TCP #116: Starlink v. Iran, Agents Attack Agents, and CrowdStrike's $1.16B Week
What's hot in security🌶️ | Jan 7th, '25 - Jan. 14th '26
Welcome to The Cybersecurity Pulse (TCP)! I'm Darwin Salazar, Head of Growth at Monad and former detection engineer in big tech. Each week, I bring you the latest security innovation and industry news. Subscribe to receive weekly updates! 📧
Beyond the Quadrant: A Former Analyst’s Real Framework
Drowning in AI vendor claims? A former Gartner analyst reveals her framework for cutting through the noise and building your shortlist. Earn 1 CPE credit.
Howdy! 👋 I hope you’re having a great week!
Feels like there’s a lot in flux across the globe at the moment. Feels like the first two weeks of 2026 have actually been two months for some reason. In any case, we have a lot to get to in this week’s TCP so let’s dive in!
TL;DR 🗞️
🪿 Block deployed infostealer using its own AI agent — Goose used prompt injection + invisible Unicode to deploy infostealer; added recipe warnings and detection
📡 Starlink vs. Iran standoff escalates — 50K-100K smuggled terminals, military-grade jammers spike packet loss to 80%; SpaceX OTA updates cut interference to 10%
🔎 Hackers probing LLM proxies at scale — GreyNoise logged 91K+ sessions; 80K in 11 days targeting 73+ model endpoints across OpenAI, Claude, Gemini, Grok
🎭 BreachForums database leaked — 323,986 user records exposed including emails, hashed passwords, IPs; pure karma
🛡️ Unit 42 drops SHIELD framework — Governance for vibe coding; real incidents already include code injection, auth bypass from AI-gen’d code
🔭 WitnessAI launches Agentic Security — Auto-discovers agents across Claude Desktop, GPT plugins, VS Code; maps MCP server access; raised $58M
🌐 CrowdStrike acquires Seraphic for $420M — Browser runtime security across Chrome, Edge, Safari, Firefox; no enterprise browser required
🔐 CrowdStrike acquires SGNL for $740M — Continuous authorization for human, NHI, and AI agent identities; $1.16B two-week M&A spree
🧬 Cyera hits $9B valuation — $400M Series F led by Blackstone; 3x valuation jump in 6 months; claims 1/5 of Fortune 500
⚡ Torq raises $140M at $1.2B valuation — AI SOC platform reports ~300% revenue growth; customers include Marriott, PepsiCo, Uber
💰 Cybersecurity funding hit $14B in 2025 — 47% increase YoY per Pinpoint; strongest since 2021 peak; investor focus on AI governance + identity
🚀 CrowdStrike accelerator picks 35 startups — AWS + NVIDIA program runs through March; five finalists pitch at RSA Conference March 24
⚒️ Picks of the Week ⚒️
Block CISO: We red-teamed our own AI agent to run an infostealer
Block CISO, James Nettesheim, recently shared how the company’s red team used prompt injection to deploy an infostealer on an employee laptop via Goose, Block’s open source AI agent.
The attack combined phishing with prompt injection hidden in invisible Unicode characters. When a developer clicked a poisoned “recipe” (Goose’s reusable workflow format) to debug a reported bug, it downloaded and executed the malware.
Block has since added recipe install warnings, suspicious Unicode detection, and is experimenting with adversarial AI to validate agent inputs and outputs.
“It’s not enough for self-driving cars to be just as good as humans. They have to be safer and better. We need that with our agentic use, too.”
Love the transparency and tinkering mindset deployed at Block. While AI security improves day by day, it still feels like the wild west at times. Having leadership that encourages this and shares learnings with the community is crucial for advancing AI security. More of this please!!
Don’t Let AI Outpace Security: 10x Your Team’s Efficiency in 2026
At the 2026 Product Security Summit, we’re diving into the Application Security playbooks used by Cloudflare, Schneider Electric, and Alter Domus. Learn to manage AI-driven code velocity and lead your team through the “Great Convergence” with application security strategies that actually work at scale.
Don’t build your 2026 roadmap in a vacuum. Get the real-world blueprints from the leaders doing the work.
Starlink vs. Iran: Satellite Internet Under Electronic Warfare
If you’re a TCP reader, you’re probably tracking what’s unfolding in Iran. While it’s hard to separate noise from signal with media, shit has clearly hit the fan. Iranian regime reportedly killing thousands of civilians over the past week.
I won’t get into the politics, but what’s most relevant for our space is the Starlink vs. Iran standoff. It demonstrates what’s technically possible with satellite jamming, and it will set legal + warfare precedents.
A near-total internet blackout began January 8, leaving 90 million people in darkness. For protestors, Starlink has become the last lifeline, and the regime is deploying countermeasures to kill it.
Professional smugglers are bringing in Starlink boxes across the border from Iraq and Dubai. An estimated 50,000 to 100,000 smuggled terminals are now active in the country. Under a 2025 law, using Starlink is legally equivalent to espionage for the CIA or Israel and carries a potential death sentence.
The regime deployed jammers, likely sourced from Russia or China, targeting Starlink’s GPS and radio frequencies (RF). Packet loss jumped from 30% to over 80% during protest peaks. In response, activist group NasNet worked with SpaceX to push emergency firmware updates, dropping interference from 35% to 10% for users in Tehran.
Security forces are using surveillance drones to spot dishes on rooftops in northern Tehran. Authorities have been rappelling down apartment blocks and raiding homes to seize equipment.
This is a real-time stress test of how resilient and secure satellite constellations are against jamming and other tactics. It’s pretty much a cat and mouse game with SpaceX pushing OTA updates as fast as Iran deploys countermeasures. Would love to geek out on this with some RF and satellite hackers some time. I’d imagine there will be some Starlink hacking at this year’s DEF CON. In any case, this a pretty wild situation currently unfolding and I’d imagine, it’ll only intensify.
Hackers target misconfigured proxies to access paid LLM services
GreyNoise documented 91,403 attack sessions against AI infrastructure between October 2025 and January 2026.
The more concerning campaign started December 28: two IPs generated 80,469 sessions over 11 days, systematically probing 73+ model endpoints across OpenAI, Anthropic, Meta, Google Gemini, Mistral, Alibaba Qwen, DeepSeek, and xAI Grok.
Many companies use a middleman server (proxy) to route employee requests to paid AI services like ChatGPT or Claude. These proxies often store the API keys and handle billing. If poorly secured, attackers can piggyback on your credentials and run up your tab, or worse, access sensitive data flowing through the proxy.
Attackers send innocent-looking prompts (”hi,” “How many states are there in the United States?”) to see which AI model responds. This fingerprinting avoids triggering security alerts while mapping which companies have exposed access.
If you’re running an exposed AI gateway, you’re likely already on someone’s target list. Harden it like any other production API.
Hackers get hacked, as BreachForums database is leaked
BreachForums, one of the biggest cybercrime marketplaces, had its entire user database leaked. The dump includes 323,986 user records: usernames, email addresses, password hashes, and IP addresses. The exposed database could hand law enforcement new leads for investigations. Pure karma.
CrowdStrike, AWS, and NVIDIA 2026 Cybersecurity Startup Accelerator Cohort
CrowdStrike, AWS, and NVIDIA announced 35 startups for the third annual Cybersecurity Startup Accelerator. The eight-week program runs through March 3, 2026, with five finalists pitching at RSA Conference on March 24. The winner gets investment from CrowdStrike’s Falcon Fund.
Notable names in the cohort: Averlon, Aira Security, Capsule Security, Haleum AI, Simbian AI, and SurePath AI.
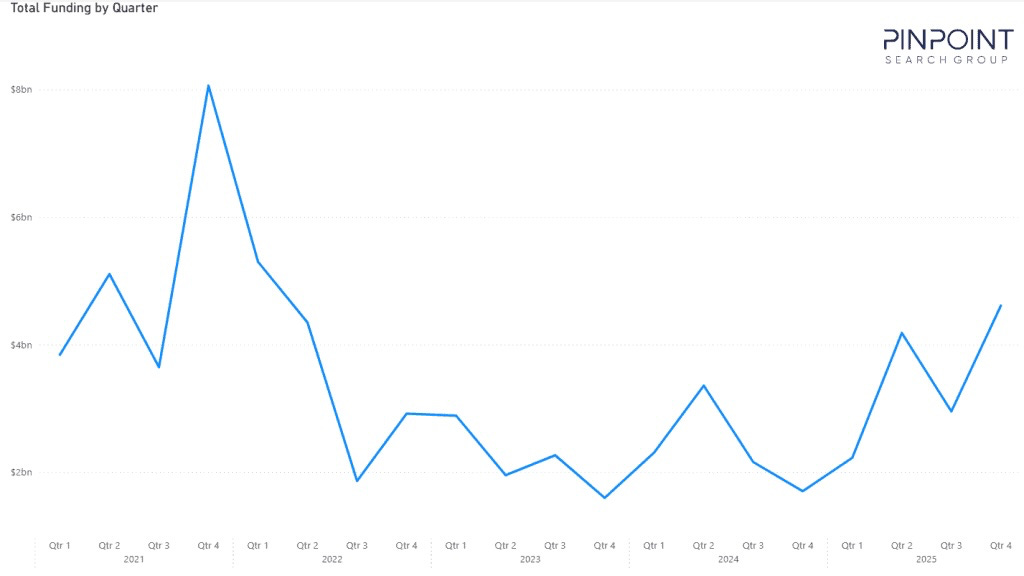
Cybersecurity Firms Secured $14 Billion in Funding in 2025: Analysis
Pinpoint Search Group reports cybersecurity vendors raised $13.97B across 392 funding rounds in 2025, a 47% increase from 2024’s $9.5B. This marks the strongest funding year since the 2021 peak of $20.6B.
Largest rounds: Saviynt ($700M), Cyera ($540M), Armis ($435M), Chainguard ($280M), Vanta ($150M), 7AI ($130M), Noma Security ($100M), Dream ($100M).
Investosr focused heavily on AI governance and identity. The post-2021 correction is officially over. Capital is flowing again… but for how long?
🔮 The Future of Security 🔮
AI Security
WitnessAI Extends Its LLM Protections to AI Agents
WitnessAI launched Agentic Security which auto-discovers agentic activity across Claude Desktop, ChatGPT with plugins, VS Code extensions, and local frameworks (LangChain, CrewAI, AutoGPT), maps MCP server access, and links agent actions back to the humans who initiated them.
This is pretty neat as most teams still have little/no visibility into what their agents are actually doing and what permissions+access they have. A single malicious prompt can cascade through tool calls, API requests, and db queries before a human notices.
WitnessAI also announced fundraising of $58M in a strategic round yesterday.
Application Security
Unit 42 Introduces New Vibe Coding Security Governance Framework
Palo Alto’s Unit 42 published a governance framework for securing vibe coding after identifying real-world incidents including data breaches, code injection, and auth bypass attacks tied to AI-generated code.
SHIELD controls:
Separation of duties (no AI agents with dev + prod access)
human-in-the-loop code review before merge
input/output validation via guardrails and SAST
security-focused helper models
least agency permissions
defensive controls like SCA and disabled auto-execution
Solid framework, but the friction paradox applies here as well. Much vibe coding happens on personal devices and shadow IT that enterprise controls don’t touch. If the security controls introduce too much friction, users will just avoid them.
In any case, this is a must read for anyone securing code in 2026.
Browser Security
CrowdStrike to Acquire Browser Security Firm Seraphic for $420 Million
CrowdStrike is acquiring browser runtime security startup Seraphic Security for $420M, following last week’s $740M SGNL deal bringing their two-week M&A spend to $1.16B.
Seraphic works within the browser runtime across Chrome, Edge, Safari, and Firefox without forcing users onto a proprietary enterprise browser. They randomizes the browser’s JavaScript engine at the execution layer to disrupt session hijacking, prevent memory-based attacks, and block man-in-the-browser exploits. It also provides granular DLP by controlling actions like copy-paste and file uploads.
This is an absolutely stellar pick up by CrowdStrike as they continue to expand their platform efforts to go toe to toe with Palo Alto Networks. I also love the angle that Seraphic takes in securing any browser vs. forcing users onto a new one like Island or Talon (now PANW) does. User friction is often a huge trade-off in security
Data Security
Cyera hits $9B valuation six months after being valued at $6B
Cyera closed a $400M Series F led by Blackstone, hitting a $9B valuation just six months after raising $540M at $6B. Total raised now exceeds $1.7B.
Enterprise AI adoption has led to a massive surge in need for data security that can keep up with the speed of AI. I wrote a piece on this last summer and most, if not all of it, still holds true today.
More data security news ⬇️
Identity and Access Management
CrowdStrike to Buy SGNL to Expand Identity Security Capabilities
CrowdStrike has acquired identity security startup SGNL for $740M. SGNL provides continuous, context-aware authorization that grants and revokes access in real-time based on risk signals. This is huuuuuge for agentic identity security.
CrowdStrike already covers endpoint, cloud and SaaS with capabilities that have come from past acquisitions (i.e., Adaptive Shield and Preempt Security).
SGNL had raised $42M from Costanoa Ventures, CRV, and others. Founded 2021 by ex-Googlers Scott Kriz and Erik Gustavson.
Massive win for CrowdStrike, imo.
Security Operations
Torq Raises $140 Million at $1.2 Billion Valuation
Torq closed a $140M Series D led by Merlin Ventures, hitting $1.2B valuation and $332M total raised. The company reported ~300% revenue growth in 2025.
Pretty cool to see Torq’s “agentic SOC” pitch landing well w/ investors and customers given that up until recently they were a pure-play SOAR solution.
Interested in sponsoring TCP?
Sponsoring TCP not only helps me continue to bring you the latest in security innovation, but it also connects you to a dedicated audience of 20,000+ CISOs, practitioners, founders, and investors across 125+ countries 🌎
Bye for now 👋🏽
That’s all for this week… ¡Nos vemos la próxima semana!
Disclaimer
The insights, opinions, and analyses shared in The Cybersecurity Pulse are my own and do not represent the views or positions of my employer or any affiliated organizations. This newsletter is for informational purposes only and should not be construed as financial, legal, security, or investment advice.