TCP #115: Venezuela Cyberattack, AI Security's Friction Paradox, MongoBleed, and More
What's hot in security🌶️ | Dec. 11th, '25 - Jan. 7th '26
Welcome to The Cybersecurity Pulse (TCP)! I'm Darwin Salazar, Head of Growth at Monad and former detection engineer in big tech. Each week, I bring you the latest security innovation and industry news. Subscribe to receive weekly updates! 📧
The World’s Fastest Security Data Lake
Scanner is a hyper-fast Security Data Lake platform built for AI agents and modern security teams.
Search across petabytes in seconds. Retain all logs forever at a fraction of SIEM costs. Power the next generation of detection & response. Automate SecOps with Agentic AI. Deploy in a day. Trusted by Ramp, Lemonade, Benchling and more.
Want to sponsor the TCP newsletter? Learn more here.
Howdy! Hope your year has been off to a great start! 🤗
While I didn’t manage to get much downtime over the break, I did get to experiment with a few new AI tools + capabilities. All I’ll say is that Claude > everything else and their Chrome Extension is preeeeeetty neat.
I also shipped two blog posts:
AI in Security: Lessons from 2025 and What’s Next - Highlights AI impact on the attack + defense side w/ real-world data points + incidents.
The Best of The Cybersecurity Pulse — 2025 Edition - Last year was our biggest year so far. 250K+ visits to our Substack and 750K+ impressions on LinkedIn. Huge thanks to everyone who opens TCP every week and shares our content + huge shoutout to our sponsors ❤️
Also, we’re hiring for a Head of Marketing at Monad. This role would be working closely with me! DM me here or on LinkedIn if you’re interested.
In any case, a ton has taken place since our last TCP weekly so let’s get to it!
TL;DR 📰
🇻🇪 US cyber op paved way for Maduro extraction — Trump confirmed “certain expertise” knocked out Caracas power during Maduro extraction
🔓 MongoBleed actively exploited — CVE-2025-14847 leaks heap memory pre-auth; 87K+ servers exposed, patch now
🤖 NHIcon 2026 on Jan 27 — Virtual event on agentic AI security with veteran CISOs and practitioners
⚡ n8n drops three critical RCEs — CVSS 10.0 and two 9.9s in a month; rotate secrets if you ran vulnerable versions
🎯 Joshua Saxe on AI security's "friction paradox" — Perfect controls get bypassed; "good enough" security that ships beats elegant models nobody uses
🎀 Hacktivist nukes Nazi sites at 39C3 — Pink Power Ranger deletes three white supremacist platforms live onstage
📊 SANS Detection Engineering survey live — Practitioners: put your DE opinions on record
📋 CISO Tradecraft drops 12 free templates — Budget prioritization, AI control matrices, tool murder boards
☁️ Palo Alto inks ~$10B Google Cloud deal — Prisma AIRS, VM-Series, SASE integration as Wiz acquisition passes DOJ
🏦 Vega hits $700M valuation — $120M Series B for the SIEM challenger. Key company to watch in 2026.
🐳 Docker hardened images now free — 1,000+ minimal containers under Apache 2.0
🔮 M&A rumors flying — Cisco may be eyeing Axonius (~$2B), PANW eyeing Koi (~$400M)
⚒️ Picks of the Week ⚒️
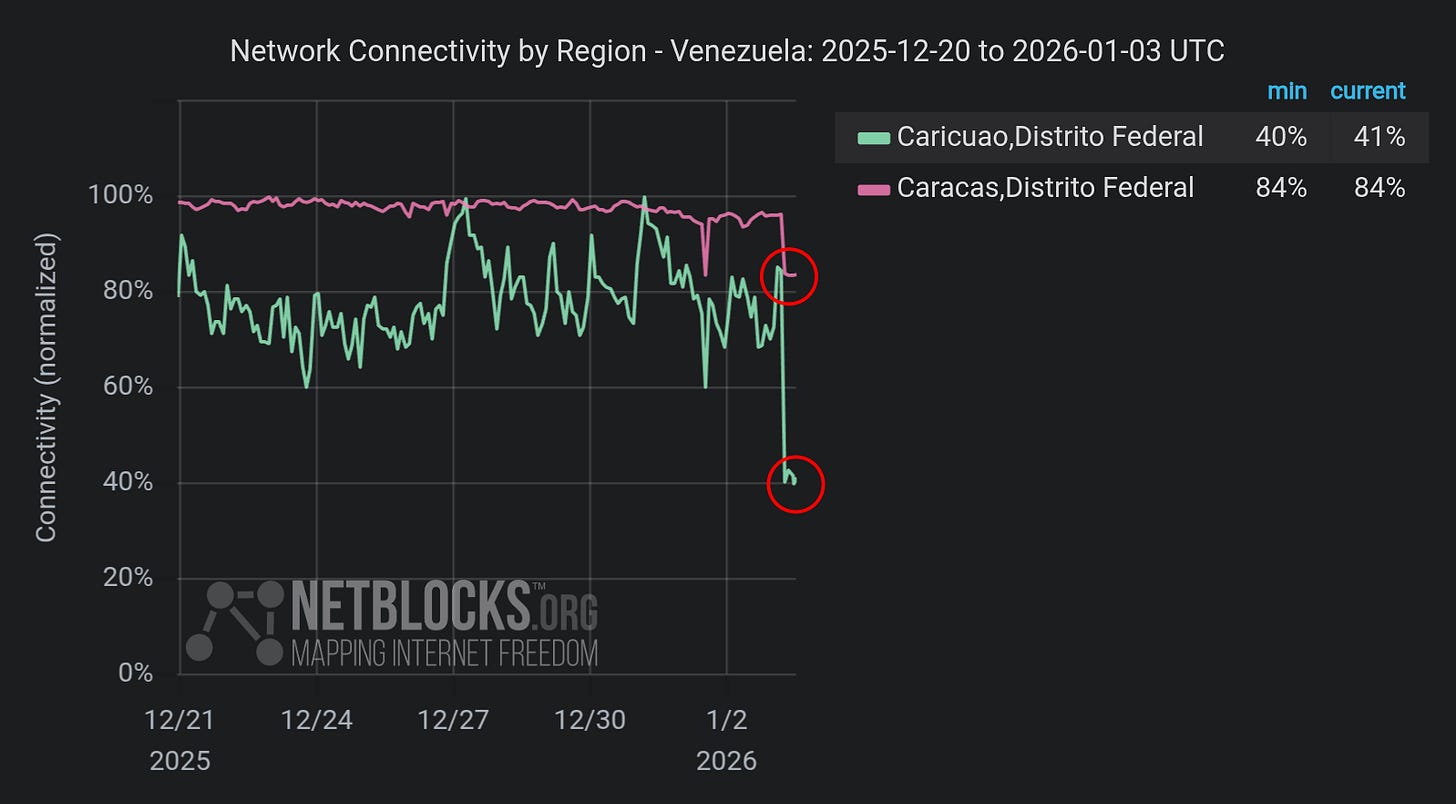
US Cyberattack Was Part of Venezuela Operation
Politico flags what many lay folks may have missed around the Venezuela operation this past week. During the Maduro extraction, Trump stated “the lights of Caracas were largely turned off” due to “certain expertise that we have.”
This strongly indicates a coordinated cyber operation against Venezuela’s electrical grid, likely targeting SCADA systems at Guri Dam, which provides roughly 70% of the country’s power.
The blackout degraded visual acquisition for MANPADS (Man-Portable Air-Defense Systems) operators (making low-flying helicopters harder to target), disrupted military communications that relied on civilian infrastructure, and induced widespread chaos during the critical insertion window. BGP anomalies during the blackout have been documented in public datasets, providing external evidence of network manipulation.
The Stuxnet precedent against Iran was covert and deniable for years. This was essentially confirmed by the President within hours.
There’s a ton of geopolitical turbulence across the globe today and I imagine we’ll see even more aggressive cyber ops used against critical infra in the very near future. As someone who studied national security in grad school, this is both exciting and scary because the reality is that it could happen anywhere.
Trying to make sense of agentic AI security?
NHIcon 2026 on Jan. 27 is a practitioner-driven virtual event focused on what changes as software becomes autonomous. Veteran CISOs, security teams, engineers, and educators share what’s breaking, what’s changing, and how they’re dealing with it in real environments.
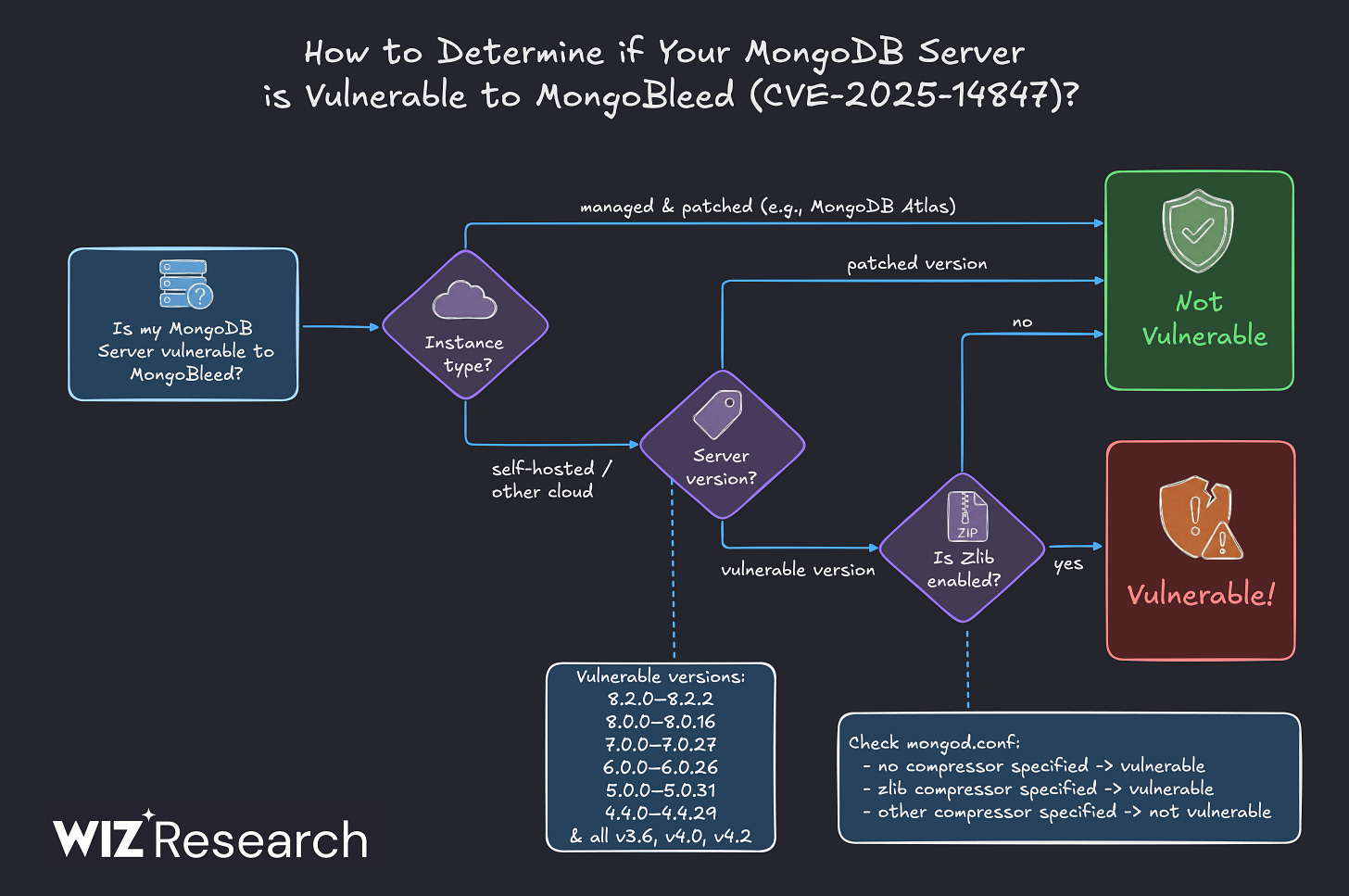
MongoBleed Is Being Actively Exploited: 87K+ Servers Exposed
Think Heartbleed, but for MongoDB. CVE-2025-14847 (CVSS 8.7) lets unauthenticated attackers leak heap memory via malformed zlib-compressed packets: plaintext passwords, AWS keys, API secrets, user data. The bug has been in the codebase since 2017 (version 3.6.0+). PoC dropped December 26, exploitation started December 29, CISA added it to KEV the same day. Censys found 87,000+ exposed instances; Wiz says 42% of cloud environments have at least one vulnerable MongoDB server. A new GUI exploitation tool makes this trivial. Patch to 8.2.3, 8.0.17, 7.0.28, 6.0.27, 5.0.32, or 4.4.30. If you can’t patch, disable zlib compression. Rotate credentials regardless.
This one’s bad. Pre-auth, trivial to exploit, POC publicly available, and the vuln has been there for nearly eight years. Detection is tricky too since it only shows up in MongoDB logs, which almost nobody ships to their SIEM. Eric Capuano put out a solid Velociraptor artifact for hunting this, and Florian Roth built a detector tool. This Wiz post provides a great deep dive + actions teams should be taking.
n8n Critical RCE Vulnerabilities: Three in a Month
n8n just disclosed CVE-2026-21877, a CVSS 10.0 RCE affecting both self-hosted and cloud deployments. Under certain conditions, authenticated users can execute untrusted code on the n8n service, resulting in full instance compromise. The flaw affects versions >= 0.123.0 through < 1.121.3. Fixed in version 1.121.3 (released November 2025). If you can’t patch immediately, disable the Git node and restrict access for untrusted users.
This follows two other critical RCEs in recent weeks:
CVE-2025-68668 (CVSS 9.9): Sandbox bypass in Python Code Node (Pyodide). Authenticated users with workflow permissions can escape the sandbox and execute arbitrary OS commands. Affects 1.0.0 through 1.x. Fixed in 2.0.0 with task runner-based Python implementation.
CVE-2025-68613 (CVSS 9.9): Another code execution vuln dropped late December.
Supply Chain Implications
Full instance compromise here is particularly nasty because n8n workflows typically store credentials for every connected service: API keys, database strings, cloud provider creds, OAuth tokens. Depending on how n8n does their secrets handling, an attacker could get all of them in one shot.
Three critical RCEs (two at 9.9, one at 10.0) in about a month is nothing to scoff at. The risk profile mirrors CI/CD compromises like CircleCI and CodeCov: automation platforms are trust anchors with broad access and stored secrets. If you’ve been running vulnerable versions, assume credential exposure and rotate secrets for any service n8n touched. Audit workflow modification history for signs of tampering etc. Upgrade to 2.0.0+ immediately.
Hacktivist Nukes White Supremacist Sites Live at 39C3
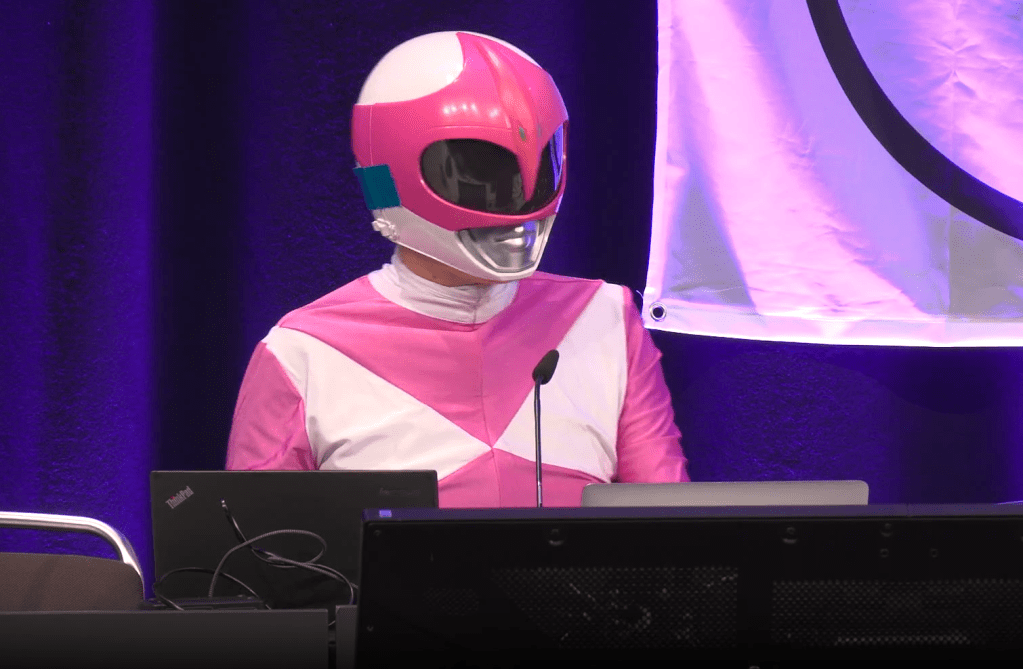
A hacktivist called “Martha Root” (dressed as the Pink Power Ranger) deleted three white supremacist websites live onstage at Chaos Communication Congress: WhiteDate (Nazi Tinder), WhiteChild (supremacist donor matching), and WhiteDeal (racist TaskRabbit). All remain offline. Root infiltrated using AI chatbots verified as “white,” scraped data, found images with precise geolocation metadata, then wiped the servers during the talk. 6,500+ user profiles leaked (86% male). DDoSecrets has the full 100GB dataset for verified researchers. The admin confirmed the hack on X, calling it “cyberterrorism.”
Many wild stories this week, but this one is certainly top 3. Crazy times we are living in.
CISO Tradecraft: 12 Free Cybersecurity Templates
CISO Tradecraft released a Christmas gift pack of 12 free templates for security leaders. Highlights include:
9 Box Template: Map security projects by Impact vs. Effort for budget prioritization
CMMC Reference Guide: All three levels with at-a-glance control explanations
AI Control Matrix & Questionnaire: Based on CSA AICM v1.0.3, with automated risk scoring and compliance dashboards
Cybersecurity Tools Murder Board: Framework for evaluating which tools to retire
GenAI Risk Assessment: Based on California’s SIMM 5305-F
Toil Register: Track manual work and tech debt with risk levels and remediation priorities
Templates available at https://www.cisotradecraft.com/freetemplates
Great practical tools for security leaders doing the not-so-sexy work of budget justification, vendor rationalization, etc. Assets like these are massive unlocks as they force leaders to reflect and optimize across many of the ‘people, process, technology’ layers.
Palo Alto Inks Multibillion-Dollar Google Cloud Deal
Palo Alto Networks and Google Cloud announced a “multibillion-dollar” partnership, with Reuters reporting Palo Alto will pay Google nearly $10B over multiple years.
Key integrations: Prisma AIRS protecting GCP AI workloads (Vertex AI, Agent Engine), VM-Series firewalls with deep GCP integration, and Prisma SASE running on Google’s network. Palo Alto will power its copilots using Vertex AI and Gemini.
Timing is notable: Google’s $32B Wiz acquisition cleared DOJ in November and Wiz was PANW’s biggest cloud security competitor.
Imo, Google is hedging: Wiz gives them native CNAPP, but Palo Alto fills gaps in network security, SASE, and AI workload protection. More importantly, enterprises with existing Palo Alto deployments aren’t switching overnight. Google needs that bridge to sell GCP. I imagine there will be a few awkward product overlap convos post-Wiz, but too much revenue at stake for competitive tensions to derail it.
Overall positive for the industry.
2026 SANS Detection Engineering Survey Is Live ⚡
SANS and Anvilogic are running the detection engineering survey again, and if you’re in the trenches doing DE work, it’d a great service to the industry for you to take it. You can access it here.
Last year’s report had a ton of valuable findings and insights from top DE voices including: 80% of orgs investing in DE, and confirmation that nearly half of SOCs still can’t get access to the data they actually need. The threat modeling and data engineering skills + tooling gaps were called out hard, and honestly, I don’t think much has changed.
I may be biased since I contributed to last year’s report but these practitioner surveys are one of the few places we get real signal instead of vendor narratives. If you’re a practitioner and you’ve got opinions on where DE is headed, this is your chance to put them on record.
Rumor Mill: Cisco and Palo Alto Networks
The year certainly started off with some M&A rumor fireworks. Cisco is rumored to be in talks to acquire Axonius for ~$2B (Axonius has denied). Meanwhile Palo Alto Networks is rumored to be eyeing an acquisition of KOI security (~$400M). Both would be very synergistic for the acquiring co’s in my opinion. I’ll be ‘monitoring the situation’ and cover anything else that arises here. Rumors for now they say….
🔮 The Future of Security 🔮
AI Security
Palo Alto Networks Joins NVIDIA Enterprise AI Factory Validated Design
Prisma AIRS now part of NVIDIA’s Enterprise AI Factory validated design, running on BlueField DPUs. The architecture offloads security processing to the DPU, freeing 100% of host compute for AI workloads while maintaining real-time threat detection. Telemetry feeds into Cortex XSIAM.
More AI security news ⬇️
Banger post on the "friction paradox" in AI security: the more academically beautiful and complete your security controls, the more likely users bypass them entirely. The result is zero security impact.
AI Security Firm Ciphero Emerges From Stealth With $2.5 Million in Funding
Identity and Access Management
Wiz Adds Oracle Cloud IAM to Unified Identity Graph
Wiz now pulls OCI IAM into the same security graph used for AWS, Azure, and GCP. OCI’s quirky constructs (Identity Domains, Compartments, natural-language policies) get normalized into a queryable cross-cloud model. Surfaces users, groups, service principals, API keys, permission paths, plus the usual: unrotated keys, overly broad groups, missing MFA.
SaaS Security
SaaS-to-SaaS Connections: The OAuth Scope Blind Spot Most Teams Miss
This post from Reco highlights some of the biggest security issues with OAuth. The Salesloft-Drift breach from earlier this year is a good example of what happens when these get ignored.
Every time a user clicks “Allow,” those permissions persist indefinitely, often granting read/write access far beyond what’s needed
Dormant apps retain active tokens long after anyone stops using them
A compromised plugin with cross-platform OAuth access can create lateral movement paths between apps (Slack → Google Workspace) through completely unmonitored tunnels
AI agents and MCP add another layer: non-human identities with high privilege spanning multiple SaaS platforms, no HR visibility, no natural offboarding trigger, and nobody reviewing the permissions they’re requesting
We’re still early in figuring out how to secure agents and MCP, but SaaS security tools are well-positioned to help solve some of these risks.
Security Operations
Vega Raises $120M Series B, Hits $700M Valuation
In December, Vega closed a $120M Series B led by Accel, hitting a $700M valuation (up from $400M three months ago). Total raised: $185M.
Vega challenges traditional SIEMs by analyzing data in place without forced migration.
Congrats to the Vega team! Genuinely great humans + sponsors of TCP. Two years in, $700M valuation, $185M raised. The “analyze in place” pitch resonates because SIEM migration is genuinely painful. Strong company to watch.
More SecOps news ⬇️
Supply Chain Security
Docker Opens the Hardened Image Vault: 1,000+ Secure Containers Now Free
Docker made its entire catalog of 1,000+ Hardened Images free under Apache 2.0. Images are minimal, rootless, no shell, no package manager. Full SBOMs and SLSA Build Level 3 provenance included. Enterprise tier remains for FIPS/STIG compliance, 7-day critical CVE SLAs, and customization. Timing notable given Bitnami just pulled its free catalog behind a $50K+ paywall.
Docker playing offense, commoditizing secure base images right as Chainguard ($3.5B valuation) and Echo ($50M raised) build businesses around them. Community skepticism is fair given Docker’s track record, but this removes a real barrier.
Vulnerability Management
Gambit Cyber Raises $3.4M Seed for AI-Native CTEM Platform
Dutch startup Gambit Cyber closed $3.4M seed led by Expeditions, with Bitdefender Voyager Ventures participating. Founded 2024, their KnightGuard platform uses coordinated AI agents for vulnerability discovery, validation, and prioritization. Already deployed in financial services, telecom, and critical infrastructure across India, UAE, and Europe.
Interested in sponsoring TCP?
Sponsoring TCP not only helps me continue to bring you the latest in security innovation, but it also connects you to a dedicated audience of 20,000+ CISOs, practitioners, founders, and investors across 125+ countries 🌎
Bye for now 👋🏽
That’s all for this week… ¡Nos vemos la próxima semana!
Disclaimer
The insights, opinions, and analyses shared in The Cybersecurity Pulse are my own and do not represent the views or positions of my employer or any affiliated organizations. This newsletter is for informational purposes only and should not be construed as financial, legal, security, or investment advice.





Thanks for sharing the CISO Tradecraft Templates. Really Appreciate it