TCP #112: AWS re:Invent Roundup; CRWD Earnings; Golden Agents; and More
What's hot in security🌶️ | Nov. 26th - Dec. 3rd, 2025
Welcome to The Cybersecurity Pulse (TCP)! I'm Darwin Salazar, Head of Growth at Monad and former detection engineer in big tech. Each week, I bring you the latest security innovation and industry news. Subscribe to receive weekly updates! 📧
Vega: Security Analytics Mesh for AWS S3
Get all the benefits of a flexible, cost-efficient architecture without the headaches of data migrations and normalization. Security Analytics Mesh, aka SAM, delivers full visibility and detection by analyzing your data in place. (See ya, egress fees.)
SAM was built for distributed data architectures to give you federated search, detection, and investigation across all your S3 buckets, data lakes, and SIEMs.
At AWS re:Invent? Visit booth #1928 for hot dogs, magic, and live demos!
Howdy! 👋 Across AWS re:Invent (all announcements covered in Future of Security section), all the shots fired during CrowdStrike’s earnings call, and everything in between we have A LOT to cover.
Before we dive in, two notes on upcoming events we’ll be at:
Cyversity Austin Awards Ceremony and Gala is tomorrow. Get fly and come hang if you’re in town! It’s free. Link to register is here.
CyberMarketingCon is next week! Let’s grab coffee or get into something fun if you’re in town. I’ll also be presenting on technical writing. Details for my talk + RSVP link here.
Side note: This is a very long TCP edition so if you’re reading via email, you’ll probably get cut off halfway through. To avoid this, jump to the web version.
Quick plug: Q1 + Q2 2026 sponsorship slots are now open, including RSAC weeks. If you’re interested in getting in front of 20K+ security professionals, reach out to sponsorships@cybersecuritypulse.org
Alright, let’s dive in!
TL;DR 📰
📊 CrowdStrike and Okta post strong quarters, shots fired — CRWD hits $4.92B ARR; Okta is going after agent identities
🎯 Golden Agent attacks are coming — Gunnar Peterson warns delegated OAuth tokens make AI agent proxies the new Golden Ticket target
🔓 Mixpanel breach leaves more questions than answers — OpenAI confirms data stolen, terminates Mixpanel
🧟 Caleb Sima warns of “zombie tool” crisis — AI makes building easy but operating hard; abandoned internal tools become technical debt
🍺 Heineken CISO on business-aligned security — “How does MFA help me sell more beer?” is the test for executive buy-in
🧠 AWS launches Security Agent for AppSec — AI-powered design reviews, code scanning, and on-demand pen testing in hours instead of weeks
🔑 AWS releases IAM Policy Autopilot — Open source MCP server generates IAM policies from your actual code; no hallucinations, runs locally
⚙️ Amazon Bedrock AgentCore adds math-based guardrails — Policy, Evaluations, and Episodic Memory for governing AI agents deterministically
🧬 Netskope adds MCP security controls — Discovery, risk scoring, and DLP for Model Context Protocol traffic
💰 ServiceNow to acquire Veza for $1B+ — Identity security play for governing human, machine, and AI agent access
🧪 Wiz launches SAST with cloud context — Correlates code vulns with actual deployment; AI-assisted remediation via PR comments
💵 Zafran raises $60M Series C — Agentic exposure management with AI-powered owner identification and exploitability scoring
🎙️ Axonius CEO on why boring problems build unicorns — Dean Sysman bet on cyber asset visibility after his first startup failed; hit $100M ARR in under 5 years
🔌 Scanner.dev launches MCP server — Natural language threat hunting and autonomous 24/7 investigation workflows
⚒️ Picks of the Week ⚒️
CrowdStrike and Okta earnings and what they’re betting on next
CrowdStrike reported a very strong Q3 FY26 earnings yesterday. Quarterly rev. came in at $1.23B (up 22% YoY) and clocking a $4.92B ARR (up 23% YoY). The earnings call had a lot of nuggets that hint at $CRWD’s long-term strategy and where they see the industry heading.
1. Becoming the “Operating System of Cybersecurity” Is their Strategy
NG-SIEM is now positioned as the foundation — not just a product.
George Kurtz, CEO: “Falcon Next-Gen SIEM is the foundation of our platform, turning CrowdStrike into our customers’ operating system for cybersecurity.”
2. First SIEM Vendor in AWS Quick Start
Announced at re:Invent, CrowdStrike recently became the first security partner in AWS’s enhanced Quick Start program, connecting Falcon NG-SIEM directly to CloudTrail, Security Hub, and GuardDuty with guided onboarding.
Lower friction to adopt = product-led growth motion with AWS’s customer base.
They also announced federated search on AWS using Athena.
Full post: Transform AWS Security Operations with Falcon Next-Gen SIEM
3. Network Appliances Are Next
F5 partnership puts Falcon sensor on BIG-IP appliances.
Kurtz: “This will create a working model that will open it up to other appliance vendors.”
CrowdStrike EDR is expanding beyond endpoints and into network appliances #huge.
4. The Flex Model Is Working
$1.35B ARR (+200% YoY) from Flex accounts. 200+ “reflex” customers, 10 at 2x+ their initial subscription. Kurtz expects Flex to become the licensing standard.
5. Agentic AI = Their Largest Opportunity
Kurtz framed AI as both the threat and the growth driver: “AI adoption necessitates the right cybersecurity. It necessitates CrowdStrike.”
Charlotte AI is now FedRAMP High approved as the “agentic SOC orchestrator.”
While Q3 was financially strong, I think it laid the groundwork for a great next few quarters. Not to mention their recent Onum and Pangea acquisitions.
CRWD Earnings transcript - https://seekingalpha.com/article/4849578-crowdstrike-holdings-inc-crwd-q3-2026-earnings-call-transcript
Spicy nuggets - Kurtz called out performing multiple Wiz replacements in q3 🌶️
Okta: Solid Quarter, Positioning for Agent Identity
Okta also reported earnings this week. $742M revenue (+12% YoY), beat estimates, raised guidance. Okta wants to be the identity layer that governs AI agents.
Runtime protection that keeps pace with your release cycle
Impart gives teams real-time visibility and enforcement across web traffic, APIs, and AI interfaces.
Protect what comes in, what happens inside, and how your app runs.
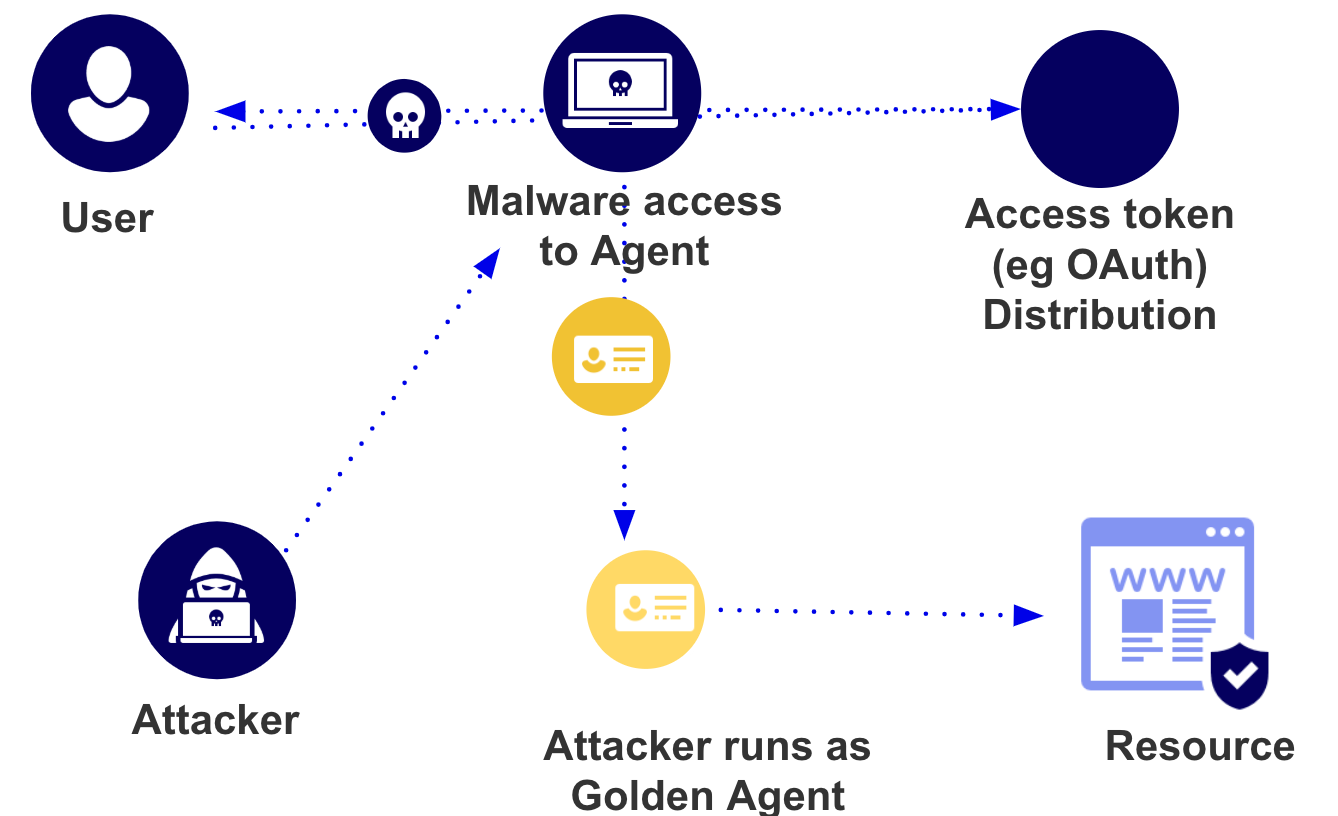
Gunnar Peterson: “Golden Agent” Attacks Are Coming
Gunnar Peterson (CISO at Forter + IANS advisor) argues security teams should prepare for Golden Agent attacks — the agentic AI equivalent of Active Directory’s decades-old Golden Ticket problem.
When users delegate access to AI agents via OAuth tokens, the agent proxy becomes the target. Attackers don’t need credentials if they can compromise the intermediary that already has delegated access.
Why it’s worse than Golden Ticket:
Golden Ticket targeted one vendor (Microsoft). Golden Agent spans dozens of agent vendors with inconsistent security.
Lateral movement is a feature, not a bug — that’s what agents are designed to do.
Least privilege alone won’t cut it. Robust identity-layer anomaly detection (velocity checks, suspicious delegation requests, anomalous access patterns) will be essential.
A data breach at analytics giant Mixpanel leaves a lot of open questions
Mixpanel detected a breach on November 8, disclosed it in a bare-bones blog post right before Thanksgiving (>.<). CEO Jen Taylor hasn’t responded to press inquiries. OpenAI confirmed what Mixpanel wouldn’t say explicitly: customer data was stolen.
What we know:
OpenAI was affected—their developer documentation users had names, emails, approximate location (from IP), and device data exfiltrated
OpenAI terminated Mixpanel as a result
Mixpanel has 8,000 corporate customers, each with potentially millions of end users
Total impact unknown; Mixpanel may not even know yet
Dig Deeper:
The First Platform to Eliminate Manual CVE Work 🎯
A critical CVE hits an app dependency. Security flags it, AppSec escalates, engineering groans because the fix usually means risky version upgrades or waiting for an upstream patch that may never come. Teams stay pinned to certain versions for compatibility. Upgrading can break apps and slow delivery, leaving you stuck between security, stability, and velocity.
This ends today.
Root Library Catalog gives you an end-to-end way to secure open-source dependencies from discovery to verified installation. It provides a searchable catalog of Root-maintained secure package versions that plug into existing workflows with authenticated, ecosystem-native integrations.
Search the catalog, see which CVEs are remediated, and install through your package manager. Enterprises can point their registry to Root’s trusted mirror for automatic secure delivery. Root fixes CVEs in pinned versions without forced upgrades or disruption.
Caleb Sima x Mark Hillick: The “Zombie Tool” Crisis Is Coming
Caleb Sima (CSA AI Safety Chair, ex-Robinhood CSO) and Mark Hillick (CISO, Brex) warn that AI-accelerated “vibe coding” is creating a technical debt timebomb.
AI makes building trivially easy, but hasn’t solved the cost of operating. Which results in “zombie tools” — internal projects that become critical infrastructure, then get abandoned when the builder leaves or gets promoted.
Why it’s happening:
The 80/20 trap — AI gets you to 80% fast; the last 20% (reliability, edge cases) still takes 80% of the effort
Career-driven development — building gets you promoted; buying a vendor doesn’t
Corporate AI mandates — “Use AI, we will fund AI” incentivizes building over solving
Eval framework: Before building, ask: (1) Is this problem unique to us? (2) Is it secret sauce? (3) Does the market fail to solve it? If no to all three — buy, don’t build.
Heineken CISO on Business-Aligned Security
Marina Marceta’s interview is a masterclass in translating security speak for the C-suite.
Her core test: “How does MFA help me sell more beer?” If you can’t answer that, you’ve already lost the room.
Top takeaways:
Speak in business outcomes, not CVEs. “This could cost us X million EUR” lands. “Critical zero-day” doesn’t.
Use real incidents as leverage. Peer company breaches make abstract risk concrete. Execs pay attention when it’s someone they know.
Guardrails, not straitjackets. Set global principles and baseline controls, then let regions adapt. Requires mature monitoring and culture to pull off.
Bake security into KPIs. Top-down mandates fail. Tie security to performance reviews and project planning—then celebrate teams who get it right.
Develop leaders, not just technicians. Titles and certs aren’t enough. Give juniors stretch assignments mixing tech and business. Build a culture where “I don’t know” is strength, not weakness.
Worth the full read if you’re a security leader struggling with executive buy-in, or an aspiring leader thinking about what skills actually matter for the next level.
🎙️ From Failed Startup to $2.6B: The Case for Boring Problems
Axonius CEO Dean Sysman on why he deliberately chased a “boring” problem after his first startup failed, and how betting on cyber asset visibility (instead of something flashy) got him to $100M ARR in under five years and a $2.6B valuation.
🔮 The Future of Security 🔮
AWS re:Invent Highlights
AWS premier annual conference is taking place this week and of course, with that comes fireworks and a slew of announcements. It’s all too much for me to cover so I’ll touch on my top 3 and include the rest of announcements in a list.
➡️ Here’s the link for all AWS announcements incl. non-security.
AWS Application Security Agent
AI-powered AppSec agent that reviews designs, code, and runs on-demand pen tests. Context-aware to your specific environment.
Design-time findings: Analyzes architecture docs and specs against your security policies before dev
Custom pen testing: Builds attack plans from your security requirements, design docs, and source code
Auto-remediation: Can submit PRs with fixes (human approval required)
Timeline claim: Results in hours vs. weeks of scheduling back-and-forth
MCP server that analyzes your code and generates IAM policies from actual SDK calls. Free, runs locally, no AI hallucinations—uses deterministic code analysis.
Integrations: Works with Kiro, Claude Code, Cursor, Cline
Languages: Python, TypeScript, Go
Bonus feature: Analyzes Access Denied errors and proposes fixes
More AWS re:Invent news ⬇️
AWS Security Hub now generally available with near real-time analytics and risk prioritization
Unit 42 Incident Response Retainer for AWS Security Incident Response
AWS unveils EKS capabilities to reinvent Kubernetes operations as AI workloads surge
Announcing replication support and Intelligent-Tiering for Amazon S3 Tables
AWS Introduces DNS Failover Feature for Its Notoriously Unreliable US East Region
CrowdStrike Leverages NVIDIA Nemotron in Amazon Bedrock to Advance Agentic Security
Salt Security launches ‘Ask Pepper AI’ to simplify API risk analysis
Amazon Bedrock AgentCore Updates
Three new capabilities for governing AI agents, headlined by math-based guardrails that help prevent prompt injection.
Policy: Natural language rules enforced between agent and tools via automated reasoning—deterministic.
Evaluations: 13 pre-built evaluators plus custom options, alerting when agents start failing quality checks
Episodic Memory: Trigger-based recall to work around context window limits
AI Security
Netskope adds MCP security controls to protect enterprise AI agents
Netskope has added security controls for Model Context Protocol (MCP). Netskope already sits in the data path between users and cloud/SaaS apps doing DLP and policy enforcement; MCP traffic is prety much just another protocol to inspect.
Capabilities:
Discovery — find MCP servers and clients on your network
Risk scoring — assess security posture of MCP-enabled tools
Policy controls — define which agents access which resources; block unapproved by default
DLP — inspect MCP sessions for sensitive data access
Application Security
Introducing Wiz SAST: Where Code Risk Meets Cloud Context
Wiz launched Wiz SAST (public preview), adding static code scanning to its ASPM platform. Correlates code vulns with actual cloud deployment to surface only what’s exploitable. Ingests findings from Checkmarx, Semgrep, Snyk, and enriches them with the same cloud context.
Also notable: AI-assisted remediation lets devs comment #wiz remediate in PRs for auto-generated fixes.
Cloud Security
CrowdStrike Unveils Real-Time Cloud Detection and Response Innovations
CrowdStrike announced new Cloud Detection & Response capabilities at AWS re:Invent, claiming to cut detection latency from 15+ minutes to seconds.
What’s new:
Streaming detection engine — processes logs in real-time (built on OverWatch threat hunting tech)
Expanded cloud IOAs — privilege escalation, malicious CloudShell, unified with endpoint/identity detections
Automated response — SOAR-based actions disrupt threats without waiting for analyst intervention
More Cloud Security news ⬇️
Data Security
Falcon Data Protection for Cloud Extends DSPM into Runtime
CrowdStrike announced GA of Falcon Data Protection for Cloud, which extends DSPM into runtime using eBPF-based monitoring.
Identity and Access Management
ServiceNow to acquire Veza in move to expand identity security portfolio
ServiceNow is acquiring Veza for a reported price of $1B+.
What Veza does: The Veza Access Graph maps all identities (human, machine, third-party) and their permissions across cloud, SaaS, on-prem, and custom apps.
Why ServiceNow wants it: Zavery (President/COO): “In the era of agentic AI, every identity — human, AI agent, or machine — is a force for enterprise impact. It’s only when you have continuous visibility into each identity’s permissions that you can trust it.”
Funding context: Veza raised $235M total (NEA, Accel, GV, Sequoia). $1B+ exit on $235M raised is a strong outcome.
ServiceNow already has a strong security portfolio and a hook into Fortune 500 environments, I think Veza will open up identity security biz for them + be rolled into their agentic AI offerings with secure agents being a compeititve advantage.
More IAM news ⬇️
Security Operations
Scanner.dev Launches MCP Server for AI-Powered Investigations
Scanner.dev released an MCP server that connects AI agents directly to security data lakes — enabling natural language threat hunting, AI-assisted detection engineering, and autonomous 24/7 response workflows.
Use cases:
Interactive investigations — natural language queries, iterative refinement (2-3 hour manual investigation → 5 minutes)
Detection engineering — AI helps write detection rules
Autonomous workflows — AI agents investigate alerts at 2 AM, create tickets, notify Slack, no human needed
Vulnerability Management
Zafran Security nabs $60M for its vulnerability management platform
Zafran Security closed a $60M Series C led by Menlo Ventures (Sequoia, Cyberstarts participating). ARR has tripled since their last raise; valuation doubled.
What Zafran does: Aggregates vuln data from your existing security tools, normalizes it, dedupes, and generates remediation guidance.
New product — Agentic Exposure Management:
Zero-day triage: Checks SBOMs against new exploits, generates temp mitigations
Owner identification: AI finds who’s responsible for a vulnerable system (a multi-hour task in large orgs)
Exploitability scoring: Filters out vulns that aren’t actually reachable
More Vulnerability Management news ⬇️
Interested in sponsoring TCP?
Sponsoring TCP not only helps me continue to bring you the latest in security innovation, but it also connects you to a dedicated audience of 20,000+ CISOs, practitioners, founders, and investors across 125+ countries 🌎
Bye for now 👋🏽
That’s all for this week… ¡Nos vemos la próxima semana!
Disclaimer
The insights, opinions, and analyses shared in The Cybersecurity Pulse are my own and do not represent the views or positions of my employer or any affiliated organizations. This newsletter is for informational purposes only and should not be construed as financial, legal, security, or investment advice.







Exceptional roundup covering the strategic inflection points in enterprise security right now. The CrowdStrike earnings analysis particularly resonates because it shows how Next-Gen SIEM is transitioning from being just another security product to becoming the platform layer that everything else integrates into.
The AWS Quick Start partnership is a massive PLG play that most people will overlook. By reducing onboarding friction for NG-SIEM directly within the AWS console, CrowdStrike essentially turned AWS's customer base into a distribution channel. When you combine that with federated search via Athena, they're not just selling SIEM anymore, they're embedding themselves as the defacto query interface for AWS security data.
Gunnar's Golden Agent framing is spot on and underappreciated. The OAuth delegation model creates a fundamentally different attack surface than traditional Golden Tickets because agents are designed for lateral movement by default. You can't just apply least privilege and call it solved, you need continuous behavioral anomaly detection at the identity layer to catch when delegation patterns suddenly change. Most enterprises aren't ready for this, they're still treating AI agents like they're just anothr SaaS integration.