The Future of Data Security: From AI Agents to Unified Platforms
A deep dive into modern data security challenges and the unified platform solution
Welcome to The Cybersecurity Pulse (TCP)! I'm Darwin Salazar, Head of Growth at Monad and former Detection Engineer in big tech. Each week, I dig through all the major headlines to bring you the latest security product innovation and industry news. Subscribe below for weekly updates! 📧
About the Author
Hi! 👋 I’m Darwin Salazar and I've dealt with data security challenges up close from multiple angles, including leading HITRUST compliance initiatives and building medical device-to-cloud pipelines at Johnson & Johnson, consulting on PCI DSS engagements for Fortune 500 clients, and crafting cloud misconfiguration detection rules at Datadog. I'm excited to share what I’m seeing in the space, where I think we’re headed, and who’s at the forefront in this space.
TL;DR 🎯
Proprietary data is the crown jewel for most organizations. For attackers, it's either the prize itself or the means to their ultimate goal.
AI has fundamentally changed the way organizations think about data security.
Think about the rate of adoption and impact of AI agents, MCP servers, Shadow AI, 3rd party AI supply chain risks.
Think GenAI generated sensitive data based off of sensitive inputs.
Think data poisoning and risks to AI model integrity.
The traditional data security risks have not gone away.
The data security regulatory landscape has only intensified in recent years.
The difference between data security and any other domain is that data security must be horizontal by nature, spanning across identity, cloud, endpoints, and applications rather than living in any single domain.
Point solutions and traditional DLP fail to keep up with the velocity and distribution of sensitive data.
A unified platform approach helps tackle most of our previous shortcomings in data security while addressing emerging threat vectors.
We cover how Varonis is a great case study of the platform approach applied to data security due to their metadata framework, 20+ yrs of evolution, MDDR, DAM, DSPM, identity security capabilities and much more.
The bottom line: In an AI-powered world where data moves at machine speed, only unified platforms can provide the visibility, context, and automated response needed to stay ahead of traditional and emerging threats.
Introduction
We spent 20 years building walls around our data. Then we gave AI the keys to nearly every door. For many organizations, their data is their moat and is what’s paving their next wave of growth as they build, adapt, and deploy AI systems across their workflows. Think about patented tech, billion dollar+ R&D efforts, legally protected info, healthcare patient records, etc. Now think about just how fast consumers and enterprises are adopting the latest AI apps and integrating it across the board. The speed is mind-boggling and opens us up to many unknowns.
Take EchoLeak, for example. It was a novel vulnerability type discovered in Microsoft 365 Copilot that could have allowed exfiltration of sensitive data right out of Copilot’s context window with little user interaction. Then you have enterprise AI apps and new protocols like Model Context Protocol (MCP) which integrate with existing tech stacks, inherit permission debt and can access sensitive data. To make things worse, it feels like AI is generating more sensitive data on a weekly basis than what humans create in a lifetime.
That said, I’m not here to spread doom and gloom. Security adapts as we always have. There are world-class security leaders that have navigated similar challenges for decades and there are vendors who have done the same. Think about the emergence of the data center, virtualization, the cloud, SaaS apps, and now AI. Each new wave introduces more complexity that stacks on top of existing challenges, yet we always adapt over time to meet them. The AI wave is different from others for many reasons, but I also have a sense of optimism about what AI can do for data security programs.
In this report, I’ll be digging into how the data security landscape has evolved in recent years, what a data security platform should look like in 2025 (using Varonis as an example), and what may lie ahead for the space.
New Data Security Risks in the AI Era
AI Agents
Widely adopted AI agents like Microsoft 365 Copilot, Glean and Salesforce Agentforce come with large promises, but also new risks. Many of these AI agents inherit their creator’s user permissions by default, which means if your users have more access than they actually need (most do), then the AI tools do as well. In fact, according to Varonis’ latest research, 99% of organizations have sensitive data unnecessarily exposed to AI.
Even more concerning: around 90% of sensitive cloud data is left openly accessible to these AI apps. A simple prompt could trigger an AI to pull sensitive information from various sources, making attackers' lives much easier. Traditional DLP and DSPM controls just can’t keep up with the speed and scale at which these AI agents operate.
Modern data security platforms must see AI the way attackers do—as a privileged user with unprecedented reach. This means understanding not just where sensitive data lives, but how AI agents access it, what permissions they inherit, and whether that access aligns with business needs. When your AI can touch data across clouds, SaaS apps, databases, and file shares in milliseconds, your security must operate at the same speed and scale.
MCP and New Protocols
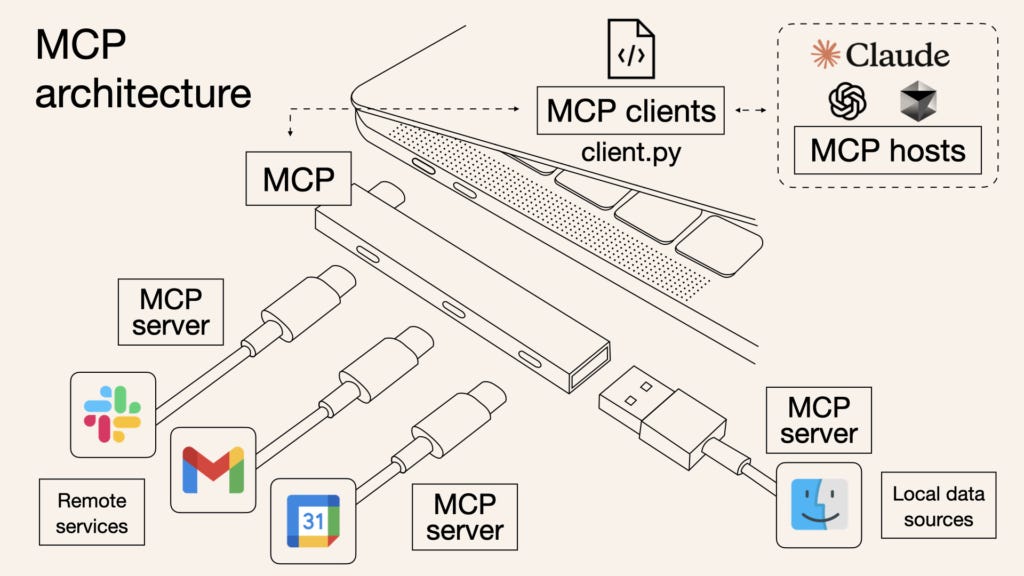
The emergence of Model Context Protocol (MCP) servers represents a fundamental shift in how AI agents, apps, and humans interact with organizational data. While MCP servers enable us to securely access local data sources, databases, and APIs through standardized protocols, they also introduce new attack vectors where a single compromised server could expose multiple data sources simultaneously.
While MCP gives AI superpowers, it also amplifies traditional prompt injection attacks like the EchoLeak vulnerability by allowing attackers to potentially manipulate AI agents into executing malicious commands across their MCP connections. As MCP servers aggregate access across previously isolated data silos, the principle of least privilege becomes more critical than ever. Organizations must now address this convergence of risks where infrastructure designed to enhance AI capabilities could become their weakest security link.
As seen in previous technology waves, when there is a rush to adoption, security is often an afterthought. New AI tools are not immune to the same risks that have plagued us for decades. Case in point, look at the recent Asana MCP bug or the critical severity vuln that allowed for Remote Code Execution (RCE) in mcp-remote, a popular MCP tool downloaded over 400K times. The risks don’t stop there.
While there hasn’t been a public incident where an MCP server compromise was the cause, the vulnerabilities and risks are certainly there so it may only be a matter of time.
GenAI Data Leaks
GenAI has exploded across enterprises, with 96% of organizations now actively using these apps—three times more than just a year ago. But there’s a downside: nearly half (46%) of recent data loss incidents involved proprietary code mistakenly shared via AI prompts. Samsung experienced this firsthand when engineers accidentally leaked confidential source code to ChatGPT leading to a full suspension of all ChatGPT use till they figured out how to secure it.
Such incidents highlight that well-intentioned employees can easily expose sensitive data by pasting it into AI prompts, effectively creating an unsanctioned data pipeline out of the business.
Shadow AI
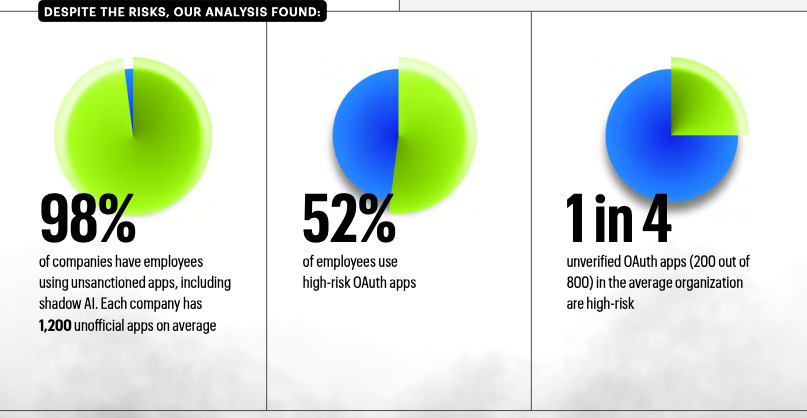
Then there’s Shadow AI, AI tools that employees adopt without security’s approval. 98% of organizations have unapproved AI apps lurking within their environments 🤯. Often, these tools integrate directly into apps like Slack or email via OAuth or browser extensions, gaining deep access to sensitive information without anyone in security even noticing.
For instance, a seemingly innocent AI-powered email assistant could access calendars, customer data, or sensitive files. If not vetted by security, this tool could expose sensitive data in a number of ways. When users adopt apps that make their jobs easier/better, they will be extremely reluctant to give them up just because security says so. They will almost always try and find a way to circumvent whatever controls are in place.
In short, while the AI revolution has delivered immense value to businesses around the world, it’s also opened up a can of worms on the data security front.
3rd Party AI Supply Chain Risks
The third-party AI supply chain introduces another layer of complexity and builds on our Shadow AI + GenAI Data Leak sections. Many enterprise AI apps are essentially wrappers around foundational models like GPT, Claude or even DeepSeek in some instances. The key here is that some vendors, especially startups, are not always transparent about it.
This creates hard-to-track data patterns where sensitive data might be processed, cached, or stored across multiple vendors without clear visibility. When an employee connects an AI writing assistant to your email, that tool might be sending your data through nested API calls to various AI providers, each with their own retention policies and security practices (or lack thereof). You lose the chain of custody for your data, which could be exposed through a vulnerability in any link of this AI supply chain. Even the most mature security teams have trouble keeping up with this which is why an AI governance plan + proper tooling is crucial, especially in heavily regulated industries.
Traditional Threats Haven't Disappeared
Sensitive Data is Everywhere
In 2025, sensitive data lives everywhere: on-prem file shares, cloud platforms, productivity tools, employee devices, and even shadow AI applications. It's become incredibly easy to deploy new resources across multi-cloud and hybrid environments, often using just a few lines of code. This ease significantly complicates visibility and governance. App-to-app and AI-to-AI integrations only make matters worse by exponentially expanding the potential attack surface and letting sensitive data move freely.
Insider Threats
Malicious insiders, careless users, and compromised accounts all fall under this category. Insiders often already have broad access, so if their account goes rogue or if they upload sensitive data to a shady AI app, it can eventually constitute as a data breach. We’ll discuss how to combat this in following sections.
Ransomware and Supply Chain Attacks
Ransomware attacks can cripple operations and expose a company’s sensitive data. Take the Change Healthcare breach for example, it devastated medical supply chains across US, leading to some medical practices temporarily shutting down and people not being able to receive their medication from pharmacies.
Just as ransomware can impact physical supply chains, it can come by way of your digital supply chain. Your data doesn't only live in systems you directly control. Partners, vendors, contractors, and SaaS providers often store or can access your sensitive information. A breach in your supply chain can be as devastating as one in-house. Recent years have shown us numerous examples of attackers exploiting weaker links ( i.e., a supplier, an IT service provider, a cloud tool) to get to the ultimate target.
The Evolving Regulatory Landscape
New regulations are pushing companies to prioritize security with increasing urgency. Here's what's driving compliance requirements today:
Global Privacy Laws
GDPR enforcement has escalated (Meta's €1.2B fine in 2023)
Similar laws spreading globally mean stringent data protection is required almost everywhere
Industry-Specific Frameworks
PCI DSS 4.0 and HITRUST now emphasize continuous compliance over periodic checks
Healthcare and finance face the strictest requirements with severe penalties
AI and Disclosure Requirements
EU AI Act (fully enforceable 2026) classifies AI systems by risk level
SEC mandates 4-day cyber incident disclosure for public companies
Board-level accountability is now standard
U.S. State Laws
California's CPRA and similar state laws require "reasonable security" measures
Focus on encryption and breach impact mitigation
The Shift to Data-Centric Security and Unified Platform Approaches
Traditional perimeter-based security fails when sensitive data spans multiple cloud platforms, SaaS applications, AI apps, and on-prem environments. Data-centric security is an approach that shifts focus from securing access points to protecting the data itself, wherever it resides. This requires answering critical questions that most organizations struggle with:
Where is our sensitive data located? What are our crown jewel data stores?
Who has access, and is that access right-sized?
How is data classified and encrypted?
How do we know when certain data usage or activity is anomalous or risky?
DSPM tools have become table stakes because they continuously discover, classify, and monitor sensitive data exposures across your entire environment. While DLP capabilities are still key, as a standalone product, it simply generates too much noise. The broader challenge here is trying to address AI agents, MCP vulnerabilities, shadow AI, insider threats, and compliance requirements with disconnected tools. Without visibility and correlation across the activity taking place with your critical identities, environments, and crown jewel data stores, you’re pretty much flying blind.
Modern data security requires a platform approach that provides unified visibility across identity, data access, AI usage, and user behavior. You need detection and that understands context and automated response + prevention that acts at AI speed. Without integrated coverage across IAM, AI security, cloud + on-prem, UEBA, and detection & response, organizations are often left with blind spots.
The difference between data security and any other domain is that data security must be horizontal by nature, spanning across identity, cloud, endpoints, and applications rather than living in any single domain. It’s clear that as data security becomes more complex, point solutions will have trouble keeping up.
In this next section, we'll dive deeper into how Varonis addresses these challenges through their unified platform approach and why they're uniquely positioned as a leader in the AI era.
Why Varonis?
I don't partner with vendors lightly, especially for reports of this gravity. I decided to collaborate with Varonis on this report because after monitoring the data security space for years, they consistently stood out, not only for their product innovation velocity, but also how they stay ahead of emerging threats while solving real problems security teams face today. Their research team is also continuously finding vulns in critical enterprise apps like the recent data inference vuln in Service Now.
Disclaimer
This isn't a sales pitch or a recommendation to buy Varonis. However, to me, they exemplify what the right approach to data security should look like in 2025 and beyond. Whether you choose Varonis or another solution, the principles and capabilities outlined here represent the baseline for data security strategies in the AI era.
Varonis has been doing data security for over 20 years, long before it was trendy. They're the established market leaders with the customer base (i.e., NASA, Lowe’s, and Stryker) and industry recognition to prove it. But unlike many legacy vendors, they haven't gotten complacent. Instead, they've doubled down on their original vision to account for AI and emerging threats while maintaining their core strength in data security. This collaboration made sense because Varonis has been building the future of data security for decades. After spending years helping Fortune 500 organizations navigate similar challenges, I wanted to work with the vendor that's at the forefront of data security.
Inside Varonis: A Leader's Approach to Data Security
The Foundation: Understanding Data Relationships at Scale
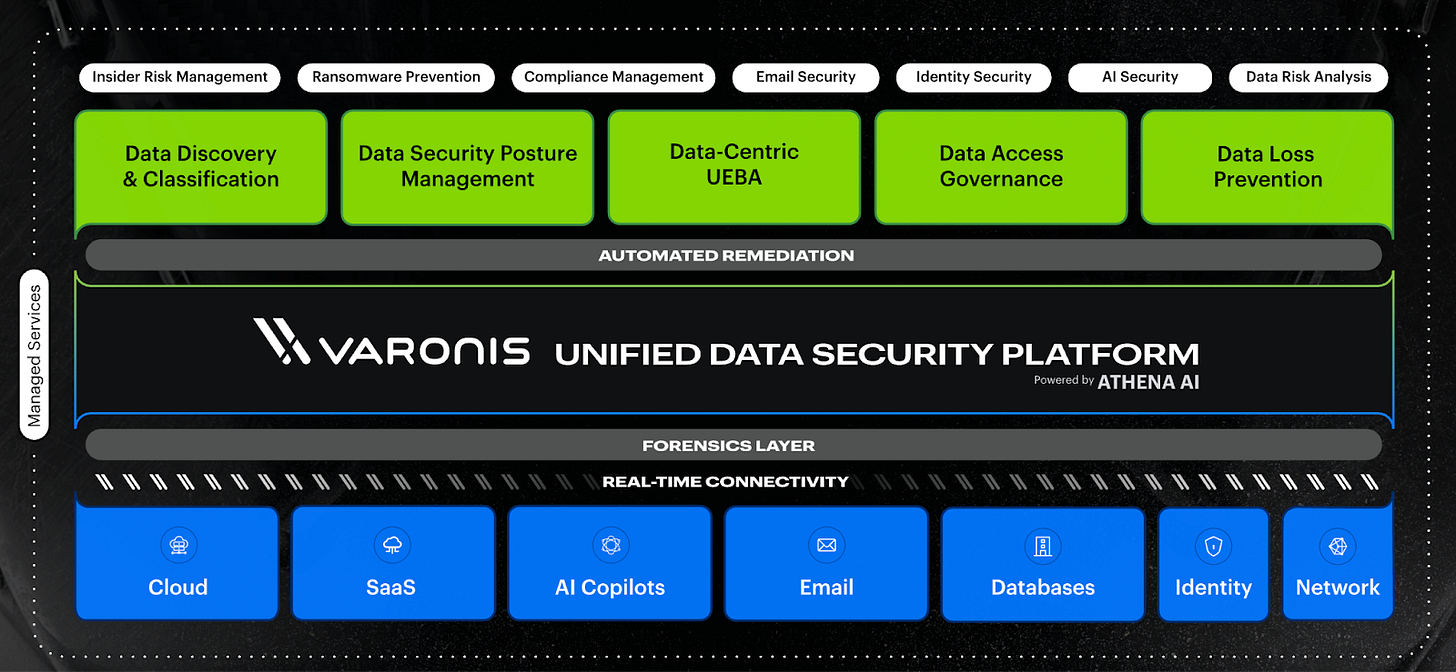
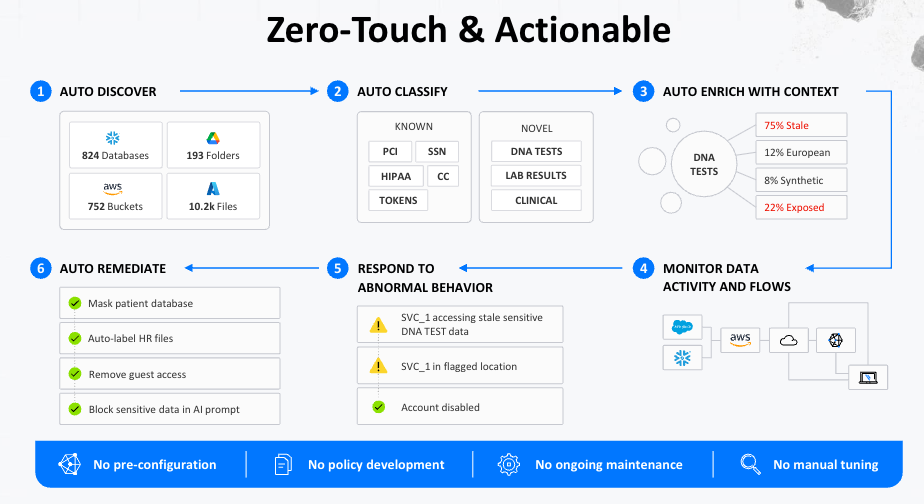
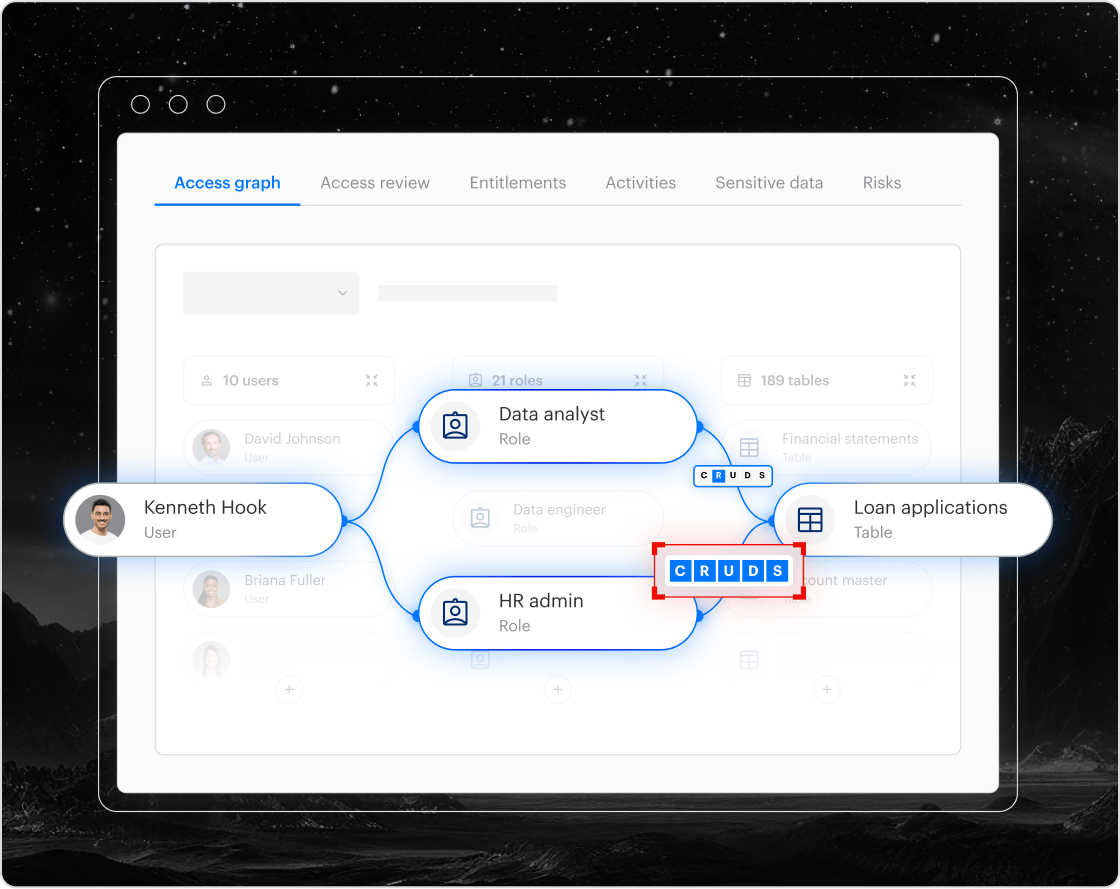
At the core, Varonis built their platform around a simple but powerful idea: you need to inventory and understand the relationships between users, permissions, and data before you can protect anything. Their unified data security platform takes a holistic approach to data security, combining the capabilities needed to stop data breaches and ensure compliance — all with minimal effort from you.
What this means in practice is that the platform knows where sensitive data is stored, on what assets, the asset’s configuration, who can access what, how they got that access, and whether they're actually using it. Taking this approach, they’re able to provide a holistic view across on-prem file shares, cloud storage, databases, email, collaboration platforms, and now AI tools. Everything is connected in one view.
Since many breaches result from attackers leveraging existing accounts and permissions or from misconfigured data stores, having a real-time view of the nuances of your data is critically important.
AI-Powered Classification Built on Two Decades of Experience
Varonis has been doing data classification since before it was cool — over 20 years now. While most vendors still use basic RegEx patterns to find credit cards and SSNs. Varonis leverages proprietary AI/ML approaches (not just GPT wrappers) to bring world-class data classification to its customers.
Their three-tier classification engine combines:
Traditional ML for known patterns (leveraging 20+ years of refinement)
LLMs (GPT-4 models via Azure) for contextual understanding
Compliance rules for regulatory requirements
Incremental scanning (only processing what's changed)
This approach ensures that it knows the difference between a SSN in an HR document versus a sample one being used in a dev environment for testing. Same pattern, completely different risk profile. This contextual understanding reduces false positives and helps teams with prioritization and remediation.
Their "Three Cs" approach is crucial to securing the full data lifecycle. Complete scans with no blind spots, Contextual understanding of data exposure and threats, and Current real-time visibility. Beyond basic pattern matching, it performs sentiment analysis, proximity matching (multiple indicators = higher confidence), and even OCR for images.
Another thing I appreciate is their commitment to privacy and transparency when it comes to AI use. They don't train ML models on customer data, only public and licensed datasets. Plus, the explainable AI provides actual reasoning when someone asks why data was flagged as sensitive, not just a black box decision.
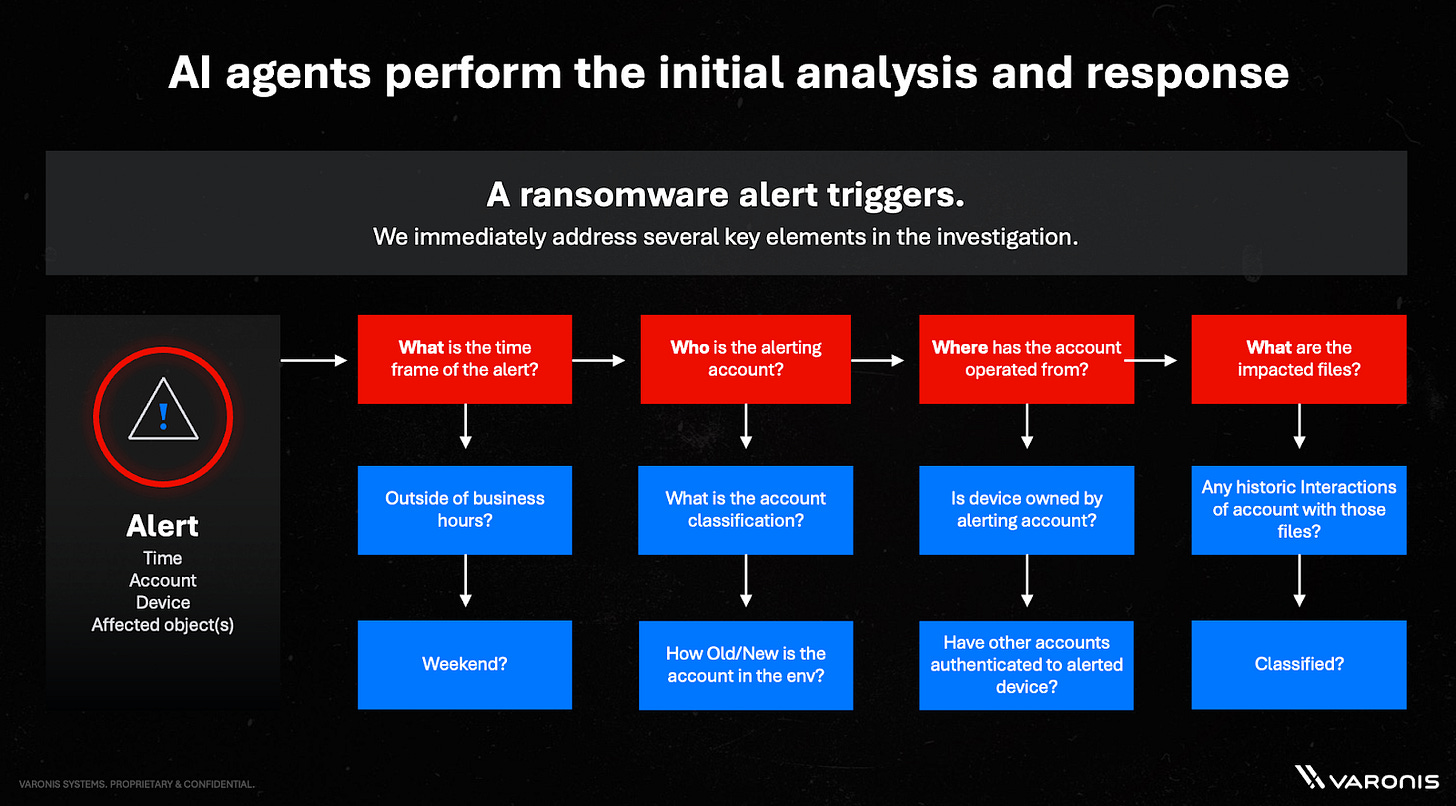
The World’s First Agentic MDDR
Varonis built the first MDDR service that uses AI agents to investigate threats before human analysts see them Traditional vendors that stop at alerting, but Varonis combines AI-powered investigation with human expertise.
How it works:
Anomalous activity triggers AI investigation
AI agents correlate user behavior, peer groups, access patterns, and device info for full context
Only escalates to human analysts when it's a true threat
SLAs + Response times: 30 minutes for ransomware, 120 for everything else.
Having the vendor provide MDDR solves the expertise gap. Most orgs can't hire and retain data security experts who understand these platforms deeply. With Varonis MDDR, you get analysts who live and breathe this stuff, backed by AI that's learning from thousands of deployments. Nobody else in data security offers this combination.
UEBA Built Specifically for Data Threats
Most UEBA tools watch endpoints, cloud, and user activity. Varonis built theirs from the ground up specifically for data security. The platform creates behavioral baselines for every user and device, learning what's normal across your entire data estate. It uses hundreds of ML threat models trained on anonymized data from their full customer base, not just your environment.
Detection coverage spans the full attack chain:
Data-layer threats: Unusual access patterns, permission changes, mass deletion/encryption
Identity threats: Privilege escalation, geo-hopping, impossible travel
Advanced TTPs: Data staging, exfiltration attempts, lateral movement (MITRE ATT&CK)
Endpoint visibility: Via Microsoft Defender and SentinelOne integrations
Full-stack coverage: Data, identity, network, cloud apps - all in one view
This data-centric UEBA helps Varonis catch what others miss. While traditional tools alert on suspicious network connections or atypical login location, Varonis alerts when that same user suddenly accesses sensitive data they've never touched before.
The system enriches every alert with full context — who did what, to which data, how sensitive it was, and whether this behavior matches known attack patterns. This is another massive value add for security leaders and differentiator from other solutions.
Modern-Day Database Monitoring
The 2025 Cyral acquisition transformed Varonis' database coverage. While traditional DAM requires agents, performance hits, and endless configuration, Varonis/Cyral deploys in an agentless fashion without touching your databases.
Comprehensive coverage across every database type:
Traditional: Oracle, SQL Server, MySQL, PostgreSQL
Cloud-native: Aurora, DynamoDB, CosmosDB, BigQuery, Snowflake
Universal connector for future databases
The architecture is elegantly simple: stateless proxies that see everything without impacting performance. It runs on the same Metadata Framework, so database activity connects to file access, identity events, and cloud behavior in one unified view.
Built-in compliance mapping (NIST, HIPAA, SOX, GDPR, PCI) and real-time ransomware detection watches for database-specific indicators like disabling automatic backups, mass data exports, and snapshot deletions.
The key differentiator is that the DAM capabilities are integrated within their full platform.
Automated Remediation That Won't Break Production
Automated remediation has been a controversial topic ever since I started in security. The main concern I always hear is that humans/machines/automation often make mistakes and those mistakes could lead to key system downtime and business disruption.
Think of an automated flow taking down the payments system production Kubernetes cluster because it closed down a critical port due to missing context of a compensating control. That would suck wouldn’t it? Scenarios like this are a key reason why our industry has been hesitant to adopt automated remediation. In the most critical cases, having a human in the loop to make the decision is a non-negotiable.
However, the world is moving toward an automated future and there are smart people with massive R&D budgets working on making automated remediation a reality with minimal friction.
Varonis is achieving this today in real-world environments across multiple domains to secure sensitive data. The key is the simulation, rollback, and multi-engine capabilities:
Multi-Engine Architecture:
File systems: Multi-threaded distributed commit engine
Cloud: Policy automation for SaaS/IaaS configurations
Intelligent decision-making about actual access needs
Automatic rollback if something breaks
Access cleanup: Removes global access groups ("Everyone"), stale users, excessive permissions, dead collaboration links, and risky third-party apps. The ML-powered recommendations mean you're not guessing what's safe to remove.
Data protection: Real-time masking for Redshift, BigQuery, and Snowflake that's role-aware and classification-driven. Automatic labeling through Microsoft Purview integration ensures consistency across platforms.
What makes this different is the intelligence behind it. The system understands who actually needs access based on usage patterns, business context, dependencies between systems, and when to roll back versus push through.
Their approach enables continuous reduction of attack surface without business disruption. Simulation lets you preview impact before committing changes. The distributed architecture means you can remediate at scale.
Huge kudos to Varonis for being one of the only vendors deeply investing in and actually realizing automated remediation.
Securing AI Agents
When deployed without security oversight, AI agents are essentially superusers with API access to everything. While everyone's rushing to deploy Copilot, ChatGPT Enterprise, and Salesforce Agentforce, most haven't figured out the security implications. Varonis has been at the forefront of handling this challenge every step along the way.
Below is how they handle security for some of the most popular AI agents:
Real-time visibility into how agents access, create, and edit Salesforce data
Automatic flagging when sensitive data gets exported
Policy enforcement that prevents data leakage before it happens
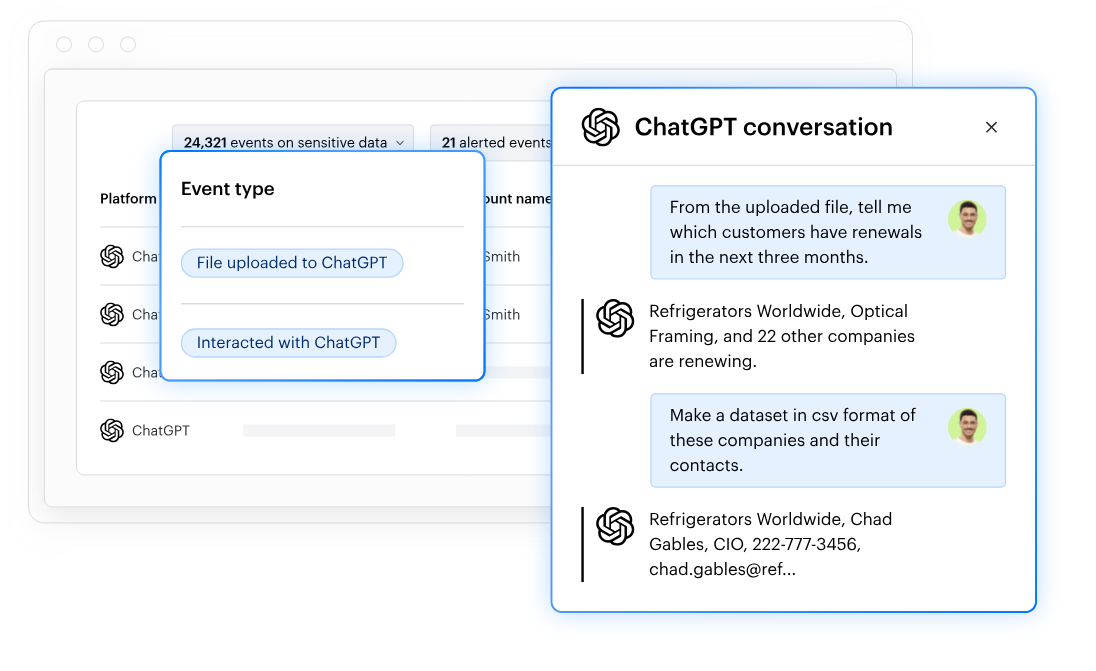
For ChatGPT Enterprise:
Parses every prompt and response for sensitive data
Catches users pasting PII into prompts
Comprehensive audit logs for compliance
Automatic access revocation when risk thresholds are exceeded
Dashboard showing exactly what sensitive data Copilot can access
Automatic lockdown of over-permissive folders
Prompt-level auditing with NIST CSF 2.0 alignment
Full integration with SharePoint, OneDrive, and Teams security
This coverage is integrated with Varonis' existing classification, UEBA, and remediation engines. When Copilot accesses sensitive data it shouldn't see, the platform knows immediately because it already classified that data and baselined normal behavior.
AI agents need the same security controls as human users, plus additional monitoring and governance for their unique risks. Varonis delivers both, which is why I’d say they’re even ahead of most pure play AI security vendors.
Identity Protection – Uniting Identity and Data Security
Most orgs manage identity and data security separately, creating a significant blind spot. Identity tools verify logins but can't see data access patterns. Data security tools monitor file access but lack context about whether that access is normal for that user. Attackers exploit this gap by using valid credentials and moving laterally while appearing legitimate to separate identity and data security solutions.
Varonis’ recent Identity Protection launch addresses this disconnect by unifying identity and data security in one platform. This gives security teams visibility into the identity layer, enabling them to correlate authentication activity with actual data access patterns.
Varonis is the first platform to fully integrate ITDR capabilities with data security, catching MFA bypasses, lateral movement, and suspicious logins while understanding what data is actually at risk. Traditional identity tools stop at "did they log in successfully?" Varonis asks, "What are they doing with that access?"
The Path Forward
The data security landscape has fundamentally changed. Enterprises and consumers now leverage GenAI and agentic AI on a daily basis, while this accelerates innovation it also, unprecedented security risk. Traditional security approaches that segment identity, cloud, data, endpoints, and AI into separate domains have never kept up, and certainly won't moving forward. Organizations need unified platforms that can correlate activity and anomalies across multiple domains and give teams governance capabilities simultaneously.
We're watching AI evolve at breakneck speed, from GenAI assistants to MCP-enabled agents, with quantum computing threats and opportunities landing in the next couple of years. The future of data security must be unified, automated, and adaptive.
The winners in this new landscape will be those who recognize that data security isn't just another security domain. It's the foundation upon which all other security efforts must build. In a world where AI agents can access terabytes of data in milliseconds, where shadow AI proliferates faster than policies can be written, and where traditional perimeters have dissolved entirely, data-centric security is pretty much one of the final frontiers.
Organizations that are proactive in their data security programs in the AI era will thrive. AI is a massive enabler, and the last thing we want to do as an industry or as a security leader is to bottleneck that because we couldn’t keep up. The future of data security is unified.
📧 Subscribe for More 📧
Disclaimer
This report is for informational purposes only and does not constitute a recommendation to purchase Varonis or any vendor solution, nor should it be considered financial or investment advice. While Varonis serves as a case study for modern data security capabilities, organizations should conduct their own assessments to determine which solutions best meet their specific needs.



Awesome in-depth research, thanks for sharing!