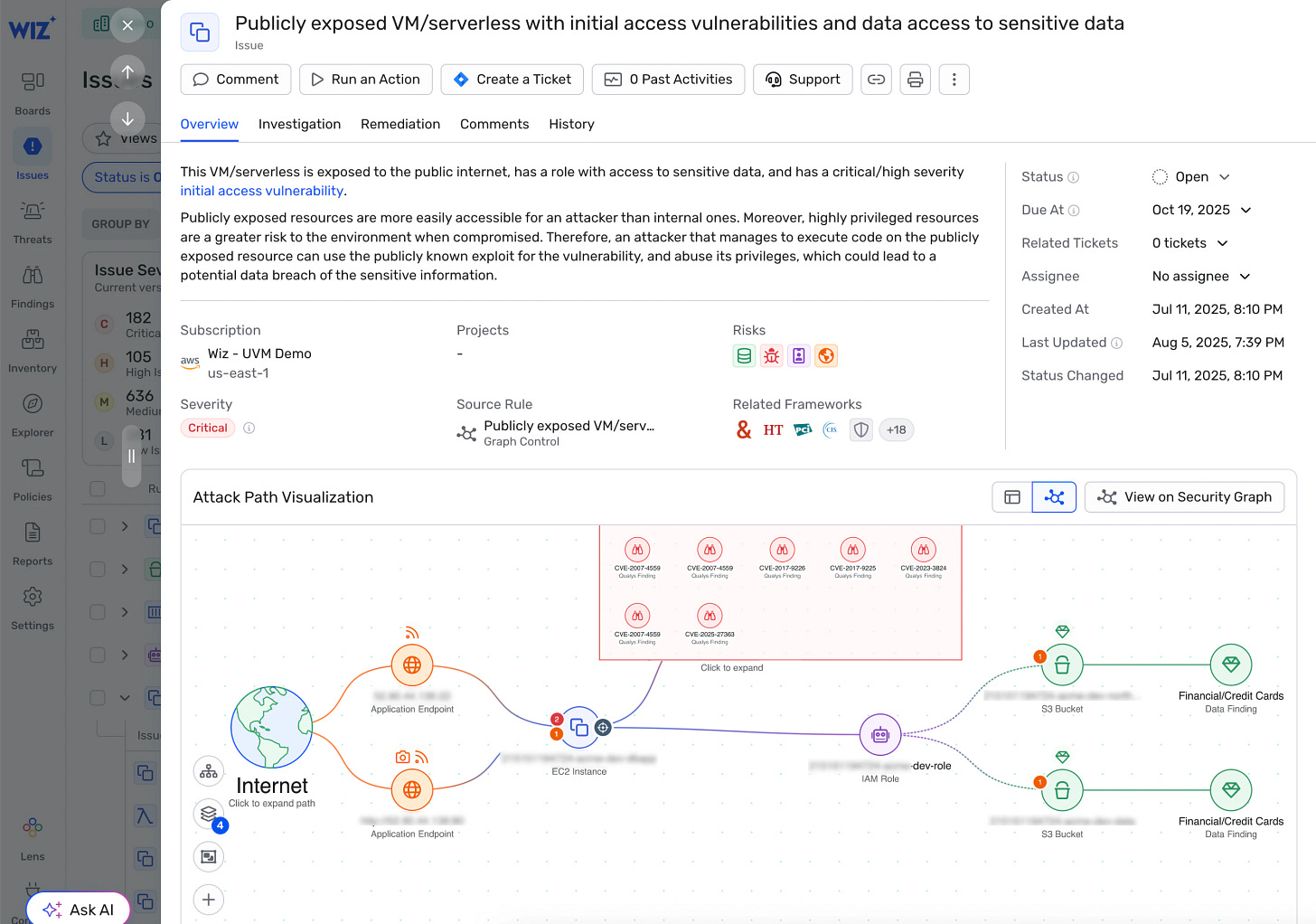
Introducing Wiz for Exposure Management: Unify, Prioritize, and Remediate Exposures Everywhere
Wiz recently released Exposure Management with Unified Vulnerability Management (UVM) from their Dazz acquisition which extends the Wiz magic we all know to help secure hybrid and on-prem infrastructure by ingesting data from existing scanners. The platform connects the dots across environments - showing how a code vulnerability becomes a privileged container in production, or how an on-prem server connects to sensitive cloud data.
Interested in sponsoring TCP?
Sponsoring TCP not only helps me continue to bring you the latest in security innovation, but it also connects you to a dedicated audience of ~7,300 CISOs, practitioners, founders, and investors across 100+ countries 🌎
Bye for now 👋🏽
That’s all for this week… ¡Nos vemos la próxima semana!
Disclaimer
The insights, opinions, and analyses shared in The Cybersecurity Pulse are my own and do not represent the views or positions of my employer or any affiliated organizations. This newsletter is for informational purposes only and should not be construed as financial, legal, security, or investment advice.