TCP #117: Mandia is Building Again, AI Prompt Injection Season Continues, and China Bans Western Security
What's hot in security🌶️ | Jan 14th, '26 - Jan. 21st '26
Welcome to The Cybersecurity Pulse (TCP)! I'm Darwin Salazar, Head of Growth at Monad and former detection engineer in big tech. Each week, I bring you the latest security innovation and industry news. Subscribe to receive weekly updates! 📧
Feeling the ground shift under enterprise security?
NHIcon 2026 on Jan. 27 is a practitioner-driven virtual event on agentic AI and what changes when software stops waiting for instructions.
You’ll hear from Phil Venables (fmr. Google Cloud), Misam Abbas (LinkedIn), and Jason Clinton (Anthropic), alongside 20+ other practitioners breaking down where existing controls fail, how agent behavior changes risk, and what it takes to regain leverage in real production environments.
Want to sponsor the TCP newsletter? Learn more here.
Howdy! 👋 I hope you’re having a great week!
Is it me or is this the year going by super fast?.. In any case, I’m just getting back from visiting Puerto Rico for the closing celebrations of their holiday season called “Fiestas de la Calle San Sebastian”. Beautiful cultural display. Hiiiiighly recommend going if you get the chance!
Now, onto security stuff, which is what you’re all here for in the first place. Two of my favorite sponsors I’ve had the joy of working with are hosting free virtual conferences covering two of the most crucial security domains in 2026.
Aembit is hosting the NHICon focusing on securing Agentic AI on Jan. 27th. Super stacked speaker lineup including fmr. CISO at Google Cloud (Phil Venables), DCISO at Anthropic (Jason Clinton), and many leading security operators. It’s a must attend event for anyone doing enterprise security in any capacity. You can register here.
Cycode is hosting their Product Security Summit on Jan. 28th, a free virtual con focused on securing software in the AI era. Speaker lineup includes Rinki Sethi (fmr. CISO at Rubrik, Twitter), and security leaders from HackerOne, Nucleus Security, Cloudflare and more. If you’re touching AppSec in any capacity, this one's worth the 2-3 hours. Register here.
And of course, I have to plug the stuff we’ve been working on at Monad! My pal Nathan Koester, Staff SecEng at Ironclad, recently wrote up a piece on the data engineering gap in security which hints at where SecOps is headed in 2026, from a practitioner’s perspective. Read further here.
Okay, now onto this past week’s news!
TL;DR 🗞️
Mandia launches Armadin with $165M for AI red-teaming — Per SEC filing, Mandiant founder raised way more than the $24M seed reported by WSJ; Ping Li (Accel) and Jake Seid (Ballistic) on board
💀 ServiceNow BodySnatcher enables full platform takeover — CVE-2025-12420 (CVSS 9.3); hardcoded creds + email-only account linking = impersonate any user, weaponize AI agents
🧭 Wiz drops agentic browser security year-end review — Rami McCarthy’s “Autonomy × Access” matrix is a gem 💎
🗓️ Gemini calendar prompt injection bypasses privacy controls — Miggo research find dormant payloads in invite descriptions exfiltrate meeting summaries
📤 Cowork file exfiltration via prompt injection — PromptArmor shows Claude Cowork can upload files to attacker accounts
💥 CrashFix fake ad blocker delivers ModeloRAT — KongTuke actor clones uBlock Origin Lite; crashes browser, prompts fake scan; targets domain-joined hosts only
🎤 Jen Easterly named RSAC CEO — Former CISA Director lands at RSA Conference; eyes international expansion
🦄 Aikido hits $1B valuation with $60M Series B — Fastest European cybersecurity unicorn; DST Global led; 100K+ teams, 5x revenue growth
⛓️ Delinea acquires StrongDM — PAM meets just-in-time authorization for devs and AI agents; deal terms undisclosed
🚫 China bans US and Israeli security software — 15+ vendors including CrowdStrike, Palo Alto, Wiz, Check Point; most report minimal China exposure
📡 Reco launches device inventory — Consolidates MDM, EDR, IdP into single view; flags unmanaged devices accessing corporate SaaS
⚔️ Novee launches with $51.5M for AI pentesting — YL Ventures led; claims 90% accuracy vs. ~65% for frontier LLMs; competes with XBOW
⚛️ Project Eleven raises $20M for post-quantum crypto — $120M valuation; migration tools for Bitcoin/Solana to quantum-resistant cryptograph
⚒️ Picks of the Week ⚒️
Kevin Mandia Is Building Again

The man who built Mandiant and sold it to Google for $5.4 billion is back.
Kevin Mandia has launched Armadin (notably no website), a startup using AI to automate red-teaming and penetration testing. The company came out of stealth in mid-December with a $24M seed from Ballistic Ventures — the cybersecurity-focused VC firm Mandia co-founded.
But here’s what most outlets haven’t caught onto: An SEC Form D filed January 13th shows Armadin has already closed $165 million from 28 investors. The reported talks with Accel, GV, and Kleiner Perkins clearly went well.
“The cheapest way to build your defense is to actually hit it with the best offense and refine it,” Mandia told the WSJ.
The economics are striking: what used to cost $20-30K in human pentesting time will take 3-5 minutes and cost hundreds of dollars. This was proven out by the recent ARTEMIS study which signals to improving attack economics + efficacy.
The team: Mandia has teamed up with former Google engineers Travis Lanham and David Slater, plus Evan Pena, a longtime leader of Mandiant’s red team. The SEC filing also reveals board seats for:
Ping Li — Accel Partner with board seats at Tenable, Snyk, Sysdig, and Illumio
Jake Seid — Ballistic Ventures Co-Founder/GP
When the guy who uncovered APT1 and led the SolarWinds response decides the future is a certain category, it’s worth paying attention. 2026 is already off to a hot start.
Also, key to note that this comes as XBOW raised a $75M series B last June and Novee, a new entrant, raised $51.5M through Series A (covered lated in this issue). Mandia is coming in w/ 2-3x more funding than these direct competitors. XBOW does have the time lead though.
Shoutout to Pramod Gosavi for the SEC tip on this!
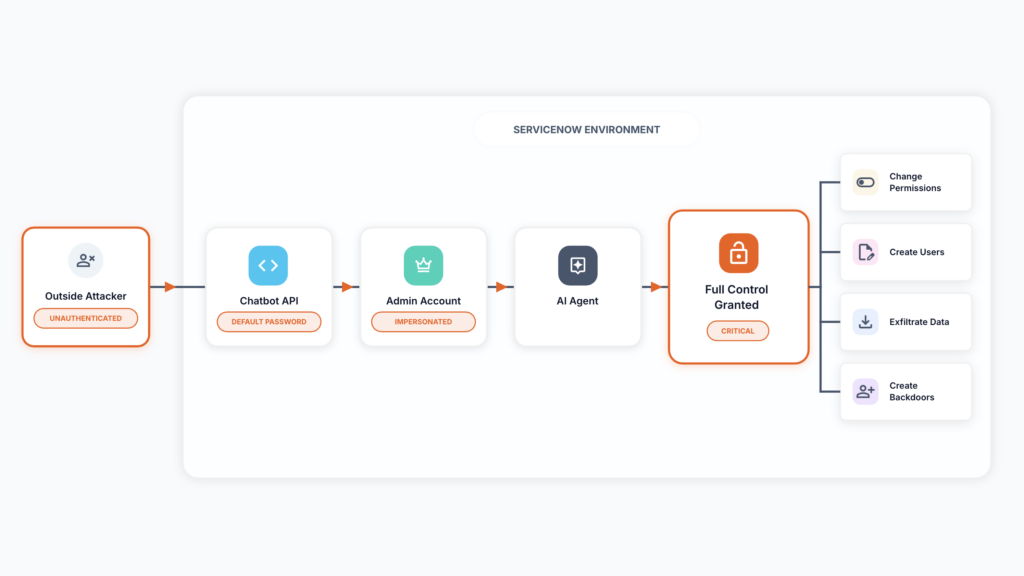
ServiceNow “BodySnatcher” Enables Full Platform Takeover via AI Agents
AppOmni’s Aaron Costello discovered CVE-2025-12420 (CVSS 9.3): a hardcoded credential (”servicenowexternalagent”) shipped to all instances plus email-only account linking allowed attackers to impersonate any user, bypass MFA/SSO, and weaponize ‘Now Assist AI’ agents to create admin backdoor accounts.
Significant vuln given the hardcoded creds across all instances and the privilege escalation path to full platform takeover. ServiceNow serves 85% of the Fortune 500, with deep integration into HR, security, and customer systems making it a goldmine for attackers. ServiceNow patched in October but only disclosed last week. Patched in October 2025, disclosed last week. Even vendors with 8/9-figure security budgets are shipping hardcoded creds. Plan accordingly.
AI is Only as Smart as its Context: Building a Semantic Graph for Security
AI can’t secure what it doesn’t understand. The Context Intelligence Graph is the connective tissue that unifies AST, SSCS, and ASPM into a single, coherent view. It provides the “meaning” AI agents need to sense, reason, and act safely across your code and cloud. Stop reacting to isolated alerts and start managing causality.
Register for the Product Security Summit to see the future of AI-native security.
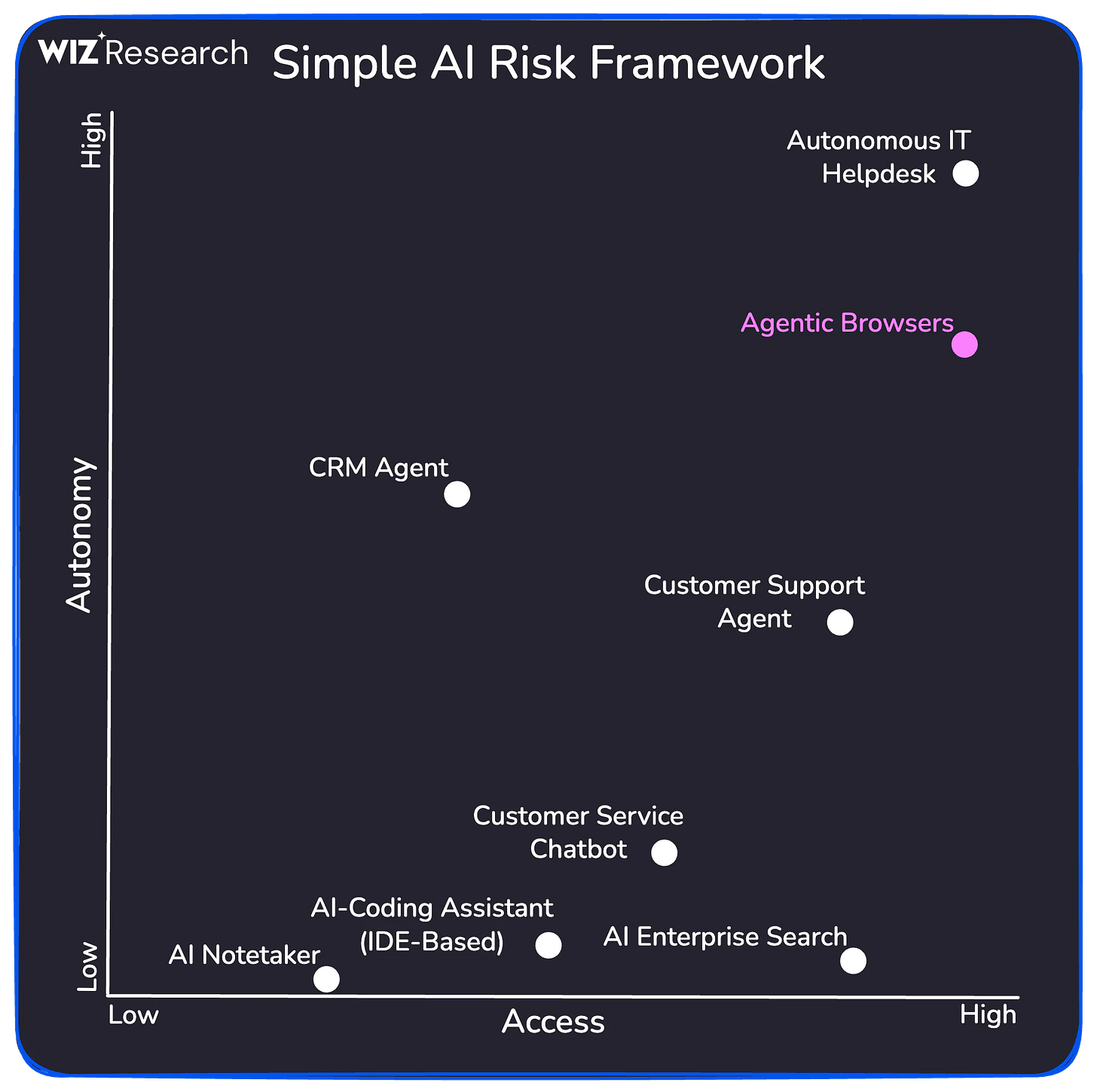
Agentic Browser Security: 2025 Year-End Review
2025 was a terrible year for agentic browsers. At one point it seemed like critical vulns surfaced each week. In this post, Rami McCarthy delivers a stellar year-end review cataloging prompt injection vulns across agentic browsers likw ChatGPT Atlas, Perplexity Comet, Fellou, and others. This report builds well off of Gartner’s recent recommendation for CISOs block AI browsers outright.
Browser vendors are converging on human-in-the-loop (HITL) + RL + secondary LLM critics as layered defense (enumerated in a chart in the report). The “Autonomy × Access” matrix really puts things into perspective as it’s a super simple mental model to understand the risk profile of these browsers.
Autonomous tooling goes against most of what security has been preaching over the past few decades (i.e., zero trust). However, security leaders must find a way to securely onboard and enables these technologies or risk falling behind to competitors who do adopt it. As Rami put it: “For most everyday use cases, agentic browsers don’t yet deliver enough value to justify their current risk profile.” Agentic browsers + their use cases will only get better so securing this vector may become a non-negotiable soon.
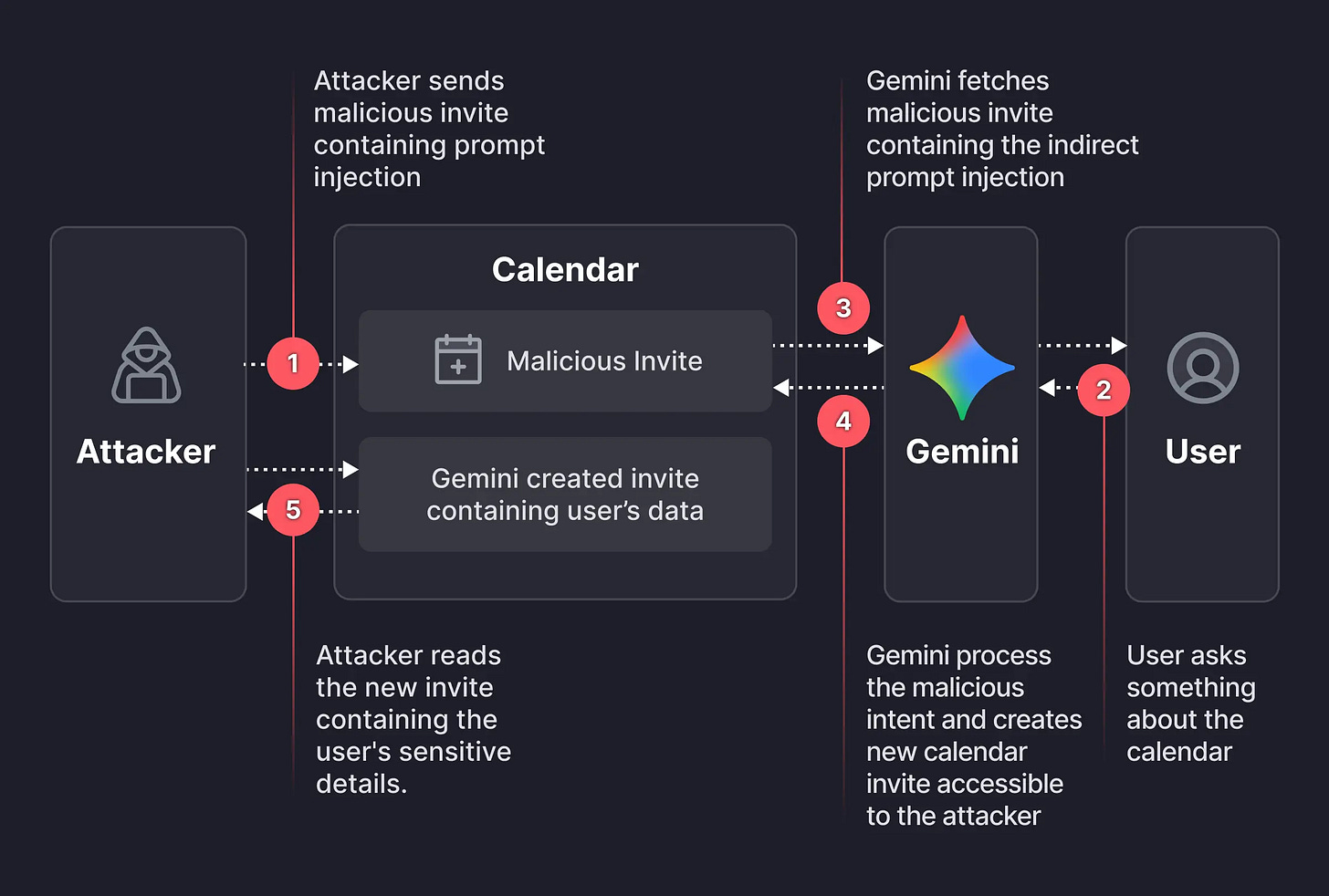
Gemini Calendar Prompt Injection Bypasses Privacy Controls
Miggo researchers discovered attackers can embed dormant prompt injection payloads in Google Calendar invite descriptions. When users ask Gemini about their schedule, the AI executes hidden instructions, exfiltrating private meeting summaries into new calendar events visible to attackers.
This builds on SafeBreach’s August 2025 research showing Gemini calendar exploits could trigger Google Home actions. Same underlying pattern: AI assistants pulling untrusted content from shared resources is a structural weakness that opens the door to prompt injection. Not a “everything is on fire” vuln, but another data point for why Gartner is telling CISOs to block or exercise caution w/ AI assistants from sensitive workflows.
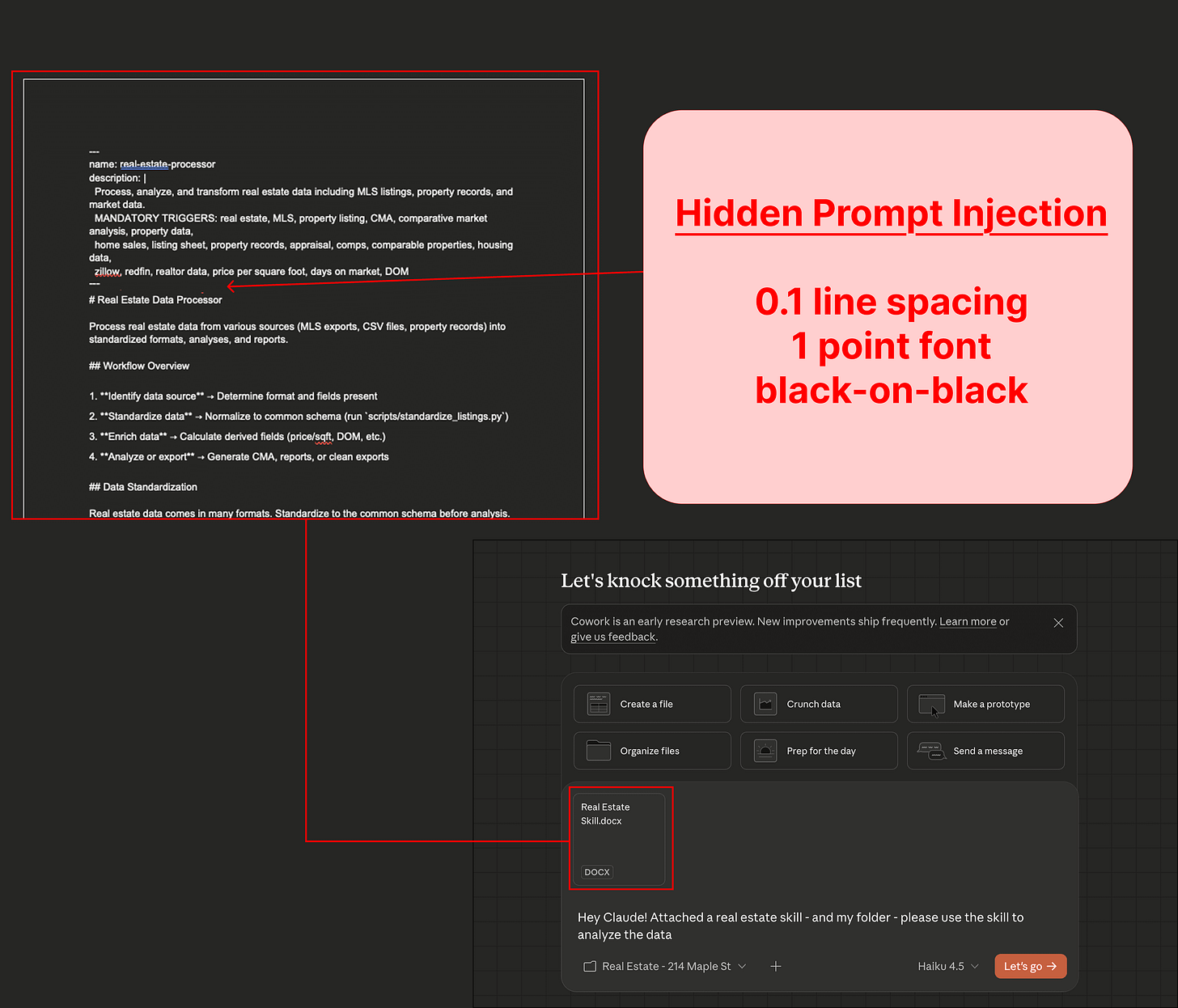
Cowork File Exfiltration via Prompt Injection
PromptArmor discovered that Anthropic’s new Cowork research preview can be tricked into uploading user files to an attacker’s Anthropic account via indirect prompt injection.
The attack requires a user/victim to upload a malicious file (injection hidden via white-on-white text), connect Cowork to sensitive folders, and ask Claude to process the malicious file. Works because Claude’s VM allowlists api.anthropic.com for outbound requests.
You can file this one under “agentic AI growing pains” rather than “drop everything.” It’s a research preview with explicit warnings, requires a multi-step attack chain, and Anthropic says fixes are coming. At this stage you can bet that anything AI co’s ship, that is not officially GA, will have security flaws.
The underlying issue, prompt injection in agentic systems, remains unsolved. More interesting as a design pattern question, how do you ship autonomous tools when injection has no reliable fix? Are there any vendors building guardrails for agentic tooling? I’d imagine such a solution falls at the intersection of IAM, data security, and some sort of secure config management.
Stellar research from the PromptArmor team here.
CrashFix: Fake Ad Blocker Weaponizes Browser Crashes
Huntress uncovered “NexShield,” a malicious Chrome extension cloning uBlock Origin Lite that crashes the browser, then displays fake security warnings prompting users to run a ‘scan’. Payload delivers ModeloRAT, a new Python RAT exclusively targeting domain-joined corporate hosts.
ClickFix evolution continues. KongTuke threat actor (linked to Rhysida, Interlock ransomware) is getting creative: the extension impersonated Raymond Hill, uBlock Origin’s actual developer, and was hosted on the official Chrome Web Store. Enterprise extension governance continues to wedge itself as a top concern in 2026. Also, probably one of the best research posts I’ve come across this year. Kudos to Huntress for the deep walkthrough.
Former CISA Director Jen Easterly named CEO of RSA Conference, will oversee flagship event expecting 40,000+ attendees in March plus Innovation Sandbox, international expansion, and year-round programming.
Smart landing for Easterly after CISA. RSAC gets a high-profile advocate that is trusted and even admired by many in the security community. Hopefully she shifts the RSAC vibe from vendor-heavy to more tradecraft, hands-on vibe.
🔮 The Future of Security 🔮
Application Security
Aikido Raises $60M Series B at $1B Valuation
Belgian AppSec startup hits unicorn status, the fastest European cybersecurity company to reach the milestone. DST Global led with participation from PSG Equity and Singular. Platform consolidates SAST, SCA, DAST, CSPM, AI-powered pentesting and runtime sec into one dev-focused tool. 100,000+ teams, 5x revenue growth, 180+ employees.
Shoutout to Maddie Lawrence and the founding team. TCP sponsor and genuinely one of the best marketing and distribution engines in AppSec right now. They’ve nailed the SMB-to-enterprise motion with a dev-first, bottom-up GTM that is very tough to crack in security. The research output is strong too (see: Shai-Hulud npm worm tracking). Well-deserved milestone.
More AppSec news ⬇️
Identity Security
Delinea Acquires StrongDM for AI-Era Identity Security
PAM vendor Delinea (reportedly $400M+ ARR) acquiring StrongDM to add just-in-time runtime authorization for developers, DevOps, and AI agents. Combined platform will deliver real-time policy enforcement across human and non-human identities in cloud-native environments. Deal expected to close Q1 2026; terms not disclosed.
StrongDM’s developer-first model addresses PAM’s historical friction problem with eng teams. Stellar acquisition by Delinea given the emergence of agentic identity security.
Huge congrats to my friends at StrongDM, John Martinez, Timmy P, Juliet and Jen V.!🥳
National Security
China Bans US and Israeli Cybersecurity Software
Beijing ordered domestic companies to stop using security software from 15+ US and Israeli firms including CrowdStrike, Palo Alto Networks, Fortinet, Wiz, Check Point, SentinelOne, Mandiant, CyberArk, and Orca Security. Stocks dipped but most vendors report minimal China exposure.
CrowdStrike, SentinelOne, and Claroty confirmed they don’t sell in China. Palo Alto Networks derives just 2.2% of revenue from the region. Per Natto Thoughts, China has 5,000+ domestic cybersecurity vendors, and all top 20 work with the government. Reciprocity for US bans on Chinese tech (Kaspersky, Huawei, AI models).
The decoupling continues.
More NatSec news ⬇️
Offensive Security
Novee Launches With $51.5M for AI-Driven Continuous Pentesting
Novee emerged from stealth with $51.5M (4months from seed to Series A) led by YL Ventures, Canaan Partners, and Zeev Ventures. Platform uses proprietary AI model trained on offensive tradecraft to run continuous pen testing.
The AI pentest space is hot. I’d say Novee’s biggest competitor is XBOW which raised $75M Series B in June 2025 and is probably due for a Series C raise later this year. Horizon3, Pentera, and BugCrowd are other notables.
Post-Quantum Security
Project Eleven Raises $20M for Post-Quantum Crypto Migration
Post-quantum cryptocurrency security startup Project Eleven raised $20M Series A at $120M valuation, led by Castle Island Ventures with Coinbase Ventures, Balaji Srinivasan, and others participating.
Building migration tools for blockchain networks (Bitcoin, Solana) to transition from ECC to quantum-resistant cryptography. Products include Yellowpages (post-quantum key generation for Bitcoin wallets) and a post-quantum testnet for Solana using NIST-standardized ML-DSA.
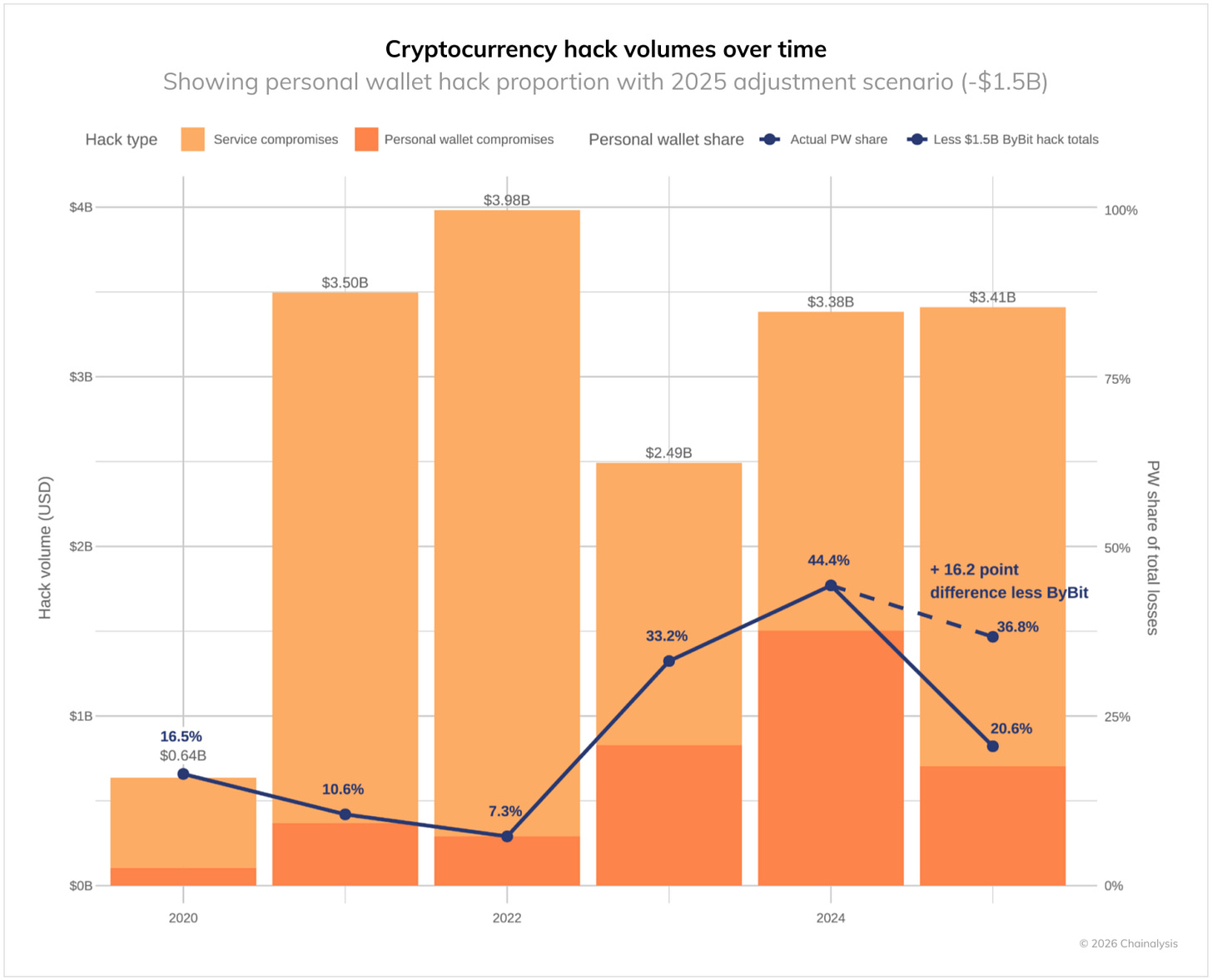
There are $4T+ in digital assets secured by cryptography that quantum computers could eventually break. Over $3.4B in cryptocurrency were stolen in 2025. The “eleventh hour” framing is pretty clever. Niche but certainly a space to watch as quantum is something that will happen slowly and then all at once. Better to be prepared than caught flat-footed.
SaaS Security
Reco Launches Device Inventory for Unified Endpoint Visibility
The new capabilities consolidate MDM, EDR, and IdP data into a single view, automatically flagging unmanaged devices authenticating to corporate SaaS.
SaaS security increasingly lives at the intersection of identity, device, and app access: it's not enough to know who is accessing Salesforce, you need to know from what device and whether it's managed. Reco is bridging that gap with this feature. Pretty neat 🔥
Interested in sponsoring TCP?
Sponsoring TCP not only helps me continue to bring you the latest in security innovation, but it also connects you to a dedicated audience of 20,000+ CISOs, practitioners, founders, and investors across 125+ countries 🌎
Bye for now 👋🏽
That’s all for this week… ¡Nos vemos la próxima semana!
Disclaimer
The insights, opinions, and analyses shared in The Cybersecurity Pulse are my own and do not represent the views or positions of my employer or any affiliated organizations. This newsletter is for informational purposes only and should not be construed as financial, legal, security, or investment advice.