📡 Cybersecurity Innovation Pulse #17: Microsoft in the HOT Seat; NATO's $1.1B Security & Defense Fund; Silk Security out of Stealth; 10+ Security Product Announcements
Covering July 27th - August 2nd of 2023
Welcome to Issue 17 of the Cybersecurity Innovation Pulse! I'm Darwin Salazar, your guide to the dynamic world of cybersecurity innovation. Each week, I deliver the latest on product launches, groundbreaking innovations, strategic collaborations, and other developments at the intersection of innovation and cybersecurity. If you find value in these updates, consider becoming a paid subscriber for access to our archive and exclusive posts. Subscribing ensures you receive these insights directly, saving time and keeping you ahead of the curve.
Introduction
As we inch closer to Hacker Summer Camp, the cybersecurity community is buzzing with anticipation. Startups are ready to step out of stealth and into the limelight, researchers are ready to hack all AI things and release their latest tools, and vendors are gearing up to announce their latest products and capabilities. Don't worry about keeping up with the flurry of updates - I’ll be on the ground in Vegas making sure that things don’t get out of hand while keeping track of the most critical and interesting innovation developments.
As for this week’s issue, it’s a hot one so buckle up and get ready for a journey through what’s transpired in the world of cybersecurity and innovation!
Top Stories
Microsoft in the Hot Seat
Microsoft has been hit with severe criticism over its security practices over the past several weeks. Government and industry leaders are labeling the company as "grossly irresponsible" and accusing it of fostering a "culture of toxic obfuscation". Tenable CEO, Amit Yoran, has even come out to say that “Microsoft will downplay, fail to disclose, not prioritize remediating,” … “They just do not have a great passion for [reducing] the risk that their customers incur when using the Microsoft Azure cloud platform.” You can read more of his 🌶️ take here.
The criticism stems from a "critical" cross-tenant vulnerability that could allow unauthorized access to other customers' data and applications. The vuln. was reported by Tenable in March, but the issue was not fully addressed until July, with a complete fix not expected until September 28th. Nearly 4 months later… This comes on the heels of U.S. Senator Ron Wyden calling for a federal investigation on Microsoft for its lax security practices, lack of accountability in the SolarWinds debacle, and more recently the developing story of a Chinese APT group dubbed “Storm-0558” ransacking various U.S. government agencies and high-profile officials. Source 1, Source 2
Not only should the entire industry be watching how this unfolds but also anyone with a vested interest in US national security. This is more serious than what it appears to be on the surface.
NATO's Investment in Security Startups
NATO recently close a $1.1B fund to invest in security and defense technology startups to bolster its capabilities. The NATO Innovation Fund will focus on early-stage companies that can provide innovative solutions to NATO's security challenges. Will be interesting to monitor where the money goes. Source
Cult of the Dead Cow Launches Veilid: The Cult of the Dead Cow (cDc), a renowned hacktivist group, has announced the launch of Veilid, an end-to-end encrypted protocol for app development. Veilid aims to provide users with a way to communicate, share files, and surf the web with the primary goal of protecting the user’s privacy and preventing their data from being sold. The protocol is built from the same digital DNA as the Tor browser and the chat app Signal. Members of the cDc will be going into the details of what Veilid is in their talk next week at DEF CON. If this gains mass adoption as other privacy-focused technologies have (i.e., Tor, Signal), then it would certainly disrupt many companies’ business models. Source
Security Product Innovation
Silk Security has emerged from stealth with $12.5 million in seed funding. The company aims to break down the silos between security and development with an integrated 'find and fix' platform. The platform consolidates alerts from multiple detection systems, performs automatic triaging based on threats to the customer’s environment and assets, and generates a remediation priority scheme for the development team.
To me, the solution feels like a breath of fresh air. It places a heavy emphasis on streamlining remediation with capabilities like automatically assigning issues to asset owners and updating the security team on the remediation status. This is where most security solutions fail customers today. Solutions often detect and surface a slew of security issues but rarely do they go the extra mile to help ease the burden of remediating the most pressing risks. This is why I’m excited to see Silk’s growth and impact on the industry over the coming years. Source
Wiz has added coverage and support for Google Cloud Vertex AI. Their CNAPP solution now helps identify misconfigurations, external exposure, sensitive data, and identity risks behind Vertex AI services. Source
Torq has launched Torq Socrates, an AI agent designed for security operations. The AI agent utilizes large language models (LLMs) to automate critical security activities, alleviating alert fatigue and false positives. Socrates’ capabilities include automated contextual alert triaging, incident investigation, and response capabilities, harnessing intelligence signals from diverse security ecosystems to autonomously drive remediation actions. Torq CEO, Ofer Smadari, states “I anticipate 90% of Tier-1 and Tier-2 tickets will be resolved autonomously.” This would be a major step in the right direction. Source
HYPR has launched HYPR Adapt, a product that provides risk-based, adaptive authentication, allowing organizations to manage identity-related risks and reduce user friction. The product's risk engine analyzes risk signals from numerous sources, including mobile, web, and browser signals, and dynamically adjusts authentication security policies in response. Source
Palo Alto Networks has onboarded its CI/CD Security Module to its Prisma Cloud CNAPP offering. This comes about 7 months after the company acquired Cider Security, a CI/CD security start-up. The module offers automated security checks, threat prevention, and compliance enforcement that is in line with the OWASP Top 10 for CI/CD security. Pretty neat solution in my opinion. Source
SpecterOps has updated its BloodHound tool, a popular solution for visualizing Active Directory (AD) environments. The new version, BloodHound Enterprise 5.0, introduces a slew of enhancements including a new graph database, improved performance, and a redesigned user interface. The latest version will be released on Aug. 8th during BlackHat. The tool is a staple used by both red teams and blue teams to identify and analyze potential attack paths in AD environments. source
BreachRx has unveiled Cyber RegScout, a product designed to automate cybersecurity, privacy, and data protection regulatory analysis. The tool provides access to a global regulatory library containing details, exceptions, and insights for compliance with over 180 laws. The library is updated in real-time, allowing organizations to stay current with compliance requirements. Source
Menlo Security has introduced two new tools to block advanced browser-based threats. The company's new capabilities are designed to protect against phishing, ransomware, and other web-based attacks, providing a safer browsing experience for users. The tools leverage Menlo Security's Isolation Core™ technology, which separates the browsing environment from the endpoint to prevent any potential threats from reaching the user's device. Source
Securonix has onboarded a ChatGPT integration that will allow its product to investigate and respond to threats. The integration allows ChatGPT to autonomously investigate potential threats, analyze data, and take appropriate action based on the findings. This enhancement aims to reduce the workload of security analysts and improve the efficiency of threat detection and response. I covered a few of these use cases in May in the Demystifying the Generative AI and LLM Buzz in Security Products report. Source
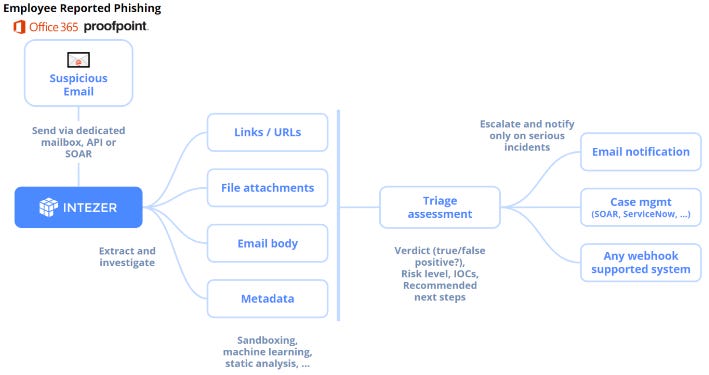
Intezer has launched Automated Phishing Investigation, a new feature designed to automate the analysis and classification of suspected phishing emails. The feature integrates into employee-reported phishing workflows, streamlining the investigation of suspicious emails and notifying security teams only of items that require attention. It provides a clear verdict, priority, classification, and context for each suspicious email, allowing teams to quickly understand the nature of the threat and take appropriate action. Source
Abbey Labs, an identity access and management startup, has secured $5.25 million in seed funding led by Point72 Ventures LP. The company, founded by former Okta and Stripe employees, Arvil Nagpal and Jeff Chao, offers a platform that helps companies secure and automate employee access to sensitive data infrastructure such as Databricks, Kafka, and MongoDB. The solution meets engineers where they are by enabling them to define IAM policies and workflows via Abbey’s Terraform provider. This is key. Source
Conclusion
And that's a wrap for this week, folks! Your feedback is the fuel that keeps this newsletter going, so don't hesitate to let me know what you loved, liked, or would like to see improved. If you found value in this issue, why not share it with a friend or consider becoming a paid subscriber? Each week, I sift through over a thousand headlines to bring you the most impactful stories that are driving innovation in cybersecurity. Your support lets me know that this work is making a difference.